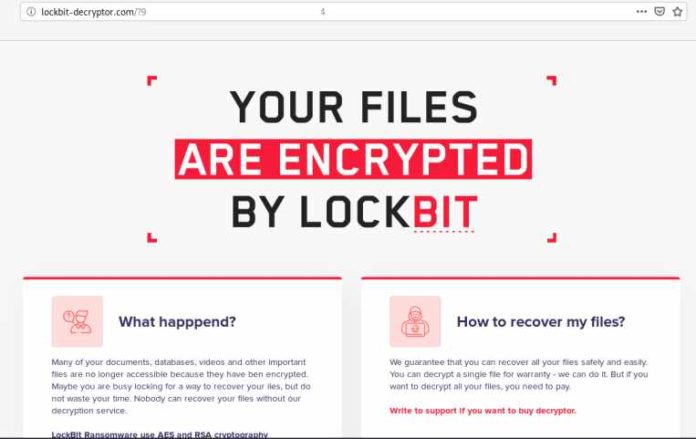
LockBit ransomware affiliates are using an interesting trick to get people into infecting their devices by disguising their malware as copyright claims.
The recipients of these emails are warned about a copyright violation, allegedly having used media files without the creator’s license. These emails demand that the recipient remove the infringing content from their websites, or they will face legal action.
The emails, spotted by analysts at AhnLab, Korea, do not determine which files were unfairly used in the body and instead tell the recipient to download and open the attached file to see the infringement content.
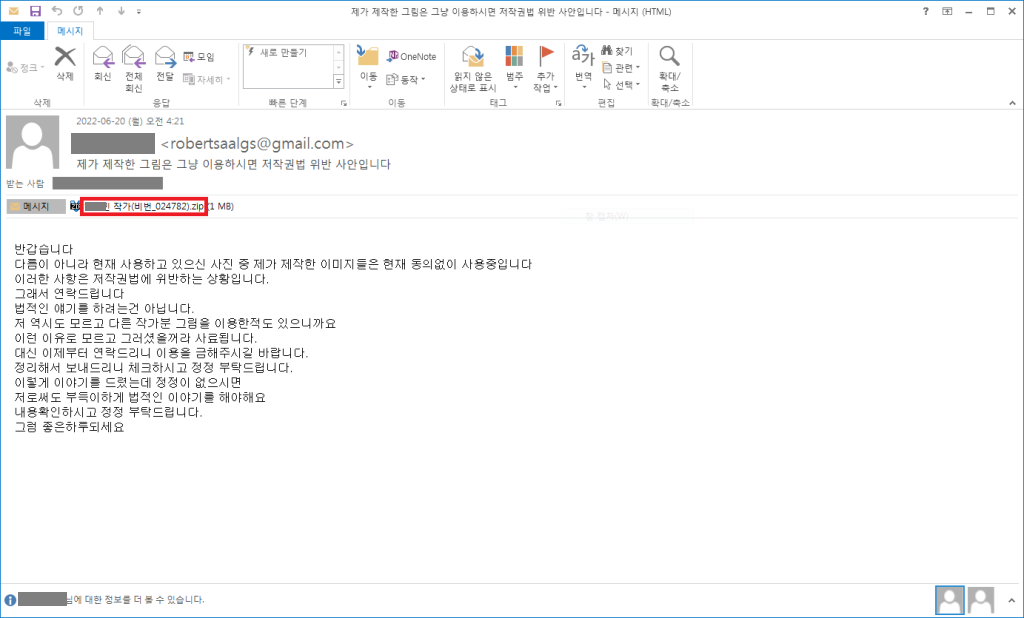
The attachment is a password-protected ZIP archive containing a compressed file, which in turn has an executable disguised as a PDF document, but in reality, is an NSIS installer.
Also Read: Windows Event ID 5379 to Detect Malicious Password-Protected File unlock
The reason for this wrapping and password protection is to evade detection from email security tools.
If the victim opens the supposed “PDF” to learn what images are being used illegally, the malware will load and encrypt the device with the LockBit 2.0 ransomware.
This ransomware prevents recovery by deleting volume shadow copy. Furthermore, to make sure the ransomware runs continuously, it registers Run Key to the registry and drops LockBit_Ransomware.hta on the desktop to keep it running even after a desktop change or a reboot.
bcdedit /set {default} bootstatuspolicy ignoreallfailures |
It then terminates multiple services and processes to avoid detection of file infection behavior and analysis.
wrapper, vmware-converter, vmware-usbarbitator64, MSSQL, MSSQL$, sql and etc. |
winword.exe, QBDBMgr.exe, 360doctor.exe, Adobe Desktop Service.exe, Autorunsc64a.exe, Sysmon.exe, Sysmon64.exe, procexp64a, procexp64a.exe, procmon.exe, procmon64.exe, procmon64a, procmon64a.exe, Raccine_x86, ProcessHacker.exe and etc. |
The encryption happens after certain services and processes are terminated. If the drive type is DRIVE_REMOVABLE, DRIVE_FIXED, or DRIVE_RAMDISK, it will also be encrypted. Extensions and names of folders or files that are excluded from encryption are as follows:
system volume information, windows photo viewer, windows PowerShell, internet explorer, windows security, windows defender, $recycle.bin, Mozilla, msbuild, appdata, windows and etc. |
.mp4 .mp3 .reg .ini .idx .cur .drv .sys .ico .lnk .dll .exe .lock .lockbit .sqlite .accdb .lzma .zipx .7z .db and etc. |
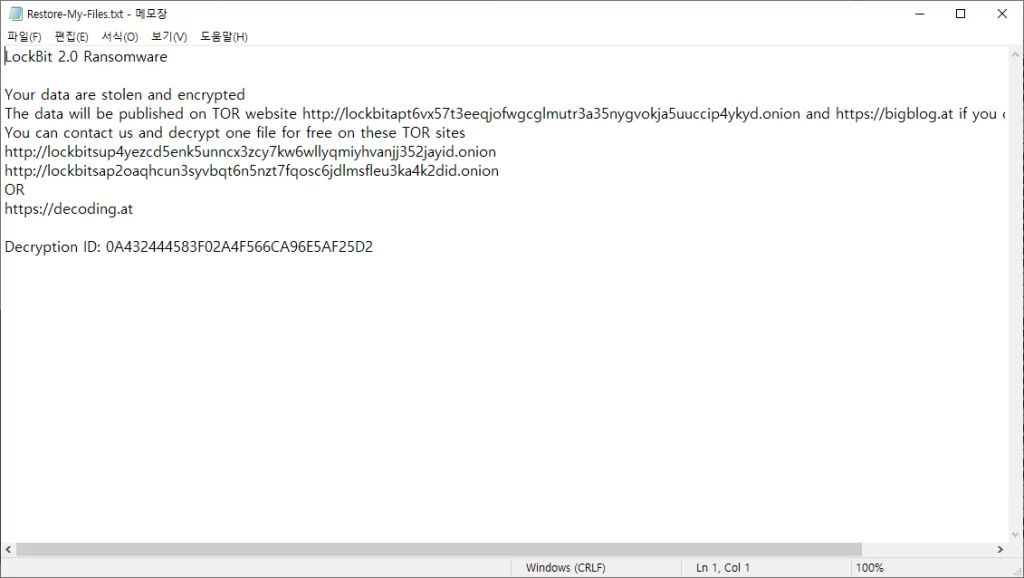
Encrypted files have an extension named .lockbit and a certain icon. Also, a ransom note named ‘Restore-My-Files.txt’ is created in the encrypted folder.
Indicator of Compromise
- 3a05e519067bea559491f6347dd6d296 (eml)
- 74a53d9db6b2358d3e5fe3accf0cb738 (exe)
Source/Credits: https://www.bleepingcomputer.com/news/security/fake-copyright-infringement-emails-install-lockbit-ransomware/
htt://asec.ahnlab.com/en/35822/