The Iran-linked Lyceum APT group, aka Hexane or Spilrin, used a new . NET-based DNS backdoor in a campaign aimed at companies in the energy and telecommunication sectors, ZScaler researchers warn.
Zscaler ThreatLabz researchers recently uncovered a new campaign where the APT group was employing a new .NET-based backdoor targeting the Middle East. The DNS backdoor borrows the code from an open-source tool named DIG.net, it was used to perform “DNS hijacking.”
The backdoor supports multiple functionalities, Including Upload/Download Files and execution of system commands on the infected machine by abusing DNS records, including TXT records for incoming commands and A records for data exfiltration.
The attack chain observed by the researchers starts with spear-phishing messages using a weaponized Word document disguised as a news report related to military affairs in Iran.
Also Read: Crypto-Miners Leveraging Atlassian Zero-Day Vulnerability
DNS hijacking is a redirection attack that relies on DNS query manipulation to take a user who attempts to visit a legitimate site to a malicious clone hosted on a server under the threat actor’s control.
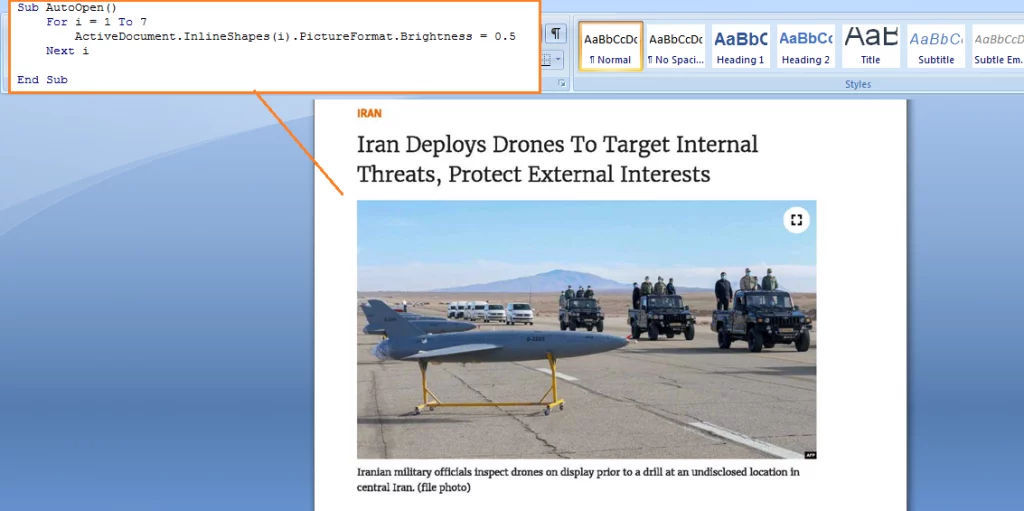
enabling macros to view the content, the DNS backdoor will be dropped onto the system when the user closes the document. The attackers leveraged the AutoClose() function to drop the DNS backdoor onto the system. The AutoClose() function reads a PE file from the text box present on the 7th page of the document.
This PE file is dropped into the Startup folder to maintain persistence via the macro code, then upon restarting the system, the DNS Backdoor is executed.
Initially, the malware sets up an attacker-controlled DNS server by acquiring the IP Address of the domain name “cyberclub[.]one” = 85[.]206[.]175[.]199 using DNS.GetHostAddresses() for the DIG Resolver function, which in turn triggers a DNS request to cyberclub[.]one for resolving the IP address. Now this IP is associated with the custom attacker-controlled DNS Server for all the further DNS queries initiated by the malware.
Also Read: Latest IOCs – Threat Actor URLs , IP’s & Malware Hashes
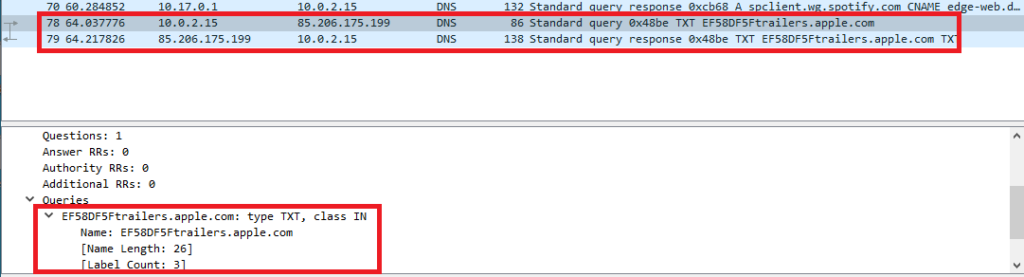
Now, the backdoor needs to receive commands from the C2 server in order to perform tasks. The backdoor sends across an initial DNS query to “*trailers.apple[.]com”
Backdoor performs initial DNS queries in order to fetch the TXT records for the domain EF58DF5trailers.apple.com. EF58DF5 is the BotID generated based on the Windows user receiving commands from the C2 server.
Source: https://www.zscaler.com
DNS query is performed to fetch the TXT records for the domain name: EF58DF5trailers.apple.com to the DNS Server: 85[.]206[.]175[.]199 which is the attacker-controlled DNS server previously initialized.
Also Read: Soc Interview Questions and Answers – CYBER SECURITY ANALYST
Here’s where the DNS hijacking happens: As the malware sends across a DNS query to fetch the TXT records to the attacker-controlled DNS server, the attacker-controlled DNS server responds with an incorrect response consisting of the commands to be executed by the backdoor such as ipconfig,whoami,uploaddd etc as shown in the screenshot below.
DIG.Net DNS response received by the backdoor and then further parsed in order to execute commands on the infected machine.
Depending on the command received in the TXT record from the C2 server, there are three functions which can be performed by the Lyceum backdoor
Download Files – If the command received from the DNS query consists of a string: “downloaddd” it initiates the download routine and downloads the file from the URL.
Upload Files – If the command received from the DNS query consists of a string: “uploaddd”, it uploads the local file on the disk.
Command Execution – If none of the above strings match the TXT record response then the response is passed on to the Command execution routine. There, the response to the txt record is executed as a command on the infected machine using “cmd.exe /c <txt_record_response_command>” and the command output is sent across to the C2 server in the form of DNS A Records.
Also Read: New SVCReady malware loads from Word doc properties – Detection & Response
APT threat actors are continuously evolving their tactics and malware to successfully carry out attacks against their targets. Attackers continuously embrace new anti-analysis tricks to evade security solutions; re-packaging of malware makes static analysis even more challenging.
Detection & Response:
Malicious File Downloaded to startup Directory:
Logpoint:((ParentImage IN ["*\\WINWORD.exe", "*\\OUTLOOK.EXE"] OR Image IN ["*\\WINWORD.exe", "*\\OUTLOOK.EXE"] OR CommandLine IN ["*WINWORD.exe*", "*OUTLOOK.EXE*"]) TargetFilename="*\\Microsoft\\Windows\\Start Menu\\Programs\\StartUp\\DnsSystem.exe*")
Qradar:SELECT UTF8(payload) from events where LOGSOURCETYPENAME(devicetype)='Microsoft Windows Security Event Log' and (("ParentImage" ilike '%\WINWORD.exe' or "ParentImage" ilike '%\OUTLOOK.EXE') or ("Image" ilike '%\WINWORD.exe' or "Image" ilike '%\OUTLOOK.EXE') or ("Process CommandLine" ilike '%WINWORD.exe%' or "Process CommandLine" ilike '%OUTLOOK.EXE%')) and UTF8(payload) ILIKE '%\Microsoft\Windows\Start Menu\Programs\StartUp\DnsSystem.exe%'
Splunk:(source="WinEventLog:*" AND (((ParentImage="*\\WINWORD.exe" OR ParentImage="*\\OUTLOOK.EXE") OR (Image="*\\WINWORD.exe" OR Image="*\\OUTLOOK.EXE") OR (CommandLine="*WINWORD.exe*" OR CommandLine="*OUTLOOK.EXE*")) AND TargetFilename="*\\Microsoft\\Windows\\Start Menu\\Programs\\StartUp\\DnsSystem.exe*")
Elastic Query:((process.parent.executable:(*\\WINWORD.exe OR *\\OUTLOOK.EXE) OR process.executable:(*\\WINWORD.exe OR *\\OUTLOOK.EXE) OR process.command_line:(*WINWORD.exe* OR *OUTLOOK.EXE*)) AND file.path:*\\Microsoft\\Windows\\Start\ Menu\\Programs\\StartUp\\DnsSystem.exe*)
Microsoft Defender:DeviceProcessEvents | where (((InitiatingProcessFolderPath endswith @"\WINWORD.exe" or InitiatingProcessFolderPath endswith @"\OUTLOOK.EXE") or (FolderPath endswith @"\WINWORD.exe" or FolderPath endswith @"\OUTLOOK.EXE") or (ProcessCommandLine contains "WINWORD.exe" or ProcessCommandLine contains "OUTLOOK.EXE")) and FolderPath contains @"\Microsoft\Windows\Start Menu\Programs\StartUp\DnsSystem.exe")
Archsight:(((sourceProcessName CONTAINS "*\\WINWORD.exe" OR sourceProcessName CONTAINS "*\\OUTLOOK.EXE" OR destinationProcessName CONTAINS "*\\WINWORD.exe" OR destinationProcessName CONTAINS "*\\OUTLOOK.EXE" OR deviceProcessName CONTAINS "*\\WINWORD.exe" OR deviceProcessName CONTAINS "*\\OUTLOOK.EXE" OR deviceCustomString1 CONTAINS "*WINWORD.exe*" OR deviceCustomString1 CONTAINS "*OUTLOOK.EXE*" OR destinationServiceName CONTAINS "*WINWORD.exe*" OR destinationServiceName CONTAINS "*OUTLOOK.EXE*")) AND filePath CONTAINS "*\\Microsoft\\Windows\\Start Menu\\Programs\\StartUp\\DnsSystem.exe*")
RSA Netwitness:(((ParentImage contains '\WINWORD\.exe', '\OUTLOOK\.EXE') || (Image contains '\WINWORD\.exe', '\OUTLOOK\.EXE') || (CommandLine contains 'WINWORD\.exe', 'OUTLOOK\.EXE')) && (TargetFilename contains 'Microsoft\Windows\Start Menu\Programs\StartUp\DnsSystem.exe'))
Carbon Black:((parent_name:(*\\WINWORD.exe OR *\\OUTLOOK.EXE) OR process_name:(*\\WINWORD.exe OR *\\OUTLOOK.EXE) OR process_cmdline:(*WINWORD.exe* OR *OUTLOOK.EXE*)) AND filemod_name:*\\Microsoft\\Windows\\Start\ Menu\\Programs\\StartUp\\DnsSystem.exe*)
Suspicious TXT DNS Records
Elastic Query:
(dns.question.type:"TXT" AND dns.answers.name:(*ipconfig* OR *downloaddd* OR *uploaddd*))Qradar:SELECT UTF8(payload) from events where UTF8(payload) ILIKE 'TXT' and ("answer" ilike '%ipconfig%' or "answer" ilike '%downloaddd%' or "answer" ilike '%uploaddd%')Splunk: index=* (record_type="TXT" AND (answer="*ipconfig*" OR answer="*downloaddd*" OR answer="*uploaddd*")) AND source=WinEventLog:DNS Server ArcSight:(deviceCustomString1 = "TXT" AND (deviceCustomString1 CONTAINS "*ipconfig*" OR deviceCustomString1 CONTAINS "*downloaddd*" OR deviceCustomString1 CONTAINS "*uploaddd*"))GrayLog:(record_type:"TXT" AND answer.keyword:(*ipconfig* *downloaddd* *uploaddd*))RSA Netwitness:((record_type='TXT') && (answer contains 'ipconfig', 'downloaddd', 'uploaddd'))Data Exfiltration via DNS A Record: Splunk:index=* (record_type="A" AND (answer="*85.206.175.199*")) AND source=WinEventLog:DNS ServerQradar:SELECT UTF8(payload) from events where UTF8(payload) ILIKE 'A' and ("answer" ilike '%85.206.175.199%')Elastic Query:(dns.question.type:"A" AND dns.answers.name:*85.206.175.199*)GrayLog:(record_type:"A" AND answer.keyword:*85.206.175.199*)Indicators of Compromise Document Hash: 13814a190f61b36aff24d6aa1de56fe2 Exe Hash: 8199f14502e80581000bd5b3bda250ee Domain and URL's: cyberclub[.]one hxxp://news-spot[.]live/Reports/1/?id=1111&pid=a52 hxxp://news-spot[.]live/Reports/1/?id=1111&pid=a28 hxxp://news-spot[.]live/Reports/1/?id=1111&pid=a40 hxxp://news-spot[.]live/Reports/1/45/DnsSystem[.]exe Source/Reference: https://www.zscaler.com/blogs/security-research/lyceum-net-dns-backdoor hhps://securityaffairs.co/wordpress/132164/apt/lyceum-apt-target-energy-dns-backdoor.html