Malware analysis is an essential part in the field of cybersecurity, and many security researchers are now exploring both static and dynamic analysis techniques. Initially, we will start with Static analysis and build a strong foundation for further exploration.
What is static malware analysis?
Static malware analysis is a method of analyzing malware without executing it. It involves examining the malware code, file structure, and behavior in order to identify potential threats and vulnerabilities.
This blog will cover the basics of static analysis and provide an overview of packers, as well as explain why security professionals need to focus on this area. We will also demonstrate how to identify packers through a simple sample test. Let’s begin with a brief introduction.
Packers (aka runtime packers or self-extracting archives) are used to compress a file. In general, packers are used for legitimate purposes to compress the executables which results in reducing disk space, network load times, downloading time, storage or reducing data transmission time and protecting the applications against software piracy.
Later, the malware authors used this technique for anti-debugging, anti-emulation (anti-VM) and code obfuscation. As a result of this, they can hide the payload file and escape from the AV detections. And more efficiently once the packed file is executed, that can unpack itself in memory.
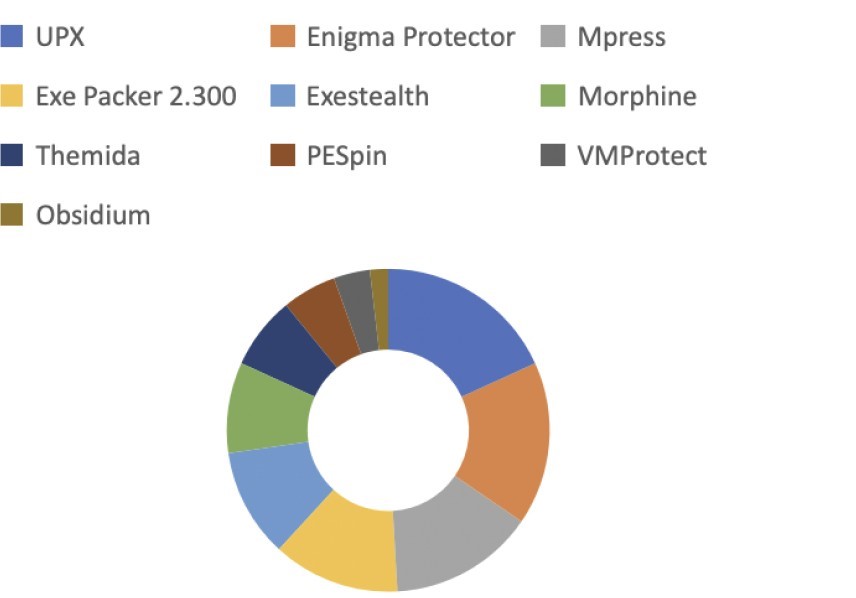
Top 10 Packers are used in malware:
What is Executable compression?
Executable compression is the method of compressing an executable file and combining the compressed data with decompression code into a single executable. Once the compressed executable file is executed, the decompression code recreates the original code from the compressed code before executing it.
A compressed executable can be considered a self-extracting archive, where a compressed executable is packaged along with the relevant decompression code in an executable file. Some compressed executable can be decompressed to reconstruct the original program file without being directly executed.
How to detect the malware packers?
To identify packers, there are a number of packer-detecting tools available. Here’s some of the best tools for identifying malware packers. We can check them one by one.
Malware Packers Identifiers List
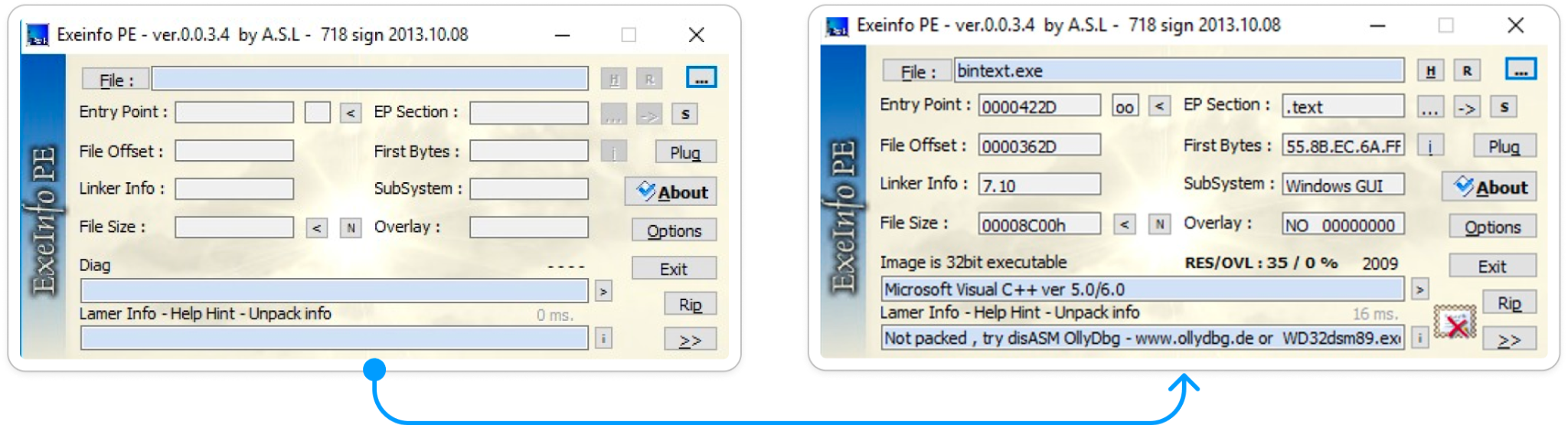
1: Exe-info PE
Exe-info PE is one of the popular tools that will analyze the code to determine if it has been packed. Also, it can identify the type of packer used and more.
Figure:1
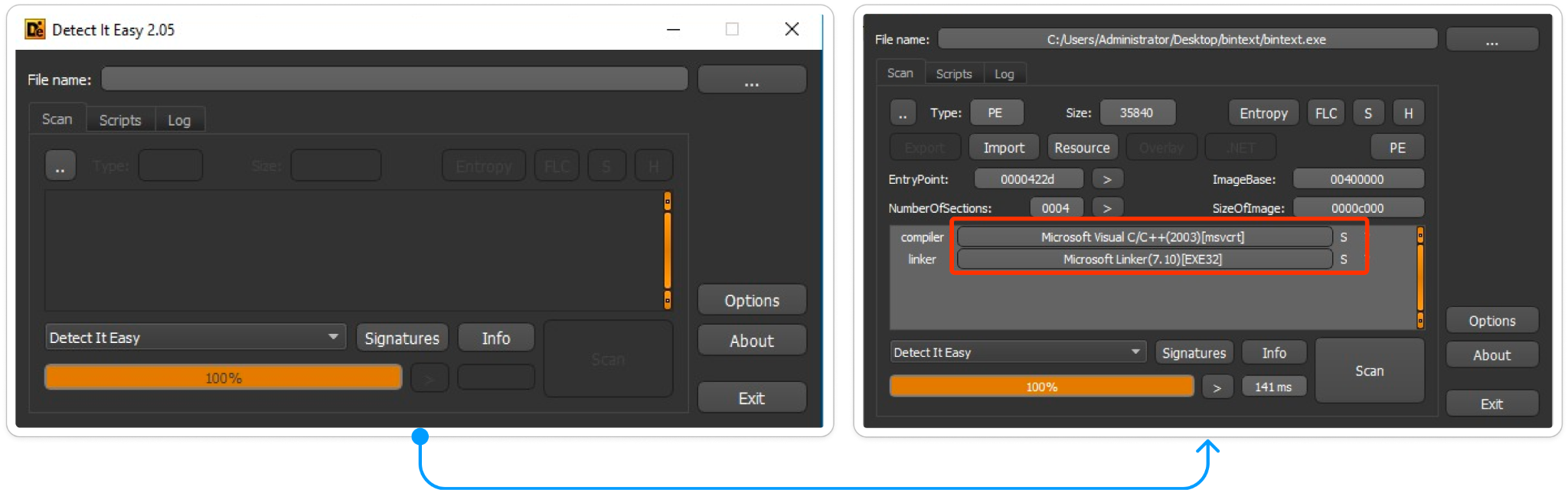
2: Detect-it-easy (DIE)
Detect It Easy is a free cross-platform program to analyze files you load into the application which enclose the file properties such as copyright, signature, the compiler or linker. It supports more than 200 file types such as MSDOS- Executable PE for Windows platform, executable ELF for Linux platform, executable MACH for Mac, text file and the binary file etc.
Figure:2
The aforementioned tools serve as identifiers that enable us to check the file type, compiler name, and other basic details of the sample. By analyzing this information, we can determine the type of packer that was used. Let’s examine one of the most commonly used packers, UPX.
Ultimate Packer for Executables (UPX):
UPX is a free and open-source executable packer supporting several file formats in different operating systems. Using this packer, we can perform both packing & unpacking it. If any of the malware samples were packed using UPX, it is possible to use the in-built command line tool to unpack the malware code and perform further analysis.
Sample Test:
Let’s take any one of the unpacked files, here I have taken bintext.exe for our analysis. Follow the below mentioned 4 steps to perform the action.
Step 1: Download any unpacked sample for testing.
Step 2: Then download upx.exe (https://upx.github.io/) depending upon our platform.
Step 3: Go to the folder path and paste the sample you have.
Step 4: Open command prompt and hit the command below & get the packed file.
Figure:3
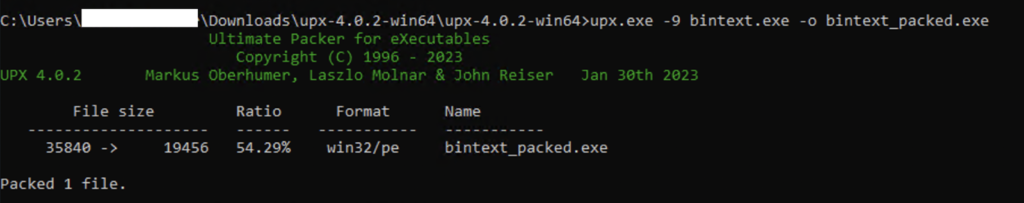
Figure:4
Figure:5
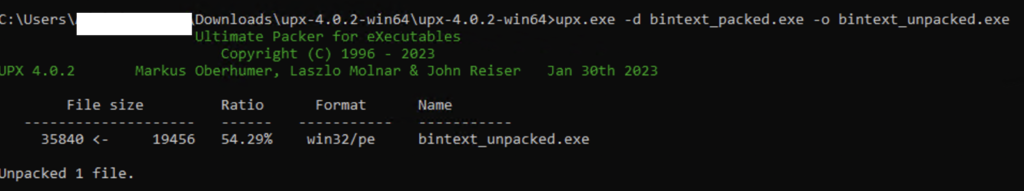
Here’s the cmd to unpack the packed sample. Likewise, we can pack & unpack any of the executable applications.
upx.exe -d bintext_packed.exe -o bintext_unpacked.exe
Let’s take a closer look at how packers work?
When a sample is uploaded to a packer, the packer tool processes the original code and compresses or encrypts the data to protect it.
The packed file consists of:
- New PE header – Which contains executable image and object files.
- Packed section(s) – original code is compressed or encrypted and stored in the packed section of the new executable.
- Decompression stub – used to unpack the code.
- During this process, the original entry point is relocated/obfuscated in the packed section. This is important for anyone trying to analyze the code. This process makes identifying the import address table (IAT) and original entry point difficult.
Figure:6
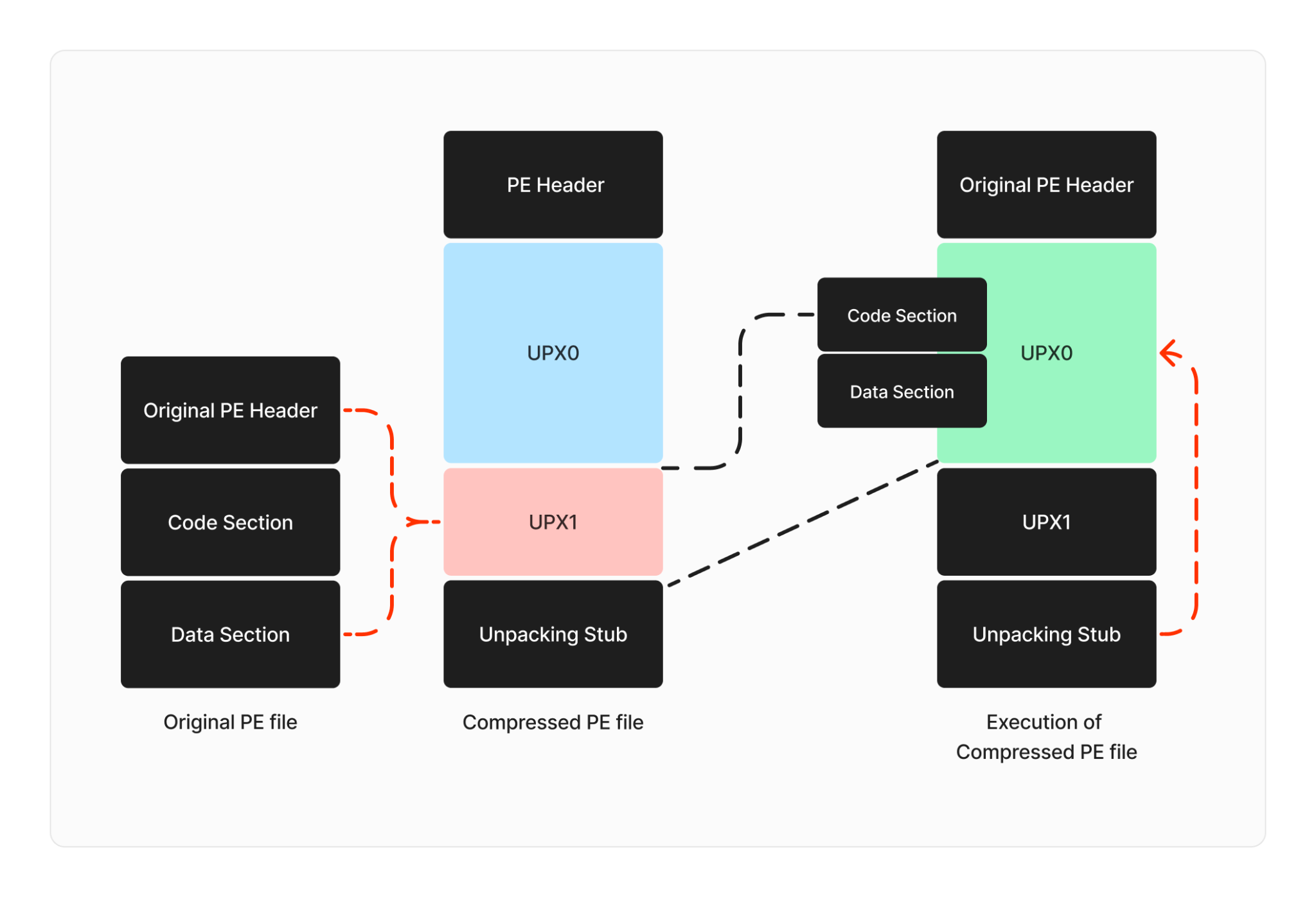
Here a stub is a small portion of code that contains the decryption or decompression agent used to decrypt the packed file.
Final Thoughts:
In short, Packer tools are powerful which are used by adversaries to evade antivirus detection and compromise targeted victim machines. They also make it difficult for security researchers to analyze the code and identify its behavior. Hence we should have safe browsing habits and regular software updates can help educate users on the importance of proactive cybersecurity practices. By remaining vigilant, we can prevent the spread of malware and protect our organizations and ourselves from the devastating impact of cybercrime.
Keep learning and be on the lookout for my next blog!! PD



































