NjRAT, also called Bladabindi and Njw0rm is a remote access trojan that is used to remotely control infected machines. Because of its availability, excess of online tutorials, plenty of information, and a robust core feature set along with several implemented evading techniques made njRAT is one of the most widely used RATs in the world.
General Information about njRAT
njRAT trojan is built on the .NET framework. This RAT gives hackers the ability to control the victim’s PC remotely. njRAT allows attackers to activate the webcam, log keystrokes, and steal passwords from web browsers as well as multiple desktop apps.
In addition, the malware gives hackers access to the command line on the infected machine. It allows to kill processes as well as remotely execute and manipulate files. On top of that, njRAT is capable of manipulating the system registry. When infected, Bladabindi trojan will collect several bits of information about the PC that it got into, including the name of the computer, operating system number, country of the computer, usernames, and OS version.
Also Read: Latest IOCs – Threat Actor URLs , IP’s & Malware Hashes
Also, this malware is able to target cryptocurrency wallet applications and steal cryptocurrency from PCs. For example, it is known to be able to grab bitcoins and even access credit card information which sometimes can be stored in crypto apps as a means to purchase cryptocurrency.
After infecting a computer the malware uses a variable name and copies into %TEMP%, %APPDATA%, %USERPROFILE%,%ALLUSERSPROFILE% or %windir% – a behavior not uncommon for this time of malware. It can also copy itself into <any string>.exe, to ensure that it will be activated every time the victim switches on their computer.
Attack Details
Infected machines will have suspicious files getting copied to the temp directory "C:\Users\admin\AppData\Local\Temp\lolpoc.exe", To achieve persistence, Threat actors leverage windows legitimate utility Netsh.exe to allow their programs in the firewall.
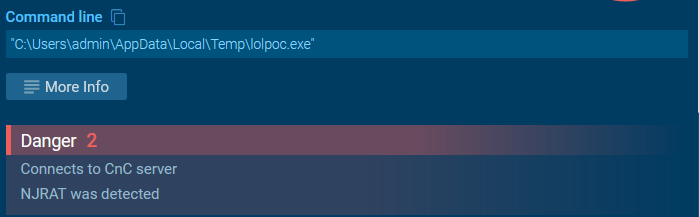
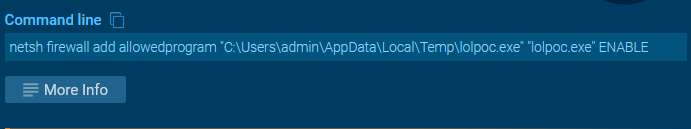
Allowed program in netsh shell will grand access to attackers to activate the webcam, log keystrokes, and steal passwords from web browsers as well as multiple desktop apps.
Also Read: Phishing with Reverse Tunnels and URL Shorteners – Detection & Response
The second stage downloader. It connects to a hard-coded Discord CDN cdn.discordapp.com endpoint and downloads data.

This second stage loads into the memory and is responsible for decrypting the final payload, which is stored as a PE resource. It includes antivirus evasion, persistence setup, and injection of the final payload to a newly initiated process.
Also Read: Cooking Malicious Documents with Cyberchef – Detect & Respond
Indicator of Compromise
3.124.142.205
185.204.1.236
149.154.154.78
3.134.39.220
3.127.181.115
3.134.125.175
91.109.178.2
3.67.112.102
3.64.4.198
3.133.207.110
3.125.188.168
91.192.100.37
195.123.221.123
37.1.217.131
147.185.221.224
3.141.142.211
File hashes:
da8d01720b72d4924634030496665779624e5fbb291a6346bf54cb61beec5020
cf3d42642c7f3867849464351e2cdacab7b5c73f50f0ac7075583a8a210d6675
ad640f1084f2228aede77674dfa5078844fd4163694234021bfe72b73f30f060
ebe8e001726ccb5df470d650b4afd2fe6d4ae087e8aba9e1bcd18bbd217022d6
0f6b5e0bd39fa3eb5e33212d1c180bacf9441a908986bd5e36eadaddb22e80ea
f84b23d6d06956922d90093c2cc18f6cb23564285fc4b482f41eb5b360cb5874
0c649e8575cdd0baf7ffcbe08c1e906a0d6adcc3e7612c86ebdd93882854ddee
633d16bb4f3465574d0e020165fb4d3f2a2c94e440c521d8dc6034f9d369a989
7cfc8fdc124e034579cfd665c38fc3f66de2fa8e47350e09f8e91f6000f96b3f
add358e91095ffee6f3232965ecc4fdee386fea3a5e9b7bc540434aece1da3d1
7b6f26c5cdec1f5dc21c46cf26889ce1349629944fd45a684c94af1174c201df
83667a9a99db9e89d9b0d39b0cd2fb94c59085f4d3b7b3c37206228f22bdc081
9425d9099bf4dd1cd2c41434fe45de21ac1659110d121342849077eb6770437a
3ec0a49b394c159a2a2833fc5009948abf485d3328d37931c1a8e0469c784824
MD5: 10666134095758789aa4d120d232945d
Domains:
sanpedro1[.]duckdns.org
Detection & Response:
Splunk:
source="WinEventLog:*" AND (((Image="*\\netsh.exe") AND (CommandLine="*firewall add allowedprogram*" OR CommandLine="*ENABLE*") AND (Image="*.exe") AND (CommandLine="*\\Users\\Admin\\AppData\\Local\\Temp\\*")) OR ((Image="*powershell.exe") AND (CommandLine="*.ps1*")))Qradar:
SELECT UTF8(payload) from events where LOGSOURCETYPENAME(devicetype)='Microsoft Windows Security Event Log' and ((("Image" ilike '%\netsh.exe') and ("Process CommandLine" ilike '%firewall add allowedprogram%' or "Process CommandLine" ilike '%ENABLE%') and ("Image" ilike '%.exe') and ("Process CommandLine" ilike '%\Users\Admin\AppData\Local\Temp\%')) or (("Image" ilike '%powershell.exe') and ("Process CommandLine" ilike '%.ps1%')))Elastic Query:
((process.executable:*\\netsh.exe AND process.command_line:(*firewall\ add\ allowedprogram* OR *ENABLE*) AND process.executable:*.exe AND process.command_line:*\\Users\\Admin\\AppData\\Local\\Temp\\*) OR (process.executable:*powershell.exe AND process.command_line:*.ps1*))Arcsight:
(((((destinationProcessName CONTAINS "*\\netsh.exe" OR sourceProcessName CONTAINS "*\\netsh.exe" OR deviceProcessName CONTAINS "*\\netsh.exe")) AND ((deviceCustomString1 CONTAINS "*firewall add allowedprogram*" OR deviceCustomString1 CONTAINS "*ENABLE*" OR destinationServiceName CONTAINS "*firewall add allowedprogram*" OR destinationServiceName CONTAINS "*ENABLE*")) AND ((destinationProcessName CONTAINS "*.exe" OR sourceProcessName CONTAINS "*.exe" OR deviceProcessName CONTAINS "*.exe")) AND ((deviceCustomString1 CONTAINS "*\\Users\\Admin\\AppData\\Local\\Temp\\\\*" OR destinationServiceName CONTAINS "*\\Users\\Admin\\AppData\\Local\\Temp\\\\*"))) OR (((destinationProcessName CONTAINS "*powershell.exe" OR sourceProcessName CONTAINS "*powershell.exe" OR deviceProcessName CONTAINS "*powershell.exe")) AND ((deviceCustomString1 CONTAINS "*.ps1*" OR destinationServiceName CONTAINS "*.ps1*")))))CarbonBlack:
((process_name:*\\netsh.exe AND process_cmdline:(*firewall\ add\ allowedprogram* OR *ENABLE*) AND process_name:*.exe AND process_cmdline:*\\Users\\Admin\\AppData\\Local\\Temp\\*) OR (process_name:*powershell.exe AND process_cmdline:*.ps1*))Crowdstike:
(((ImageFileName="*\\netsh.exe") AND ((CommandLine="*firewall add allowedprogram*" OR CommandLine="*ENABLE*") OR (CommandHistory="*firewall add allowedprogram*" OR CommandHistory="*ENABLE*")) AND (ImageFileName="*.exe") AND ((CommandLine="*\\Users\\Admin\\AppData\\Local\\Temp\\*") OR (CommandHistory="*\\Users\\Admin\\AppData\\Local\\Temp\\*"))) OR ((ImageFileName="*powershell.exe") AND ((CommandLine="*.ps1*") OR (CommandHistory="*.ps1*"))))Fireeye:
(metaclass:`windows` ((process:`*\netsh.exe` args:[`firewall add allowedprogram`,`ENABLE`] process:`*.exe` args:`\Users\Admin\AppData\Local\Temp\\`) OR (process:`*powershell.exe` args:`.ps1`)))Graylog:
((Image.keyword:*\\netsh.exe AND CommandLine.keyword:(*firewall\ add\ allowedprogram* *ENABLE*) AND Image.keyword:*.exe AND CommandLine.keyword:*\\Users\\Admin\\AppData\\Local\\Temp\\*) OR (Image.keyword:*powershell.exe AND CommandLine.keyword:*.ps1*))Logpoint:
((Image IN "*\\netsh.exe" CommandLine IN ["*firewall add allowedprogram*", "*ENABLE*"] Image IN "*.exe" CommandLine IN "*\\Users\\Admin\\AppData\\Local\\Temp\\*") OR (Image IN "*powershell.exe" CommandLine IN "*.ps1*"))
Microsoft Defender:
DeviceProcessEvents | where (((FolderPath endswith @"\netsh.exe") and (ProcessCommandLine contains "firewall add allowedprogram" or ProcessCommandLine contains "ENABLE") and (FolderPath endswith ".exe") and (ProcessCommandLine contains @"\Users\Admin\AppData\Local\Temp\")) or ((FolderPath endswith "powershell.exe") and (ProcessCommandLine contains ".ps1")))Microsoft Sentinel:
SecurityEvent | where EventID == 4688 | where (((NewProcessName endswith @'\netsh.exe') and (CommandLine contains 'firewall add allowedprogram' or CommandLine contains 'ENABLE') and (NewProcessName endswith '.exe') and (CommandLine contains @'\Users\Admin\AppData\Local\Temp\')) or ((NewProcessName endswith 'powershell.exe') and (CommandLine contains '.ps1')))RSA Netwitness:
(((Image contains '\netsh\.exe') && (CommandLine contains 'firewall add allowedprogram', 'ENABLE') && (Image contains '.exe') && (CommandLine contains '\Users\\Admin\\AppData\\Local\\Temp\\\')) || ((Image contains 'powershell\.exe') && (CommandLine contains '.ps1')))Sumo Logic:
(_sourceCategory=*windows* AND ((((Image = "*\netsh.exe") AND (CommandLine = "*firewall add allowedprogram*" OR CommandLine = "*ENABLE*") AND (Image = "*.exe") AND (CommandLine = "*\Users\Admin\AppData\Local\Temp\\*")) OR ((Image = "*powershell.exe") AND (CommandLine = "*.ps1*")))))Google Chronicle:
((target.process.file.full_path = /.*\\netsh\.exe$/ and (target.process.command_line = /.*firewall add allowedprogram.*/ or target.process.command_line = /.*ENABLE.*/) and target.process.file.full_path = /.*\.exe$/ and target.process.command_line = /.*\\Users\\Admin\\AppData\\Local\\Temp.*/) or (target.process.file.full_path = /.*powershell\.exe$/ and target.process.command_line = /.*\.ps1.*/))Aws Opensearch:
((process.executable:*\\netsh.exe AND process.command_line:(*firewall\ add\ allowedprogram* OR *ENABLE*) AND process.executable:*.exe AND process.command_line:*\\Users\\Admin\\AppData\\Local\\Temp\\*) OR (process.executable:*powershell.exe AND process.command_line:*.ps1*))Source/Reference: https://app.any.run/tasks/7efe4ff4-4399-45ae-9c93-309c45017e98?_ga=2.6436657.2075942654.1657583694-2049819986.1657583694/
https://app.any.run/tasks/87103046-f561-47d9-8b1a-319ee95cabd4?_ga=2.2354227.2075942654.1657583694-2049819986.1657583694/