Researchers from Uptycs first reported the discovery of the new Black Basta ransomware variant that supports encryption of VMWare ESXi servers. The move aims at expanding potential targets, the support for VMware ESXi was already implemented by many ransomware families, including cheerscrypt . LockBit, HelloKitty, BlackMatter, and REvil.
Black Basta has been active since April 2022, like other ransomware operations, it implements a double-extortion attack model.The ransomware will append the .basta extension to the encrypted filenames and create ransom notes named readme.txt in each folder.
Like other Linux encryptors, Black Basta’s ransomware binary will search for the /vmfs/volumes where the virtual machines are stored on the compromised ESXi servers (if no such folders are found, the ransomware exits).
Also Read: New ‘DogWalk’ Windows zero-day gets free unofficial patches – Detection & Response
The ransomware uses the ChaCha20 algorithm to encrypt the files. It also takes advantage of multithreading to use multiple processors and speeds up the encryption process.
While encrypting, the ransomware will append the .basta extension to the encrypted files’ names and create ransom notes named readme.txt in each folder.
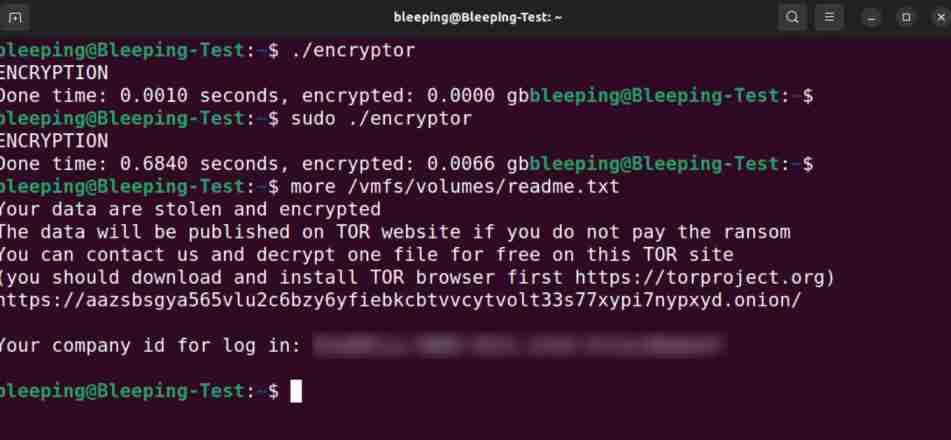
The notes include a link to the chat support panel and a unique ID that victims can use to communicate with the attackers.
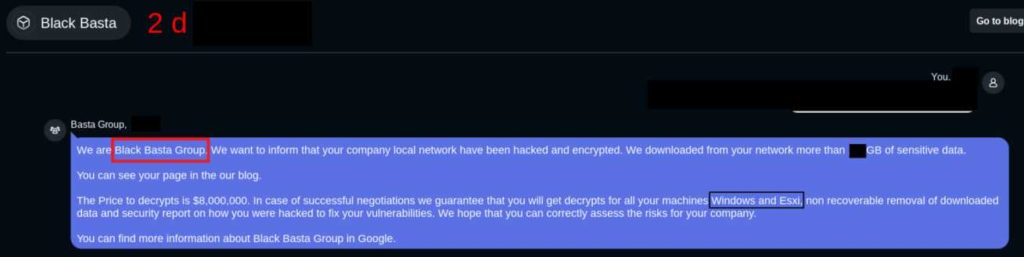
Also Read: Black Basta Ransomware operators leverage QBot for lateral movements
Indicators of Compromise
0d6c3de5aebbbe85939d7588150edf7b7bdc712fceb6a83d79e65b6f79bfc2ef
https[:]//aazsbsgya565vlu2c6bzy6yfiebkcbtvvcytvolt33s77xypi7nypxyd[.]onion
Detection Queries:
Qradar:
SELECT UTF8(payload) from events where LOGSOURCENAME(logsourceid) ilike '%linux%' and ("Image" ilike '%/chmod 777%' and ("Process CommandLine" ilike '%/vmfs/volumes%') and ("Image" ilike '%./encryptor%' or "Image" ilike '%sudo ./encryptor%')) or ("TargetFilename" ilike '%.basta')Splunk:(index="linux" AND ((Image="*/chmod 777*" AND (CommandLine="*/vmfs/volumes*") AND (Image="*./encryptor*" OR Image="*sudo ./encryptor*")) OR (TargetFilename="*.basta")))Elastic Query:((process.executable:*\/chmod\ 777* AND process.command_line:*\/vmfs\/volumes* AND process.executable:(*.\/encryptor* OR *sudo\ .\/encryptor*)) OR file.path:*.basta)GrayLog:((Image.keyword:*\/chmod\ 777* AND CommandLine.keyword:*\/vmfs\/volumes* AND Image.keyword:(*.\/encryptor* *sudo\ .\/encryptor*)) OR TargetFilename.keyword:*.basta)Logpoint:((Image="*/chmod 777*" CommandLine IN "*/vmfs/volumes*" Image IN ["*./encryptor*", "*sudo ./encryptor*"]) OR TargetFilename IN "*.basta")Google Chronicle:((target.process.file.full_path = /.*\/chmod 777.*/ and target.process.command_line = /.*\/vmfs\/volumes.*/ and (target.process.file.full_path = /.*\.\/encryptor.*/ or target.process.file.full_path = /.*sudo \.\/encryptor.*/)) or target.file.full_path = /.*\.basta/)RSA NETWITNESS:((device.class='rhlinux') && (((Image contains '/chmod 777') && (CommandLine contains '/vmfs/volumes') && (Image contains './encryptor', 'sudo \./encryptor')) || (TargetFilename contains '.basta')))ArcSight:(deviceVendor = "Unix" AND (((((destinationProcessName CONTAINS "*/chmod 777*" OR deviceProcessName CONTAINS "*/chmod 777*" OR sourceProcessName CONTAINS "*/chmod 777*")) AND ((destinationServiceName CONTAINS "*/vmfs/volumes*" OR deviceCustomString1 CONTAINS "*/vmfs/volumes*")) AND ((destinationProcessName CONTAINS "*./encryptor*" OR destinationProcessName CONTAINS "*sudo ./encryptor*" OR deviceProcessName CONTAINS "*./encryptor*" OR deviceProcessName CONTAINS "*sudo ./encryptor*" OR sourceProcessName CONTAINS "*./encryptor*" OR sourceProcessName CONTAINS "*sudo ./encryptor*"))) OR filePath CONTAINS "*.basta")))References: https://www.uptycs.com/blog/black-basta-ransomware-goes-cross-platform-now-targets-esxi-systems https://www.bleepingcomputer.com/news/security/linux-version-of-black-basta-ransomware-targets-vmware-esxi-servers/Black Basta ransomware now supports encrypting VMware ESXi servers



































