As we discussed earlier, Microsoft provides a fantastic set of cloud security solutions and MCAS is one of them. All the cloud activities will be stored here, and it alerts for suspicious behavior in real-time. We can integrate logs and alerts with sentinel to trigger an alert in it.
Microsoft Defender for Cloud Apps is a Cloud Access Security Broker (CASB) that offers a variety of deployment options such as log collection, API connectors, and reverse proxy. It offers comprehensive visibility, control over data travel, and sophisticated analytics to detect and combat cyber threats across all Microsoft and third-party cloud services.
What Exactly is a CASB?
Employees and IT teams benefit from increased flexibility because of moving to the cloud. It does, however, introduce new challenges and complexities in terms of keeping your organization secure. To reap the full benefits of cloud apps and services, an IT team must strike the right balance between facilitating access and safeguarding critical data.
This is where a Cloud Access Security Broker comes in to help strike a balance by enforcing your enterprise security policies and adding safeguards to your organization’s use of cloud services. As the name implies, CASBs act as a gatekeeper, brokering real-time access between your enterprise users and the cloud resources they use, regardless of where your users are or what device they are using.
CASBs accomplish this by discovering and providing visibility into Shadow IT and app use, monitoring user activities for anomalous behaviors, controlling access to your resources, classifying and preventing sensitive information leaks, protecting against malicious actors, and assessing cloud service compliance.
Also Read: Latest IOCs – Threat Actor URLs , IP’s & Malware Hashes
As an organization, need to protect the users and confidential data from the different methods employed by malicious actors. In general, CASBs should help you do this by providing a wide array of capabilities that protect your environment across the following pillars:
- Visibility: detect all cloud services; assign each a risk ranking; identify all users and third-party apps able to log in
- Data security: identify and control sensitive information (DLP); respond to sensitivity labels on content
- Threat protection: offer adaptive access control (AAC); provide user and entity behavior analysis (UEBA); mitigate malware
- Compliance: supply reports and dashboards to demonstrate cloud governance; assist efforts to conform to data residency and regulatory compliance requirements
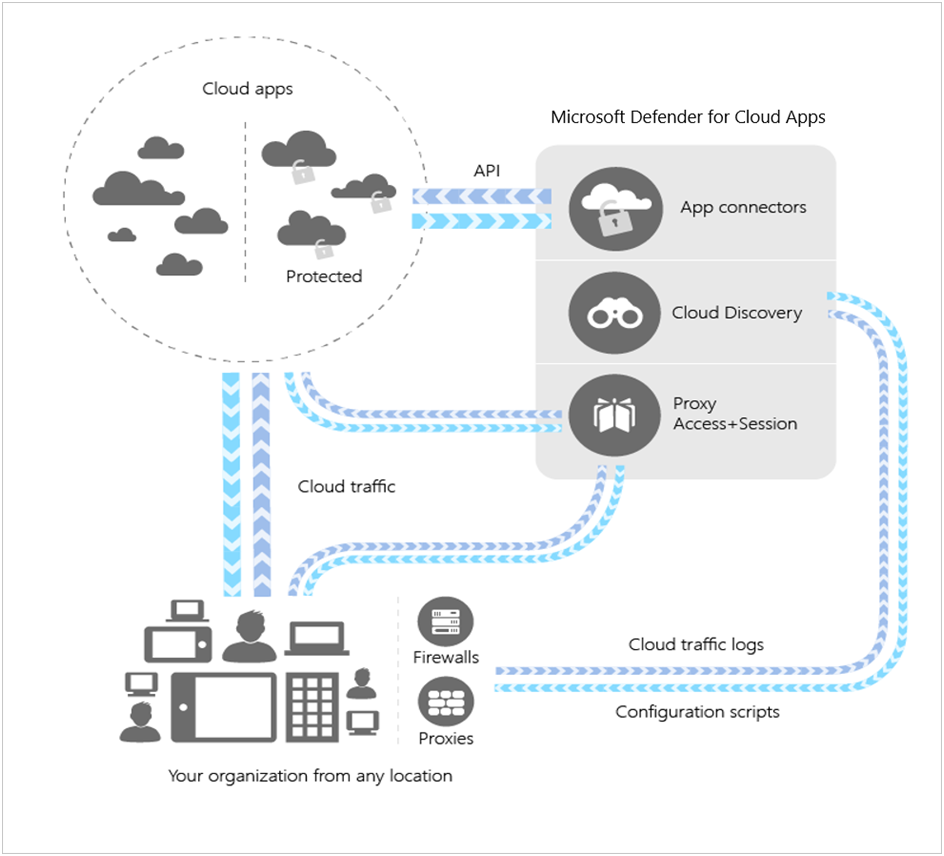
MCAS Architecture:
Defender for Cloud Apps enhances visibility in the cloud by:
- Cloud Discovery is used to map and identify your cloud environment as well as the cloud apps that your organization uses.
- Apps that are sanctioned and unsanctioned in your cloud
- Using simple-to-deploy app connectors that leverage provider APIs for visibility and governance of the apps you connect to.
- Protect your cloud apps with Conditional Access App Control to gain real-time visibility and control over access and activities.
- By establishing and then constantly fine-tuning policies, we can help you maintain continuous control.
Also Read: How DKIM SPF & DMARC Work to Prevent Email Spoofing and Phishing
Defender for Cloud Apps best practices:
- Discover and assess cloud apps
- Apply cloud governance policies
- Limit exposure of shared data and enforce collaboration policies
- Discover, classify, label, and protect regulated and sensitive data stored in the cloud
- Enforce DLP and compliance policies for data stored in the cloud
- Block and protect download of sensitive data to unmanaged or risky devices
- Secure collaboration with external users by enforcing real-time session controls
- Detect cloud threats, compromised accounts, malicious insiders, and ransomware
- Use the audit trail of activities for forensic investigations
- Secure IaaS services and custom apps
Also Read: Azure Sentinel and its Components
Following this, we will be seeing how we can use MCAS and investigate alerts with it. The first tutorial will be covering how to Discover and manage shadow IT in the network.
Discover and manage shadow IT in the network:
When IT administrators are asked how many cloud apps they believe their employees use, they typically say 30 or 40, whereas the average is over 1,000 separate apps used by employees in your organization. Shadow IT enables you to understand and identify which apps are being used, as well as your risk level. 80 percent of employees use unapproved apps that have not been reviewed and may violate your security and compliance policies. And, because your employees can access your resources and apps from outside your corporate network, having rules and policies on your firewalls is no longer sufficient.
We’ll look at how to use Cloud Discovery to discover which apps are being used, investigate the risk of these apps, configure policies to identify new risky apps that are being used, and unsanctioned these apps so that they can be blocked natively using your proxy or firewall appliance.
- Discover and identify Shadow IT
- Evaluate and analyze
- Manage your apps
- Advanced Shadow IT discovery reporting
- Approved apps must be controlled
1-Discover and identify Shadow IT:
Determine your organization’s security posture by running Cloud Discovery in your organization to see what’s going on in your network. This can be accomplished through any of the following methods:
- By integrating with Microsoft Defender for Endpoint, you can get Cloud Discovery up and running quickly. With this native integration, you can begin collecting data on cloud traffic across your Windows 10 and Windows 11 devices, both on and off the network, right away.
- It is critical to deploy the Defender for Cloud Apps log collector on your firewalls and other proxies to collect data from your endpoints and send it to Defender for Cloud Apps for analysis to ensure coverage on all devices connected to your network.
- Connect Defender for Cloud Apps to your proxy server. Defender for Cloud Apps integrates natively with a few third-party proxies, including Zscaler.
Non-sanctioned apps are frequently used for legitimate work-related purposes that aren’t addressed by a sanctioned app. Determine your apps’ risk levels by using the Defender for Cloud Apps catalog to learn more about the risks associated with each discovered app. The Defender for Cloud App Catalog contains over 25,000 apps that have been evaluated using more than 80 risk factors. The risk factors begin with general app information (where is the app’s headquarters, who is the publisher), and progress through security measures and controls (support for encryption at rest, provides an audit log of user activity).
Also Read: Advance Mitre Threat Mapping – Attack Navigator & TRAM Tools
2-Evaluate and analyze:
- Evaluate compliance: Check whether the apps are certified as compliant with your organization’s standards, such as HIPAA, SOC2, GDPR.
- Analyze usage: Now that you’ve decided whether to use the app in your organization, you should investigate how and who is using it. If it is only used in a limited capacity in your organization, it may be fine; however, if the usage increases, you may want to be notified so you can decide whether to block the app.
- Identify alternative apps: Use the Cloud App Catalog to find safer apps that perform similar business functions as the detected risky apps while adhering to your organization’s policy. You can accomplish this by using advanced filters to find apps in the same category that meet your various security controls.
3-Manage your apps:
- Manage cloud applications: Defender for Cloud Apps assists you in managing app usage in your organization. After you’ve identified the various patterns and behaviours in your organization, you can create new custom app tags to categorize each app based on its business status or justification. These tags can then be used for specific monitoring purposes, such as identifying high traffic to apps labelled as risky cloud storage apps.
- Manage discovered apps using Azure Active Directory (Azure AD) Gallery: Defender for Cloud Apps also makes use of its native integration with Azure AD to let you manage your discovered apps in the Azure AD Gallery. You can use Azure AD to manage apps that are already in the Azure AD Gallery by enabling single sign-on. To do so, select the three dots at the end of the row where the relevant app appears, and then select Manage app with Azure AD.
4-Advanced Shadow IT discovery reporting:
In addition to the reporting options provided by Defender for Cloud Apps, Cloud Discovery logs can be integrated into Microsoft Sentinel for further investigation and analysis. You can view the data in dashboards, run queries using the Kusto query language, export queries to Microsoft Power BI, integrate with other sources, and create custom alerts once it is in Microsoft Sentinel.
Also Read: Autoruns v14.06 – Malware Autostart locations for Incident Responders
5-Approved apps must be controlled:
Because of the nature of cloud apps, they are updated daily, and new apps are added all the time. As a result, employees are constantly using new apps, and it is critical to keep track of, review, and update your policies, as well as check which apps your users are using, as well as their usage and behavior patterns. You can always go to the Cloud Discovery dashboard to see what new apps are being used, and then repeat the steps in this article to ensure that your organization and data are safe.
In the next blog, we will be looking into another tutorial with MCAS.
Reference: https://docs.microsoft.com/en-us/defender-cloud-apps/tutorial-shadow-it



































