When it comes to organizations and individuals, malware is always a source of concern. The same attack vectors are frequently used by attackers nowadays. An analyst/AV can detect malicious code, extract it, and analyze it to figure out how it works so that the threat may be immediately stopped. As a consequence, attackers are urged to develop tactics to keep their malicious files hidden for as long as possible; one of the most common techniques is code obfuscation, which is what we’ll explore today.
Since malware developers frequently employ obfuscation to evade antivirus scanners, it’s essential to understand how this approach is used in malware.
What is obfuscation?
Making anything tough to grasp is referred to as obfuscation. To protect intellectual property or trade secrets, and to prevent an adversary from reverse engineering a proprietary software application, programming code is frequently obfuscated. One form of obfuscation is to encrypt some or all of a program’s code. An “obfuscator” is a tool that converts simple source code into a program that does the same thing but is more difficult to read and understand.
Malware obfuscation:
- Malware authors often use packing or obfuscation technique to make their files more difficult to detect or analyze. Malware obfuscation is a technique used to create textual and binary data difficult to interpret. It helps adversaries to hide critical strings in a program, because they reveal patterns of the malware’s behavior. The strings would be registry keys and infected URLs.
- Packed programs are a subset of obfuscated programs in which the malicious program is compressed and cannot be analyzed. Packer and obfuscation techniques will limit the attempts to statically analyze the malware.
- Non-Malicious programs always include many strings. Malware that is packed or obfuscated contains very few strings. If the program has only few strings, it is probably either obfuscated or packed, which gives a clue that it may be malicious.
Malware Obfuscation Techniques:
Since malware writers frequently employ obfuscation to evade antivirus scanners, it’s important to understand how this technique is used in malware. Here we have a few Obfuscation Techniques which is used to pack the malicious strings:
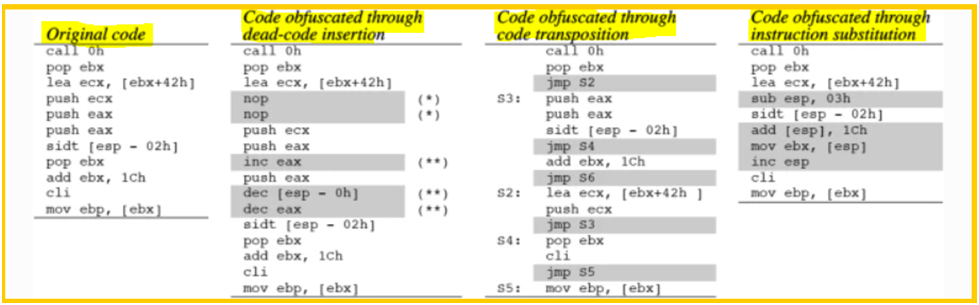
1-Dead-Code Insertion:
A dead-code insertion is a simple approach for changing the appearance of a program while maintaining its functionality. NOP is an example of such a command. The original code is easily obfuscated by inserting NOP instructions. Signature-based antivirus scanners, on the other hand, can resist this strategy by simply removing the unsuccessful instructions before analyzing them.
NOP instruction does nothing. Execution continues with the next instruction. No registers or flags are affected by this instruction. NOP is typically used to generate a delay in execution or to reserve space in code memory.
2-XOR:
This popular method of obfuscation conceals data so it cannot be analyzed. It does this by swapping the contents of two variables inside the code, such as:
- XOR EBX, EAX
- XOR EAX, EBX
- XOR EBX, EAX
3-Register reassignment:
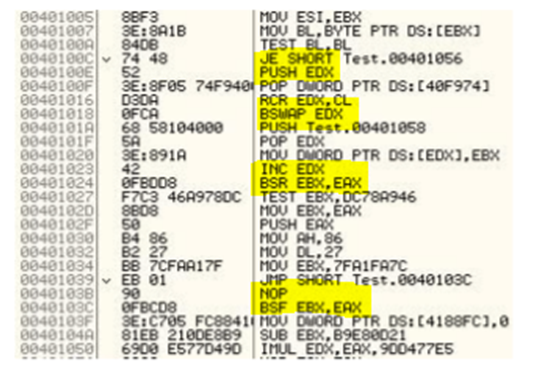
Register reassignment is another simple technique that switches registers from generation to generation while keeping the program code and its behavior the same. The below Figure describes how this technique is applied. In the below example, the original code is evolved by switching the registers. Note that wildcard searching can make this technique useless.
4-Subroutine Reordering:
Subroutine reordering obfuscates an original code by randomly rearranging its subroutines. This method can generate n! different variations, where n denotes the number of subroutines.
5-Instruction Substitution:
Instruction substitution evolves an original code by replacing some instructions with other equivalent ones. This technique can effectively change the code with a library of equivalent instructions.
6-Code Transposition:
Code transposition reorders the sequence of instructions in an original code without affecting the behavior of the code. This procedure can be accomplished in two ways:
- The first technique shuffles the instructions at random, then inserts unconditional branches or jumps to restore the original execution order. It is not difficult to defeat this method because the original program can be easily restored by removing the unconditional branches or jumps.
- The second method creates new generations by choosing and reordering the independent instructions that have no impact on one another. Because it is a complex problem to find the independent instructions, this method is hard to implement, but can make the cost of detection high.
7-Code integration:
Code integration was first spotted in the Zmist/Win95 virus (also known as Zmist), and it instructs malicious code to knit itself to the target program’s code. The malware decompiles the program into manageable bits, inserts itself between them, and then reassembles the injected code into a new variant to use the technique.
8-Instruction Substitution:
Instruction substitution evolves an original code by replacing some instructions with other equivalent ones. This technique can effectively change the code with a library of equivalent instructions.
9-Base64:
Base64 is another well-known obfuscation technique used by adversaries. It’s essentially a 64-character encoding scheme, with the padding character being the = (equal) sign. The alphabet also includes the letters a-z, A-Z, + and /, and 0-9 characters. The encoding works by stringing together three characters to generate a 24-bit string, which is then broken down into four 6-bit chunks, each of which is translated into one of the Base64 characters.
10-Packers:
In some situations, the entire program is obfuscated to prevent the malware code from being detected until it is placed into memory. This is accomplished with the aid of software that compresses an executable to make it smaller. The compressed executable is then packaged inside the code required to decompress itself during runtime. The decompression procedure assures that the executive file does not resemble its original state.
SolarWinds attack with Obfuscation technique:
- The attackers planted a backdoor in software upgrades for the Orion platform using Sunburst malware, which integrated obfuscation, machine learning, and AI capabilities. To hide their activities and get around defences, they tampered with audit logs, removed files and program after use, and faked activity to make it appear as though they were legitimate network applications.
- The attack on the supply chain is said to have gone unnoticed for over a year. Until users downloaded the compromised updates, the malware embedded in the Orion code remained dormant and unnoticed. It subsequently moved undetected throughout the network, infecting a long list of Orion users.
Conclusion:
Hackers use a variety of ways to break into IT systems. Malware obfuscation is a highly reliable technique that everyday adversaries can do little about. The above techniques can be used to obfuscate malicious codes to evade antivirus. Keeping an eye on the above techniques while analyzing the malware will be more helpful.



































