Security researchers are seeing improved use of reverse tunneling services with URL shorteners for large-scale phishing campaigns, making it difficult to stop malicious activity.
This practice differs from the general method of registering a domain with a hosting provider which may remove phishing sites in response to complaints. Using reverse tunnels allows an attacker to host a phishing page locally on their computer and route communication through a remote service. You can use the URL shortening service to generate as many new links as you want to avoid discovery.
THREAT
- Increased malicious use of reverse tunnel services like Ngrok, and URL shorteners like bit.ly, to launch large-scale phishing campaigns.
- Malicious sites are hosted from local machines that cannot be traced back to the actors.
- Primary targets are banks and their customers.
IMPACT
Data collected from phishing sites can be sold on the dark web.
● It can also be used to create fake bank accounts and cards.
● Many of the links are life only for 24 hours, making it difficult to track the actors.
● Loss of trust in banks impersonated by the sites.
MITIGATION
Real-time scans to identify and phishing domains, not just by name, but also by trademarks and images.
● Awareness among customers regarding malicious URLs.
● Policies to ensure that reverse tunnel service providers assist victims to takedown such sites.
Legitimate Services Abuse
Traditional phishing campaigns require threat actors to register domains with hosting providers. This meant that when a phishing domain was detected and reported to a hosting provider, they were required to take down the domain and cooperate with law enforcement to track threat actor groups. However, reverse tunnel service providers don’t currently have any such accountability. This makes it an especially
attractive channel for threat actors to launch large-scale campaigns while remaining anonymous
CloudSEK’s TRIAD (Threat Research & Information Analytics Division) researchers have performed an in-depth analysis of 500+ sites that were hosted and distributed using the popular reverse tunnel services and URL shorteners
Abused reverse tunnel services that CloudSEK found in their research are Ngrok, LocalhostRun, and Cloudflare’s Argo. They also saw Bit.ly, is.gd, and cutt.ly URL shortening services being more prevalent.
Also Read: Ngrok Threat Hunting: Detect Hackers at the End of the Tunnel
Modus Operandi
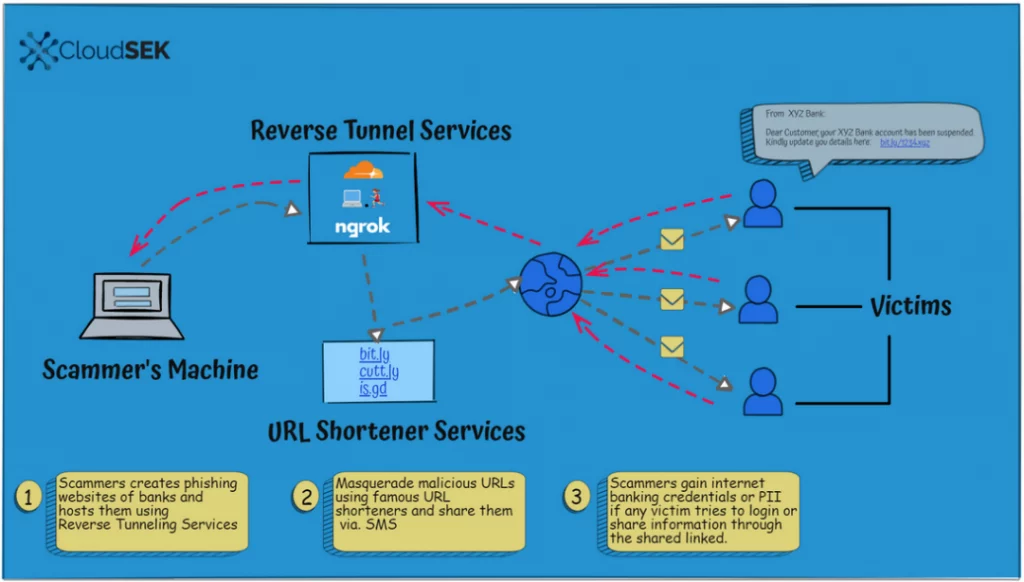
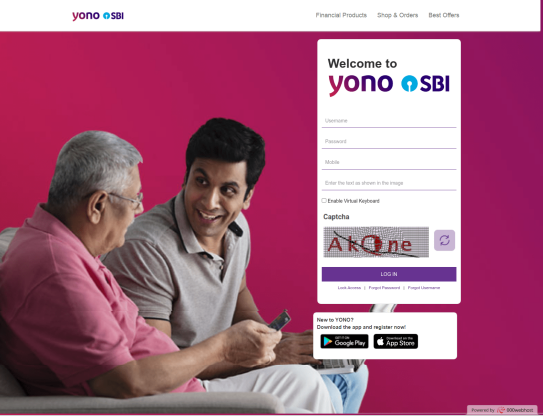
Step 1: A threat actor hosts phishing pages impersonating popular banks from their local machine. They then run reverse tunnel services to make the URLs available to users. The URLs typically have randomized names such as: http://776f-2401-4900-3625-4c7e-540a-4ac4-d992-7867[.]in[.]ngrok[.]io/.
Step 2: The URLs are then simplified using URL shorteners to something innocuous, such as: http://ibit[.]ly/oMwK.
Step 3: Threat actors distribute the simplified URLs via email, text messages, WhatsApp, Telegram, fake social media pages, etc.
Step 4: Victims who land on the phishing pages are directed to share sensitive information such as:
● Banking credentials
● Aadhaar card numbers
● PAN card numbers
Step 5: Since most reverse tunnel URLs are live only for 24 hours, threat actors keep the same template, but generate new URLs on a daily basis. Even if a URL is reported or blocked, threat actors can easily host another page, using the same template.
Also Read: Latest IOCs – Threat Actor URLs , IP’s & Malware Hashes
Overview of Popular Reverse Tunnel Services
Cloudflare Reverse Tunnel Service
● Cloudflare’s reverse tunnel, named Argo Tunnel, lets anyone expose a server or local system to the internet without opening any ports.
● The reverse tunnel service runs a lightweight process on the user’s server that is responsible for creating outbound tunnels to the Cloudflare network.
● Anyone with a Cloudflare account can use this service for free.
● Detailed tutorial and documentation is available on their official website regarding how to set up the Argo Tunnel on a local system.
● Example of a phishing domain hosted using Cloudflare:
○ Submitted URL: https://cutt[.]ly/UDbpGhs
○ Effective URL: http://ultimate-boy-bacterial-generates[.]trycloudflare[.]com/sbi/
Also Read: Densityscout – Entropy Analyzer for Threat Hunting and Incident Response
Localhost Reverse Tunnel Service
● localhost[.]run is a client-less tool that makes a locally running application available on the internet through a URL.
● This reverse tunnel uses SSH as a client, so no download is necessary to use the service without setting up an account.
● It is capable of forwarding HTTP traffic down to the locally hosted app and automatically adds encrypted HTTPS endpoints.This service comes with Freemium plans and detailed documentation.
● Example of a phishing domain hosted using Localhost:
○ Submitted URL: http://bit[.]ly/3pkBIUn
○ Effective URL: https://585928ab103a05[.]localhost[.]run/
Ngrok Reverse Tunnel Service
Ngrok is used to expose local servers behind NATs and firewalls to the public internet over a
secure reverse tunnel.
● This is a program that can be downloaded on a local machine and run to provide it the port of a network service, generally a web server.
● This service is used for running personal cloud services, hosting demo websites without deploying, for building webhooks, etc.
● It can create a public HTTPS URL for a website running locally on a development machine.
● This service also has Freemium plans that gives users the flexibility to use customized subdomains to End-to-End TLS Tunnels.
● Despite the core logic behind Cloudflare, LocalHost, and Ngrok reverse tunnels’ being the same, due to extensive misuse, Ngrok requires a registered account to host HTML content. And the traffic is redirected through the dynamically generated subdomain by the reverse tunnel services.
● Example of a phishing domain hosted using Localhost:
○ Submitted URL: http://ibit[.]ly/oMwK
○ Effective URL: http://776f-2401-4900-3625-4c7e-540a-4ac4-d992-7867[.]in[.]ngrok[.]io/
Also Read: What is Threat Intelligence – Importance , CTI Lifecycle & Pyramid of Pain
Detection & Response
Source Type == Proxy/Endpoint AND URl Contains ( '.ngrok.io' OR 'try.cloudflare.com' OR '*.localhost.run/' OR '*.lhr.run‘ ) AND URL in the list ( cutt.ly OR Bit.ly OR is.gd OR Any URL shortening services ) AND Time_spam = 1m
Source: https://cloudsek.com/whitepapers_reports/cybercriminals-exploit-reverse-tunnel-services-and-url-shorteners-to-launch-large-scale-phishing-campaigns/



































