In the last blog, we have gone through 3 techniques used in Masquerading. The first three techniques are Sub-Technique 1 – Invalid Code Signature (T1036.001), Sub-Technique 2 – Right-to-Left Override (T1036.002) &Sub-Technique 3 – Rename System Utilities (T1036.003). Today we are going to see rest techniques and detection methods.
Sub-Technique 4 -Masquerade Task or Service (T1036.004):
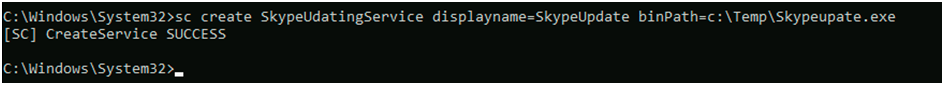
Malicious actors may try to change the name of a task or service in order to make it appear legitimate or benign. Tasks/services run by Task Scheduler or systemd are usually given a name and/or description. Windows services will have both a service name and a display name. There are innumerable benign tasks and services that have commonly associated names that are similar or identical to legitimate ones. Other fields, such as description, may be used by adversaries to make tasks or services appear legitimate.
Example:
Sometimes tricking the user that a normal task is being run to trick them that it’s a legitimate service.
Also Read: Soc Interview Questions and Answers – CYBER SECURITY ANALYST
Sub-Technique 5 -Match Legitimate Name or location (T1036.005):
Attackers may match or approximate the name or location of legitimate files when naming/placing their files. This is done to avoid detection and evades defenses. This can be accomplished by placing an executable in a commonly trusted directory (for example, under System32) or by naming it after a legitimate, trusted program (ex: svchost.exe). Alternatively, the filename provided could be a close match to a legitimate program or something innocuous. Malicious actors may also use the same icon as the file they are attempting to imitate.
Example:
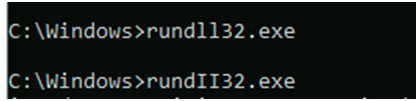
In the below image we have imitated the rundll32 file. To the untrained eye, their names appear to be quite similar, but the difference is that rundll32 is now typed with an uppercase “i.” This may appear similar by typing rundll and rundII, but it also depends on the type of font used.
Also Read: Latest IOCs – Threat Actor URLs , IP’s & Malware Hashes
Sub-Technique 6 -Masquerading: Space after Filename(T1036.006):
Malicious actors can mask a program’s true file type by changing a file’s extension. When it comes to certain file types (specifically this does not work with .app extensions), appending a space to the end of a filename changes how the operating system processes the file. We have more open websites to change the icon image and also text file icons to trick users.
Example:
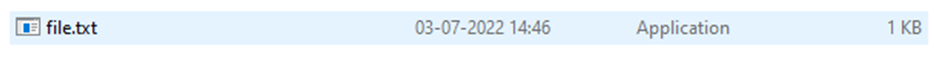
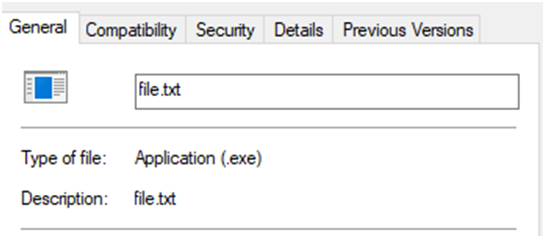
In the below screenshot the extension is .txt and the icon is .exe icon. While checking the properties of the file, it clearly shows that it is an .exe file.
Screenshot 1: This is what users visually see while downloading it from email or browser.
Screenshot 2: File properties
Sub-Technique 7 -Masquerading: Space after Filename (T1036.006):
Malicious actors may use double extensions to conceal dangerous payload file types. A common application involves duping a user into opening what appears to be a harmless file type but is actually executable code. These files are frequently disguised as email attachments, allowing an adversary to gain Initial Access to a user’s system via Spearphishing Attachment, followed by User Execution.
Example:
An executable file attachment named sample.txt.exe may appear to a user as sample.txt. The user may then mistake it for a harmless text file and open it, unknowingly executing the hidden malware.
Masquerading Mitigations:
| Mitigation | Mitigation Description | Attacks techinique |
| Code Signing(M1045) | Enforce binary and application integrity with digital signature verification to prevent untrusted code from executing. | Invalid Code Signature |
| Restrict File and Directory Permissions (M1022) | Use file system access controls to protect folders such as C:\Windows\System32. | Rename System Utilities & Match Legitimate Name or Location |
| Code Signing(M1045) | Require signed binaries and images. | Match Legitimate Name or Location |
| Execution Prevention(M1038) | Use tools that restrict program execution via application control by attributes other than file name for common operating system utilities that are needed. | Match Legitimate Name or Location |
| Operating System Configuration(M1028) | Disable the default to “hide file extensions for known file types” in Windows OS | Double File Extension |
| User Training(M1017) | Train users to look for double extensions in filenames, and in general use training as a way to bring awareness to common phishing and spearphishing techniques and how to raise suspicion for potentially malicious events. | Double File Extension |
Also Read: Email Header Analysis – Use Cases Including SPF, DKIM & DMARC
Masquerading Detection:
| Mitre Detection ID | Data component | Detects | Attack Technique |
| DS0022 | File Metadata | Monitor for contextual data about a file, which may include information such as name, the content (ex: signature, headers, or data/media), user/ower, permissions, etc. | Double File Extension |
| DS0022 | File metadata | Collect and analyze signing certificate metadata and check signature validity on software that executes within the environment, look for invalid signatures as well as unusual certificate characteristics and outliers. | Code Signing |
| DS0022 | File metadata | Monitor for common formats of RTLO characters within filenames such as \u202E, [U+202E], and %E2%80%AE. Defenders should also check their analysis tools to ensure they do not interpret the RTLO character and instead print the true name of the file containing it. | Right-to-Left Override |
| DS0017 | Command execution | Monitor executed commands and arguments for actions that could be taken to gather. | Rename System Utilities |
| DS0022 | File metadata | Collecting and comparing disk and resource filenames for binaries by looking to see if the InternalName, OriginalFilename, and/or ProductName match what is expected could provide useful leads, but may not always be indicative of malicious activity. | Rename System Utilities, Match Legitimate Name or Location |
| DS0022 | File Modification | Monitor for changes made to files for unexpected modifications to file names that are mismatched between the file name on disk and that of the binary’s PE metadata. This is a likely indicator that a binary was renamed after it was compiled. | Rename System Utilities |
| DS0009 | Process Metadata | Monitor for file names that are mismatched between the file name on disk and that of the binary’s PE metadata, this is a likely indicator that a binary was renamed after it was compiled. | Rename System Utilities |
| DS0017 | Command execution | Monitor executed commands and arguments that may attempt to manipulate the name of a task or service to make it appear legitimate or benign. | Masquerade Task or Service |
| DS0003 | Scheduled Job Metadata | Monitor for contextual data about a scheduled job, which may include information such as name, timing, command(s), etc. | Masquerade Task or Service |
| DS0003 | Scheduled Job Metadata | Monitor for changes made to scheduled jobs for unexpected modifications to execution launch | Masquerade Task or Service |
| DS0019 | Service Creation | Monitor for newly constructed services/daemons. Data and events should not be viewed in isolation, but as part of a chain of behavior that could lead to other activities, such as network connections made for Command and Control, learning details about the environment through Discovery, and Lateral Movement. | Masquerade Task or Service |
| DS0019 | Service Metadata | Monitor for changes made to services for unexpected modifications to names, descriptions, and/or start types | Masquerade Task or Service |
| DS0022 | File Metadata | Collect file hashes; file names that do not match their expected hash are suspect. Perform file monitoring; files with known names but in unusual locations are suspect. Likewise, files that are modified outside of an update or patch are suspect. | Match Legitimate Name or Location |
| DS0007 | Image Metadata | In containerized environments, use image IDs and layer hashes to compare images instead of relying only on their names.[151] Monitor for the unexpected creation of new resources within your cluster in Kubernetes, especially those created by atypical users. | Match Legitimate Name or Location |
| DS0022 | File Metadata | Monitor for spaces at the end of file names, that can easily be checked with file monitoring. From the user’s perspective though, this is very hard to notice from within the Finder.app or on the command line in the Terminal.app. Processes executed from binaries containing non-standard extensions in the filename are suspicious. | Space after Filename |
| DS0022 | File Creation | Monitor for files written to disk that contain two file extensions, particularly when the second is an executable. | Double File Extension |
Masquerading Detection Rules:
| Name | Splunk rule |
| Linux Kworker Process In Writable Process Path | | tstats `security_content_summariesonly` count min(_time) as firstTime max(_time) as lastTime from datamodel=Endpoint.Processes where Processes.parent_process = “*[kworker/*” Processes.parent_process_path IN (“/home/*”, “/tmp/*”, “/var/log/*”) Processes.process=”*iptables*” by Processes.parent_process_name Processes.parent_process Processes.process_name Processes.process Processes.process_id Processes.parent_process_id Processes.parent_process_path Processes.process_guid Processes.dest Processes.user | `drop_dm_object_name(Processes)` | `security_content_ctime(firstTime)` | `security_content_ctime(lastTime)` | `linux_kworker_process_in_writable_process_path_filter` |
| Suspicious Rundll32 Rename | | tstats `security_content_summariesonly` count min(_time) as firstTime max(_time) as lastTime from datamodel=Endpoint.Processes where Processes.original_file_name=RUNDLL32.exe AND Processes.process_name!=rundll32.exe by Processes.dest Processes.user Processes.parent_process_name Processes.process_name Processes.process Processes.process_id Processes.parent_process_id Processes.original_file_name | `drop_dm_object_name(Processes)` | `security_content_ctime(firstTime)` | `security_content_ctime(lastTime)` | `suspicious_rundll32_rename_filter` |
| Suspicious MSBuild Rename | | tstats `security_content_summariesonly` count min(_time) as firstTime max(_time) as lastTime from datamodel=Endpoint.Processes where Processes.process_name!=msbuild.exe AND Processes.original_file_name=MSBuild.exe by Processes.dest Processes.user Processes.parent_process_name Processes.process_name Processes.process Processes.process_id Processes.parent_process_id Processes.original_file_name | `drop_dm_object_name(Processes)` | `security_content_ctime(firstTime)` | `security_content_ctime(lastTime)` | `suspicious_msbuild_rename_filter` |
| Suspicious microsoft workflow compiler rename | | tstats `security_content_summariesonly` count min(_time) as firstTime max(_time) as lastTime from datamodel=Endpoint.Processes where Processes.process_name!=microsoft.workflow.compiler.exe AND Processes.original_file_name=Microsoft.Workflow.Compiler.exe by Processes.dest Processes.user Processes.parent_process_name Processes.process_name Processes.process Processes.process_id Processes.parent_process_id Processes.original_file_name | `drop_dm_object_name(Processes)` | `security_content_ctime(firstTime)` | `security_content_ctime(lastTime)` | `suspicious_microsoft_workflow_compiler_rename_filter` |
| Linux Kworker Process CommandLine | | tstats `security_content_summariesonly` count min(_time) as firstTime max(_time) as lastTime from datamodel=Endpoint.Processes where Processes.process = “*[kworker/*” OR Processes.parent_process = “*[kworker/*” by Processes.parent_process_name Processes.parent_process Processes.process_name Processes.process Processes.process_id Processes.parent_process_id Processes.process_guid Processes.dest Processes.user | `drop_dm_object_name(Processes)` | `security_content_ctime(firstTime)` | `security_content_ctime(lastTime)` | `linux_kworker_process_commandline_filter` |
| Suspicious msbuild path | | tstats `security_content_summariesonly` count values(Processes.process_name) as process_name values(Processes.process) as process min(_time) as firstTime max(_time) as lastTime from datamodel=Endpoint.Processes where `process_msbuild` AND (Processes.process_path!=*\\framework*\\v*\\*) by Processes.dest Processes.original_file_name Processes.parent_process Processes.user | `drop_dm_object_name(Processes)` | `security_content_ctime(firstTime)` | `security_content_ctime(lastTime)` | `suspicious_msbuild_path_filter` |
| Windows InstallUtil in Non Standard Path | | tstats `security_content_summariesonly` count min(_time) as firstTime max(_time) as lastTime FROM datamodel=Endpoint.Processes where `process_installutil` NOT (Processes.process_path IN (“*\\Windows\\ADWS\\*”,”*\\Windows\\SysWOW64*”, “*\\Windows\\system32*”, “*\\Windows\\NetworkController\\*”, “*\\Windows\\SystemApps\\*”, “*\\WinSxS\\*”, “*\\Windows\\Microsoft.NET\\*”)) by Processes.dest Processes.user Processes.parent_process Processes.process_name Processes.process Processes.original_file_name Processes.process_id Processes.parent_process_id Processes.process_hash | `drop_dm_object_name(“Processes”)` | `security_content_ctime(firstTime)` | `security_content_ctime(lastTime)` | `windows_installutil_in_non_standard_path_filter` |
| Attacker Tools On Endpoint | | tstats `security_content_summariesonly` count min(_time) as firstTime max(_time) as lastTime values(Processes.process) as process values(Processes.parent_process) as parent_process from datamodel=Endpoint.Processes where Processes.dest!=unknown Processes.user!=unknown by Processes.dest Processes.user Processes.process_name Processes.process | `security_content_ctime(firstTime)` | `security_content_ctime(lastTime)` | `drop_dm_object_name(Processes)` | lookup attacker_tools attacker_tool_names AS process_name OUTPUT description | search description !=false | `attacker_tools_on_endpoint_filter` |
| Suspicious Copy on System32 | | tstats `security_content_summariesonly` count min(_time) as firstTime max(_time) as lastTime from datamodel=Endpoint.Processes where Processes.parent_process_name IN(“cmd.exe”, “powershell*”,”pwsh.exe”, “sqlps.exe”, “sqltoolsps.exe”, “powershell_ise.exe”) AND `process_copy` AND Processes.process IN(“*\\Windows\\System32\*”, “*\\Windows\\SysWow64\\*”) AND Processes.process = “*copy*” by Processes.dest Processes.user Processes.parent_process_name Processes.process_name Processes.process Processes.process_id Processes.parent_process_id | `drop_dm_object_name(Processes)` | `security_content_ctime(firstTime)` | `security_content_ctime(lastTime)` | `suspicious_copy_on_system32_filter` |
| Executables Or Script Creation In Suspicious Path | |tstats `security_content_summariesonly` values(Filesystem.file_path) as file_path count min(_time) as firstTime max(_time) as lastTime from datamodel=Endpoint.Filesystem where (Filesystem.file_name = *.exe OR Filesystem.file_name = *.dll OR Filesystem.file_name = *.sys OR Filesystem.file_name = *.com OR Filesystem.file_name = *.vbs OR Filesystem.file_name = *.vbe OR Filesystem.file_name = *.js OR Filesystem.file_name = *.ps1 OR Filesystem.file_name = *.bat OR Filesystem.file_name = *.cmd OR Filesystem.file_name = *.pif) AND ( Filesystem.file_path = *\\windows\\fonts\\* OR Filesystem.file_path = *\\windows\\temp\\* OR Filesystem.file_path = *\\users\\public\\* OR Filesystem.file_path = *\\windows\\debug\\* OR Filesystem.file_path = *\\Users\\Administrator\\Music\\* OR Filesystem.file_path = *\\Windows\\servicing\\* OR Filesystem.file_path = *\\Users\\Default\\* OR Filesystem.file_path = *Recycle.bin* OR Filesystem.file_path = *\\Windows\\Media\\* OR Filesystem.file_path = *\\Windows\\repair\\* OR Filesystem.file_path = *\\AppData\\Local\\Temp* OR Filesystem.file_path = *\\PerfLogs\\*) by Filesystem.file_create_time Filesystem.process_id Filesystem.file_name Filesystem.user | `drop_dm_object_name(Processes)` | `security_content_ctime(firstTime)` | `security_content_ctime(lastTime)` | `executables_or_script_creation_in_suspicious_path_filter` |
| Suspicious MSBuild Rename | | tstats `security_content_summariesonly` count min(_time) as firstTime max(_time) as lastTime from datamodel=Endpoint.Processes where Processes.process_name!=msbuild.exe AND Processes.original_file_name=MSBuild.exe by Processes.dest Processes.user Processes.parent_process_name Processes.process_name Processes.process Processes.process_id Processes.parent_process_id Processes.original_file_name | `drop_dm_object_name(Processes)` | `security_content_ctime(firstTime)` | `security_content_ctime(lastTime)` | `suspicious_msbuild_rename_filter` |
| Suspicious msbuild path | | tstats `security_content_summariesonly` count values(Processes.process_name) as process_name values(Processes.process) as process min(_time) as firstTime max(_time) as lastTime from datamodel=Endpoint.Processes where `process_msbuild` AND (Processes.process_path!=*\\framework*\\v*\\*) by Processes.dest Processes.original_file_name Processes.parent_process Processes.user | `drop_dm_object_name(Processes)` | `security_content_ctime(firstTime)` | `security_content_ctime(lastTime)` | `suspicious_msbuild_path_filter` |
| System Processes Run From Unexpected Locations | | tstats `security_content_summariesonly` count min(_time) as firstTime max(_time) as lastTime FROM datamodel=Endpoint.Processes where Processes.process_path !=”C:\\Windows\\System32*” Processes.process_path !=”C:\\Windows\\SysWOW64*” by Processes.dest Processes.user Processes.parent_process Processes.process_name Processes.process Processes.process_id Processes.parent_process_id Processes.process_hash | `drop_dm_object_name(“Processes”)` | `security_content_ctime(firstTime)` | `security_content_ctime(lastTime)` | `is_windows_system_file` | `system_processes_run_from_unexpected_locations_filter` |
| Execution of File with Multiple Extensions | | tstats `security_content_summariesonly` count min(_time) as firstTime max(_time) as lastTime from datamodel=Endpoint.Processes where Processes.process = *.doc.exe OR Processes.process = *.htm.exe OR Processes.process = *.html.exe OR Processes.process = *.txt.exe OR Processes.process = *.pdf.exe OR Processes.process = *.doc.exe by Processes.dest Processes.user Processes.process Processes.parent_process | `security_content_ctime(firstTime)` | `security_content_ctime(lastTime)` | `drop_dm_object_name(Processes)` | `execution_of_file_with_multiple_extensions_filter` |
| Suspicious writes to windows Recycle Bin | | tstats `security_content_summariesonly` count min(_time) as firstTime max(_time) as lastTime values(Filesystem.file_path) as file_path values(Filesystem.file_name) as file_name FROM datamodel=Endpoint.Filesystem where Filesystem.file_path = “*$Recycle.Bin*” by Filesystem.process_id Filesystem.dest | `drop_dm_object_name(“Filesystem”)` | search [ | tstats `security_content_summariesonly` values(Processes.user) as user values(Processes.process_name) as process_name values(Processes.parent_process_name) as parent_process_name FROM datamodel=Endpoint.Processes where Processes.process_name != “explorer.exe” by Processes.process_id Processes.dest | `drop_dm_object_name(“Processes”)` | table process_id dest] | `suspicious_writes_to_windows_recycle_bin_filter` |
| Suspicious writes to System Volume Information | (`sysmon` OR tag=process) EventCode=11 process_id!=4 file_path=*System\ Volume\ Information* | stats count min(_time) as firstTime max(_time) as lastTime by dest, Image, file_path | `security_content_ctime(firstTime)` | `security_content_ctime(lastTime)` | `suspicious_writes_to_system_volume_information_filter` |
Conclusion:
So we have gone through all the techniques and detection methods for Masquerading attacks. Each and every move inside the machine will be a malicious activity sometime. So we need to monitor most of the rules mentioned above. Happy hunting!!
Source: https://research.splunk.com/tags/#masquerading



































