What is a Linux Firewall?
A Linux firewall is a device that inspects Network traffic ( Inbound /Outbound connections ) and makes a decision to pass or filter out the traffic. Iptables is a CLI tool for managing firewall rules on a Linux machine.
Network Security evolved with different types of Linux firewalls in the era. Traditional packet-filtering firewalls deal with Routing and filtering packets ( OSI Layers 3 and 4 ), Where else NGFWs will work with additional functions as with OSI layers ( L4-L7 of OSI model ).
What is Iptables? How does it work?
Iptables is a CLI ( Command-line interface ) application that allows the administrator to configure specific rules that will enforce the Linux kernel ( Netfilter framework) to perform an action such as inspect, modify or drop network packets. Enabling these Iptables in any Linux machine or device will be acting as a Network Firewall and/or a router.
Different kernel modules and programs are used for different protocols; IPtables apply to IPv4, ip6tables to IPv6, ARP tables to ARP, and ebtables to Ethernet frames.
Later Netfilter Project developed Nftables for performance and scalability. This is a packet filtering framework that does the same work of Iptables.
How Does Packet Filtering Work with Iptables?
An iptables policy is built with an ordered set of rules, which describe to the kernel the actions that should be taken against certain types of packets.
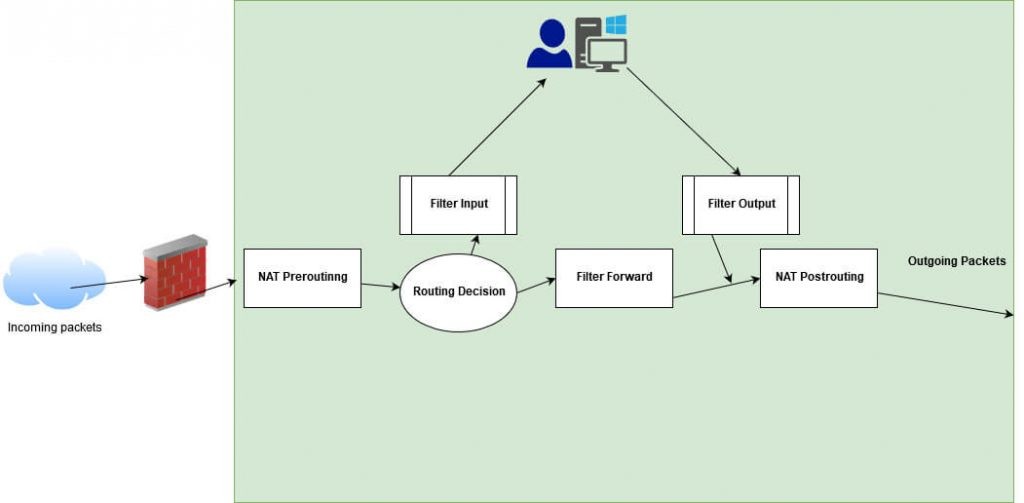
Tables Overview
Iptables functionality is classified into Four tables which are NAT table, packet filtering table, Mangle table, and Raw table.
NAT Table:
- Network Address Translation ( NAT ) is processed for incoming packets and outgoing packets with routing decisions in the table.
- Network Routing is processed with Pre-routing and Post-routing of packets from origination to destination.
Also: Threat Hunting using Firewall Logs – Soc Incident Response Procedure
Packet Filtering Table:
Packet filtering is processed with the below chain rules.
Chains:
- Chains are classified into 3 types INPUT CHAIN, OUTPUT CHAIN & FORWARD CHAIN.
- Input Chain – Incoming connections which are traversed from Prerouting. Example: External IP trying to establish an SSH connection on your system.
- Output Chain- Packets that are passed or outgoing connections from your system. Example: If you’re trying to visit socinvestigation.com, user traffic is verified in chain rule to allow or deny the connection.
- Forward Chain – Forwarding connections to specific networks or ports.Example: Port Forwarding.
Mangle table
- The mangle table can be used for the special-purpose processing of packets.
- It includes a Combination of NAT Tables & Chains.
Raw table
- Raw tables are used only for packets processed with special conditions, such as exempt from connection tracking.
Matches:
Every iptables rule has a set of matches that tells the iptables what to do with a packet.
–source (-s) source IP address or network
–destination (-d) Destination IP address or network
–protocol (-p) IP value
–in-interface (-i) Input interface (e.g., eth0)
–out-interface (-o) Output interface
–state connection states
–string sequence of application layer data bytes
Target:
ACCEPT – Allows a packet. ( Accept the incoming/outgoing connection )
DROP – Drops a packet. ( Drop the connections )
LOG – Logs a packet to Syslog. ( Log the connection status for network monitoring, TCP Built/teardown )
REJECT – Drops a packet sends an appropriate response packet (TCP Reset or an ICMP Port Unreachable message).
RETURN- Continues processing a packet within the calling chain.
Blocking Attacks with IPtables:
Let’s write a simple rule to block & allow ICMP probs.
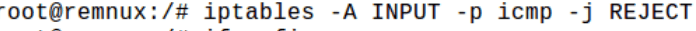
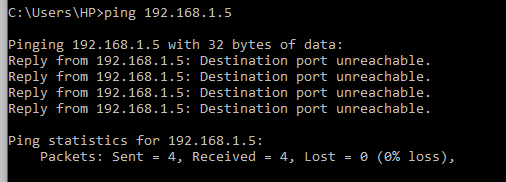
Yes, it worked. It has blocked all incoming packets with the protocol as ICMP in the network. Now let’s allow the ICMP probs to enter the network.
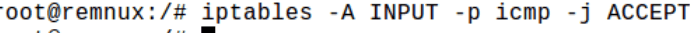
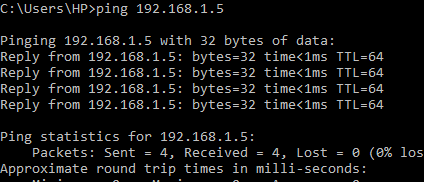
You can also write any customized rule according to your environment, Such as ALLOW traffic over port 1443 or any, protocol and Log those connection logs with the -L parameter.
NOTE: If you are a Pentester /Red team guy, the Iptables Linux firewall can hide some systems in the network as ICMP probs are blocked. But this system can be enumerated and identified in-network with crafted ARP packets. Still, as Defense guys, they can use Arp-tables to stop you.
Also Read: Soc Interview Questions and Answers – CYBER SECURITY ANALYST
Other Simple rules to Try :
Application Layer Defense:
- This will log the connections when any Web clients are trying to access a Web server shadow file path.
iptables -I FORWARD 1 -p tcp –dport 80 -m state –state ESTABLISHED -m string –string “/etc/shadow” –algo bm -j LOG –log-prefix “ETC SHADOW“
Malformed Packets Transport Layer:
- This will DROP and teardown the TCP connections as it is malformed.
iptables -A INPUT -p tcp –tcp-flags ALL NONE -j DROP
Blocking Outbound Emails:
- Block all SMTP outbound connections in the network.
iptables -A OUTPUT -p tcp –dport 25 -j REJECT
Open Source Linux firewall can be used for small-scale business, VPS hosted on third-party clouds and more. Enterprise firewalls also play a similar kind of technique. But it’s good to choose the right Firewalls ( Proprietary/OpenSource ) according to your business needs.
Happy Packet Dropping!