Cybersecurity researchers have developed the zero-day bug in Microsoft Office, which could be exploited to obtain the execution of arbitrary code on affected Windows systems. The technique is used through MSDT (Microsoft Diagnostics Tool) and Microsoft Office Utilities.
The vulnerability was revealed after an independent cybersecurity research team named nao_sec discovered a Word document (“05-2022-0438.doc“) uploaded to VirusTotal from an IP address in Belarus.
“It uses Word’s external link to load the HTML, then uses the ‘ms-msdt’ schema to run the PowerShell code,” the researchers noted in a series of tweets last week.
According to security researcher Kevin Beaumont, who called the error “Follina”, maldoc uses Word’s external template function to retrieve an HTML file from a server, which then uses the “ms-msdt: //” URI scheme. to get the malicious payload.
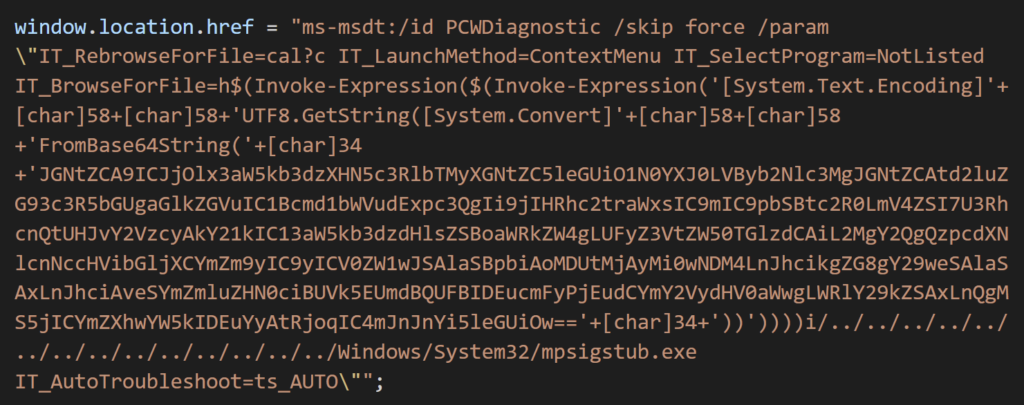
MSDT is the abbreviation for Microsoft Support Diagnostics Tool, a tool used for troubleshooting and collecting diagnostic data for analysis by support professionals for troubleshooting a problem.
“There’s a lot going on here, but the first problem is Microsoft Word is executing the code via msdt (a support tool) even if macros are disabled,” Beaumont explained.
“Protected Mode kicks in, although when you edit the document in RTF format, it runs without opening the document (via the Preview tab in Explorer), not to mention Protected Mode,” the researcher added.
In an analysis, nao_sec noticed that the HTML file that triggers the exploit comes from a now unreachable domain called “xmlformats [.] Com”.
IOC : C2: www.xmlformats[.]com (141[.]105.65.149)
A Rich Text Format (.RTF) file could trigger the call to this exploit using only the preview pane in Windows Explorer,” said John Hammond of Huntress Labs. “Like CVE-2021-40444, this increases the severity of this threat with not just a ‘single click’ to exploit, but potentially with a ‘zero click’ trigger.”
Multiple versions of Microsoft Office, including Office, Office 2016, and Office 2021, are said to be affected, although other versions are also expected to be vulnerable. Additionally, Richard Warren of the NCC Group managed to demonstrate an exploit on Office Professional Pro with the April 2022 patches running on a recent Windows 11 machine with the preview pane enabled.
Samir Said Diagnosis-Scripted Event ID 105 (logged by default, not noisy) could be useful for dfir (on tests I did its always generated) and captures msdt pid which can be correlated with other timeline events, also event ResolutionId property is pretty rare “RS_IncompatibleApplication_ID”
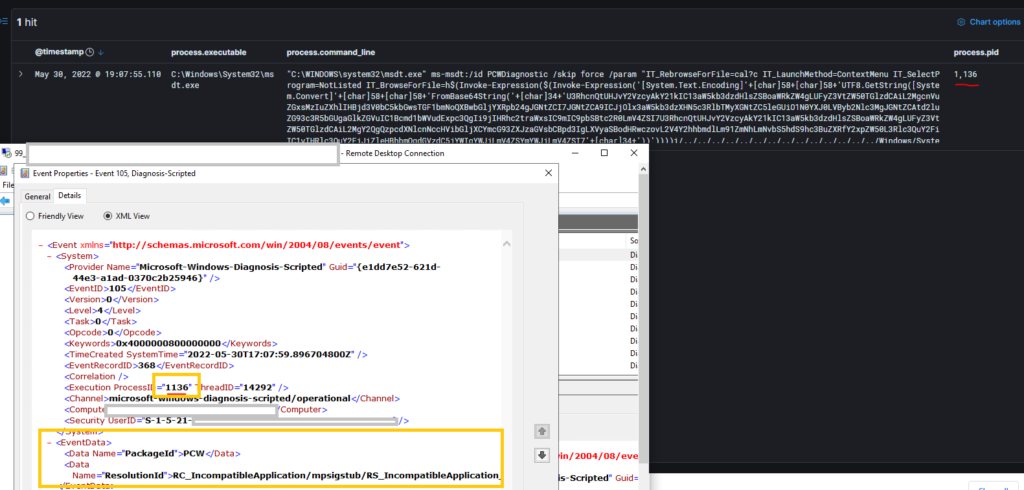
Detection Query can be:
Event ID = "105" AND Process_name "MSDT.exe"
The security hole, is now tracked as CVE-2022-30190.
CVE-2022-30190 ( IOCS ) :
52945af1def85b171870b31fa4782e52
8ee8fe6f0226e346e224cd72c728157c
6bcee92ab337c9130f27143cc7be5a55
f531a7c270d43656e34d578c8e71bc39
529c8f3d6d02ba996357aba535f688fc
d313002804198b5af1e0b537799be348
4a24048f81afbe9fb62e7a6a49adbd1faf41f266b5f9feecdceb567aec096784
Source :buffaloverflow
Detection Rules for Payloads & Process Names:
Microsoft Defender
DeviceProcessEvents | where ((ProcessCommandLine contains "WINWORD.EXE") and (ProcessCommandLine contains "msdt.exe") and (ProcessCommandLine contains "sdiagnhost.exe" or ProcessCommandLine contains "csc.exe" or ProcessCommandLine contains "PCWDiagnostic" or ProcessCommandLine contains "IT_ReBrowserForFile" or ProcessCommandLine contains "IT_BrowserForFile" or ProcessCommandLine contains "conhost.exe"))Splunk Alert[Doc Malware] alert.severity = 2 description = Detection (Rule ID: 74566a6a66aaasdq2ed) cron_schedule = 0 * * * * disabled = 1 is_scheduled = 1 is_visible = 1 dispatch.earliest_time = -60m@m dispatch.latest_time = now search = (source="WinEventLog:*" AND (CommandLine="*WINWORD.EXE*") AND (CommandLine="*msdt.exe*") AND (CommandLine="*sdiagnhost.exe*" OR CommandLine="*csc.exe*" OR CommandLine="*PCWDiagnostic*" OR CommandLine="*IT_ReBrowserForFile*" OR CommandLine="*IT_BrowserForFile*" OR CommandLine="*conhost.exe*")) alert.suppress = 0 alert.track = 1QradarSELECT UTF8(payload) from events where LOGSOURCETYPENAME(devicetype)='Microsoft Windows Security Event Log' and ("Process CommandLine" ilike '%WINWORD.EXE%') and ("Process CommandLine" ilike '%msdt.exe%') and ("Process CommandLine" ilike '%sdiagnhost.exe%' or "Process CommandLine" ilike '%csc.exe%' or "Process CommandLine" ilike '%PCWDiagnostic%' or "Process CommandLine" ilike '%IT_ReBrowserForFile%' or "Process CommandLine" ilike '%IT_BrowserForFile%' or "Process CommandLine" ilike '%conhost.exe%')GrayLog(CommandLine.keyword:*WINWORD.EXE* AND CommandLine.keyword:*msdt.exe* AND CommandLine.keyword:(*sdiagnhost.exe* *csc.exe* *PCWDiagnostic* *IT_ReBrowserForFile* *IT_BrowserForFile* *conhost.exe*))Sumologic(_sourceCategory=*windows* AND (CommandLine = "*WINWORD.EXE*") AND (CommandLine = "*msdt.exe*") AND (CommandLine = "*sdiagnhost.exe*" OR CommandLine = "*csc.exe*" OR CommandLine = "*PCWDiagnostic*" OR CommandLine = "*IT_ReBrowserForFile*" OR CommandLine = "*IT_BrowserForFile*" OR CommandLine = "*conhost.exe*"))Elastic Query:(process.command_line:*WINWORD.EXE* AND process.command_line:*msdt.exe* AND process.command_line:(*sdiagnhost.exe* OR *csc.exe* OR *PCWDiagnostic* OR *IT_ReBrowserForFile* OR *IT_BrowserForFile* OR *conhost.exe*))"Microsoft will need to patch it across all of its different product offerings, and security vendors will need robust detection and blocking," Beaumont said. We've reached out to Microsoft for comment and will update the story once we receive feedback. 156/1000
Reference:
https://thehackernews.com/2022/05/watch-out-researchers-spot-new.html



































