Security researchers say a new backdoor called Whisker Spy is being used in a campaign by a relatively new advanced threat actor tracked as Earth Fox, known for targeting individuals showing interest in North Korea.
The actor used a tried and tested method and picked victims from visitors to a pro North Korea website, a tactic known as a watering hole attack.
ALSO READ : Anatomy Of An Advanced Persistent Threat Group
Watering hole attack
According to Trend Micro, WhiskerSpy was delivered when visitors tried to watch videos on the website. The attacker compromised the website and injected a malicious script that asked the victim to install a video codec for the media to run.
To avoid suspicions, the threat actor modified a legitimate codec installer so that it ultimately loaded “a previously unseen backdoor” on the victim’s system.
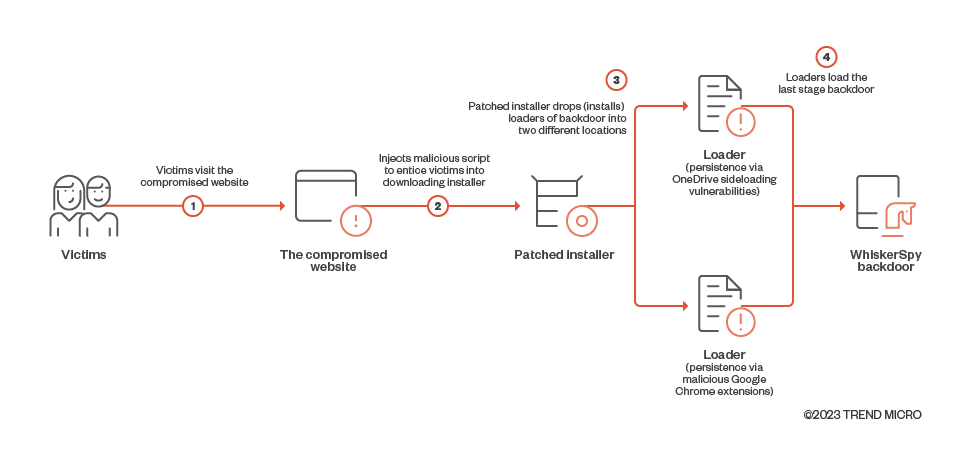
The researchers say that the threat actor targeted only visitors to the website with IP addresses from Shenyang, China; Nagoya, Japan; and Brazil.
ALSO READ: Latest IOCs – Threat Actor URLs , IP’s & Malware Hashes
It is likely that Brazil was used only for testing the watering hole attack using a VPN connection and the real targets were visitors from the two cities in China and Japan. Relevant victims would be served the fake error message below that prompts them to install a codec to watch the video.
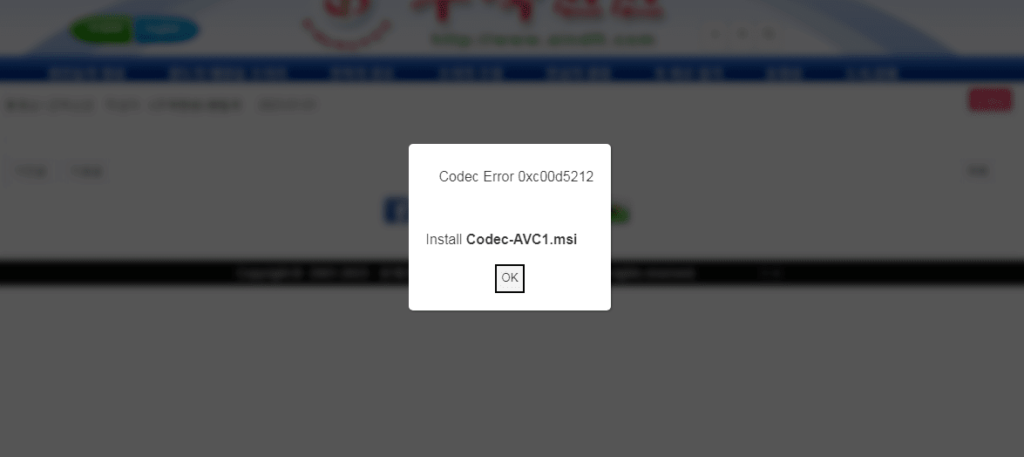
In reality, the codec is an MSI executable that installs on the victim’s computer shellcode that triggers a series PowerShell commands that lead to deploying the WhiskerSpy backdoor.
The researchers note that one persistence technique that Earth Kitsune used in this campaign abuses the native messaging host in Google Chrome and installs a malicious Google Chrome extension called Google Chrome Helper.
ALSO READ: RedLine Stealer returns with New TTPS – Detection & Response
The role of the extension is to allow execution of the payload every time the browser starts.
WhiskerSpy details
WhiskerSpy is the main payload used in the latest ‘Earth Kitsune’ campaign, giving remote operators the following capabilities:
- interactive shell
- download file
- upload file
- delete file
- list files
- take screenshot
- load executable and call its export
- inject shellcode into a process
The backdoor communicates with the command and control (C2) server using a 16-byte AES key for encryption.
WhiskerSpy periodically connects to the C2 for updates about its status and the server may respond with instructions for the malware, such as execute shell commands, inject code to another process, exfiltrate specific files, take screenshots.
Trend Micro has discovered an earlier version of WhiskerSpy that use the FTP protocol instead of HTTP for C2 communication. This older variant also checks for the presence of a debugger upon execution and informs the C2 with the appropriate status code.
Indicators of Compromise
Earth Kitsune samples (SHA-256) Detection Name Note ---------------------------------------------------------------- CE7016067C97421E3050FA8BD7F1950E0707E6DEEAC20003F5F30F1C58F435BC Trojan.JS.SLUB.A Delivery script 1C24D9013B3EAE373FC28D40F9E475E1DD22C228E8F1E539ED9229E21807839D Trojan.Win32.SLUB.AA Installer 076BA1135B2F9F4DBC38E306DC533AF71B311C1DC98788C18253448FCA096C46 Trojan.Win32.SLUB.AA Installer 371CFA10A7262438E5BC0694BA5628EB21E044DC8173710DF51826DAFA11E300 Trojan.Win32.SLUB.B Google Chrome persistence payload E01399D47CDA45F1AF496FA460F20620A5B08C39714875FE292A5FC3D1C7A215 Trojan.Win32.SLUB.B Google Chrome persistence payload 6F0A0AC477C73C2533A39CB3D8FBF45365761D11B7368460964A4572E91C5FCB Trojan.Win64.SLUB.B Google Chrome persistence payload C357E572DD7C618C54F8333313266A8A9CF07C1038D6B2F711CDBAE714BC2654 Trojan.JS.SLUB.A Google Chrome persistence payload 902902B5457C6945C2B3878521D23D05D448DE179D19761C718FB67C15A4BCC0 Trojan.Win64.SLUB.B Microsoft OneDrive persistence payload 20C214D58CCFB5AD797F1A02667078D182629AC7E157162566C123519E039D55 Trojan.Win32.SLUB.B Backdoor loader 3D62E122E31D7929E76633773D752B8BEE31462BB79CB5B8B7C6952341E93482 Trojan.Win32.SLUB.B Backdoor dropper 66C8E0ACFE030C4EEC474CD75C4D831601DAE3EF4E1CEF78B624DE3C346C186D Trojan.Win32.SLUB.B Backdoor dropper C78CB41F4FB4E5F5476EB2C1414F138643494C2B8ABE2CF539FAFC54199E2AEF Trojan.Win32.SLUB.B Backdoor dropper FBAC7B40A12970CDCC36F48945BEB83BF9461F14C59CB8106AD8E43E5D22A970 Trojan.Win32.SLUB.B Backdoor dropper 7365F661AD9E558FDD668D3563E0A1B85CCF1A543BE51CB942DB508F9CCBCF5E Trojan.Win32.SLUB.B Backdoor dropper 3D4107C738B46F75C5B1B88EF06F82A5779DDD830527C9BECC951080A5491F13 Backdoor.Win64.WHISPERSPY.A WhiskerSpy (64-bit version using HTTP) 84E9BCC055225BD50534147E355834325B97AD948C3A10D792928B48C56C1712 Backdoor.Win64.WHISPERSPY.A WhiskerSpy (64-bit version using HTTP) EFFA1AE32DBCF6BC64A5025BCA4F4C41572439B69EDD58B5F78952A407CEB5DF Backdoor.Win32.WHISPERSPY.A WhiskerSpy (32-bit version using FTP) Earth Kitsune infrastructure Note ---------------------------------------------------------------- microsoftwindow[.]sytes[.]net Delivery server domain updategoogle[.]servehttp[.]com WhiskerSpy HTTP C&C domain londoncity[.]hopto[.]org WhiskerSpy FTP C&C domain windowsupdate[.]sytes[.]net Related domain florida[.]serveblog[.]net Related domain googlemap[.]hopto[.]org Related domain liveupdate[.]servepics[.]com Related domain chromecast[.]hopto[.]org Related domain googlemap[.]serveblog[.]net Related domain selectorioi[.]ddns[.]net Related domain rs[.]myftp[.]biz Related domain
SOURCE: https://www.trendmicro.com/content/dam/trendmicro/global/en/research/23/b/earth-kitsune-delivers-new-whiskerspy-backdoor-via-watering-hole-attack/Earth_Kitsune_WhiskerSpy_iocs.txt
Detection & Response
CarbonBlack:
(process_name:(*powershell.exe OR *cmd.exe) AND process_cmdline:(*Invoke\-WebRequest\ http* OR *\*.jpg* OR *\*.php* OR *Get\-Content* OR *\\cmd.bin* OR *\-raw*) AND ((process_original_filename:*\\Users\\*\\AppData\\Local\\Microsoft\\OneDrive*) OR (process_name:*\\Users\\*\\AppData\\Local\\Microsoft\\OneDrive*)) AND ((process_original_filename:(*vcruntime140.dll OR *\*.dll)) OR (process_name:(*vcruntime140.dll OR *\*.dll))))
Elastic Query:
(process.executable.text:(*powershell.exe OR *cmd.exe) AND process.command_line.text:(*Invoke\-WebRequest\ http* OR *\*.jpg* OR *\*.php* OR *Get\-Content* OR *\\cmd.bin* OR *\-raw*) AND file.path.text:*\\Users\\*\\AppData\\Local\\Microsoft\\OneDrive* AND file.path.text:(*vcruntime140.dll OR *\*.dll))
GrayLog:
(Image:(*powershell.exe *cmd.exe) AND CommandLine:(*Invoke\-WebRequest\ http* **.jpg* **.php* *Get\-Content* *\\cmd.bin* *\-raw*) AND FileName:*\\Users\*\\AppData\\Local\\Microsoft\\OneDrive* AND FileName:(*vcruntime140.dll **.dll))
Microsoft Sentinel:
SecurityEvent | where EventID == 1 | where ((NewProcessName endswith @’powershell.exe’ or NewProcessName endswith @’cmd.exe’) and (CommandLine contains @’Invoke-WebRequest http’ or CommandLine contains @’*.jpg’ or CommandLine contains @’*.php’ or CommandLine contains @’Get-Content’ or CommandLine contains @’\cmd.bin’ or CommandLine contains @’-raw’) and TargetFilename contains @’\Users\*\AppData\Local\Microsoft\OneDrive’ and (TargetFilename endswith @’vcruntime140.dll’ or TargetFilename endswith @’*.dll’))
Microsoft Defender:
DeviceProcessEvents | where ((FolderPath endswith @’powershell.exe’ or FolderPath endswith @’cmd.exe’) and (ProcessCommandLine contains @’Invoke-WebRequest http’ or ProcessCommandLine contains @’*.jpg’ or ProcessCommandLine contains @’*.php’ or ProcessCommandLine contains @’Get-Content’ or ProcessCommandLine contains @’\cmd.bin’ or ProcessCommandLine contains @’-raw’) and FolderPath contains @’\Users\*\AppData\Local\Microsoft\OneDrive’ and (FolderPath endswith @’vcruntime140.dll’ or FolderPath endswith @’*.dll’))
Splunk:
source=”WinEventLog:*” AND ((Image=”*powershell.exe” OR Image=”*cmd.exe”) AND (CommandLine=”*Invoke-WebRequest http*” OR CommandLine=”**.jpg*” OR CommandLine=”**.php*” OR CommandLine=”*Get-Content*” OR CommandLine=”*\\cmd.bin*” OR CommandLine=”*-raw*”) AND (FileName=”*\\Users\*\\AppData\\Local\\Microsoft\\OneDrive*”) AND (FileName=”*vcruntime140.dll” OR FileName=”**.dll”))
Sumo Logic:
((_sourceCategory=*windows* AND (Image=*powershell.exe OR Image=*cmd.exe) AND (CommandLine=*Invoke-WebRequest http* OR CommandLine=**.jpg* OR CommandLine=**.php* OR CommandLine=*Get-Content* OR CommandLine=*\cmd.bin* OR CommandLine=*-raw*) AND (((\Users\ AND \AppData\Local\Microsoft\OneDrive))) AND (vcruntime140.dll OR .dll)))
Qradar:
SELECT UTF8(payload) FROM events WHERE LOGSOURCETYPENAME(devicetype)=’Microsoft Windows Security Event Log’ AND (“Image” ILIKE ‘%powershell.exe’ OR “Image” ILIKE ‘%cmd.exe’) AND (“Process CommandLine” ILIKE ‘%Invoke-WebRequest http%’ OR “Process CommandLine” ILIKE ‘%*.jpg%’ OR “Process CommandLine” ILIKE ‘%*.php%’ OR “Process CommandLine” ILIKE ‘%Get-Content%’ OR “Process CommandLine” ILIKE ‘%\cmd.bin%’ OR “Process CommandLine” ILIKE ‘%-raw%’) AND “Filename” ILIKE ‘%\Users\*\AppData\Local\Microsoft\OneDrive%’ AND (“Filename” ILIKE ‘%vcruntime140.dll’ OR “Filename” ILIKE ‘%*.dll’)
FireEye:
(metaclass:`windows` process:[‘*powershell.exe’, ‘*cmd.exe’] args:[‘*Invoke-WebRequest http*’, ‘**.jpg*’, ‘**.php*’, ‘*Get-Content*’, ‘*\\cmd.bin*’, ‘*-raw*’] filename:[‘*\\Users\\*\\AppData\\Local\\Microsoft\\OneDrive*’] filename:[‘*vcruntime140.dll’, ‘**.dll’])
Securonix:
index = archive AND (rg_functionality = “Microsoft Windows” AND ((@customstring54 ENDS WITH “powershell.exe” OR @customstring54 ENDS WITH “cmd.exe”) OR (@destinationprocessname ENDS WITH “powershell.exe” OR @destinationprocessname ENDS WITH “cmd.exe”)) AND (@resourcecustomfield3 CONTAINS “Invoke-WebRequest http” OR @resourcecustomfield3 = “**.jpg*” OR @resourcecustomfield3 = “**.php*” OR @resourcecustomfield3 CONTAINS “Get-Content” OR @resourcecustomfield3 CONTAINS “\cmd.bin” OR @resourcecustomfield3 CONTAINS “-raw”) AND (rawevent = “*\Users*\AppData\Local\Microsoft\OneDrive*”) AND (rawevent CONTAINS “vcruntime140.dll” OR rawevent = “**.dll*”))
Source: https://www.trendmicro.com/en_us/research/23/b/earth-kitsune-delivers-new-whiskerspy-backdoor.html & https://www.bleepingcomputer.com



































