ProcDOT is an interactive malware analysis tool created by Christian Wojner, offered as a free and open-source solution. Its primary objective is to aid malware analysts in comprehending and scrutinizing the actions of malicious software. The name “ProcDOT” stems from merging “Process” and “DOT,” which relates to the utilization of Graphviz DOT format for generating visual representations.
With its user-friendly interface, ProcDOT empowers analysts to effectively visualize and interpret the interactions between various processes, files, and registry entries, providing invaluable insights into the behavior of malware. Additionally, the tool offers features like an interactive timeline, string and file extraction, and displays of imports and exports, all contributing to a comprehensive and dynamic analysis process.
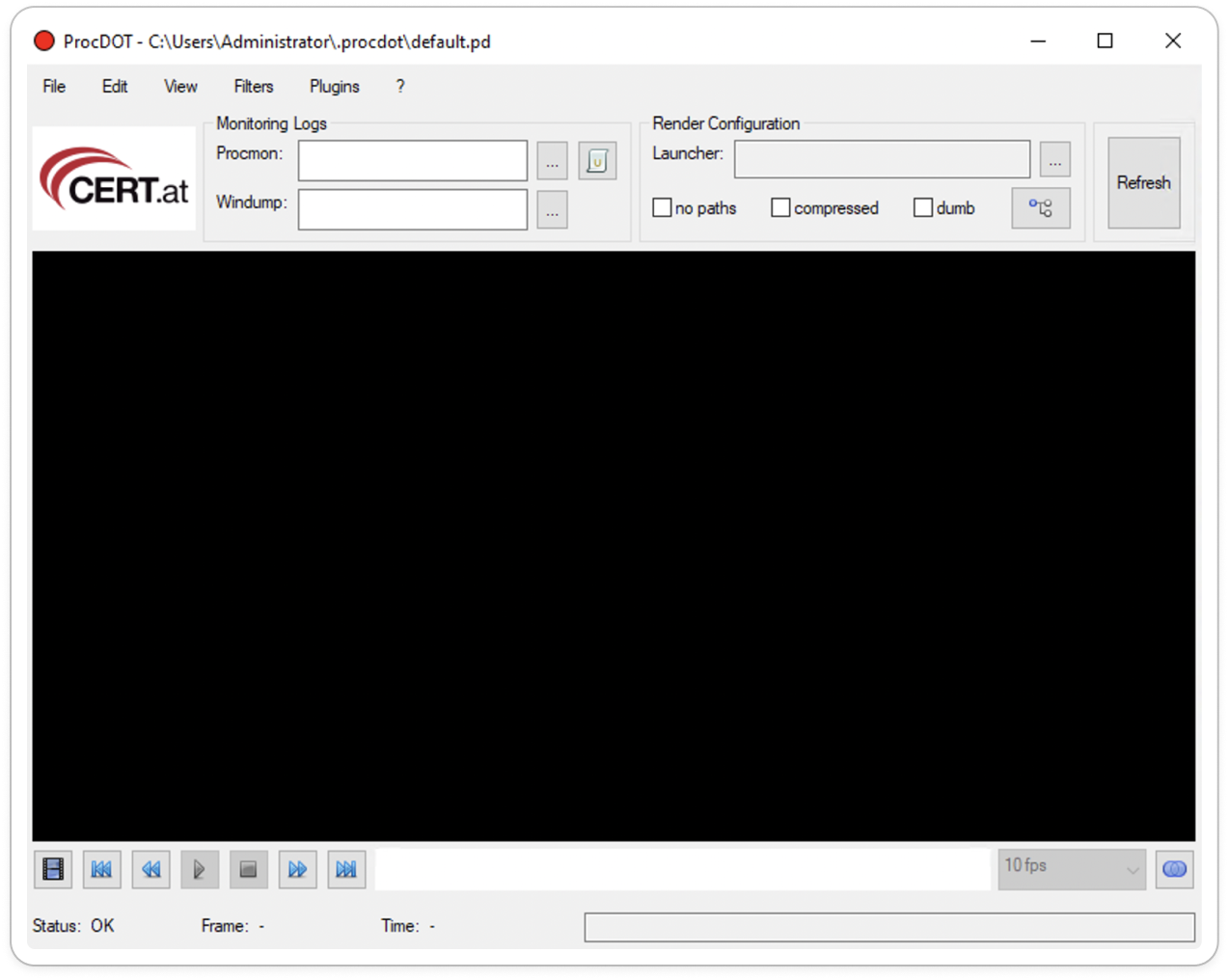
ProcDOT Main Window
Key features of ProcDOT include:
- ProcDOT facilitates an interactive process visualization, enabling analysts to explore malware behavior through a graph format. This visual representation highlights interactions between processes, files, and registry entries, enhancing comprehension of the malware’s actions.
- A dynamic interactive timeline is provided, showcasing the sequence of events and actions performed by the malware during its execution. Analysts can effortlessly track the malware’s behavior over time.
- Analysts can extract strings and files from the malware sample using ProcDOT. This valuable feature offers additional insights into the malware’s objectives and potential capabilities.
- ProcDOT displays the imported and exported functions of the analyzed malware, assisting analysts in identifying dependencies and potential functionalities.
- Streamlining the analysis process, ProcDOT offers a range of built-in filters, allowing analysts to focus on specific events or activities of interest, ensuring the discovery of crucial details.
- By incorporating context menus for graph objects, ProcDOT grants analysts swift access to supplementary information and analysis options, enhancing the efficiency of their investigations.
With these robust features at their disposal, ProcDOT empowers us to conduct comprehensive investigations, effectively visualize intricate malware behavior, and acquire valuable insights into the threats encountered.
Installation Guidance:
Let’s get hands-on practicality. Before we embark on our interactive journey, make sure to download the tool from the link provided as your specific platform such as Windows and Linux.
Once installed, proper configuration of additional software is necessary for ProcDOT to function correctly. This includes setting up the Graphviz-Suite and the executables for Windump/Tcpdump.
Graphviz-Suite: Windows and Linux (Use package manager to install).
Windump/Tcpdump: Windows and Linux (Use package manager to install).
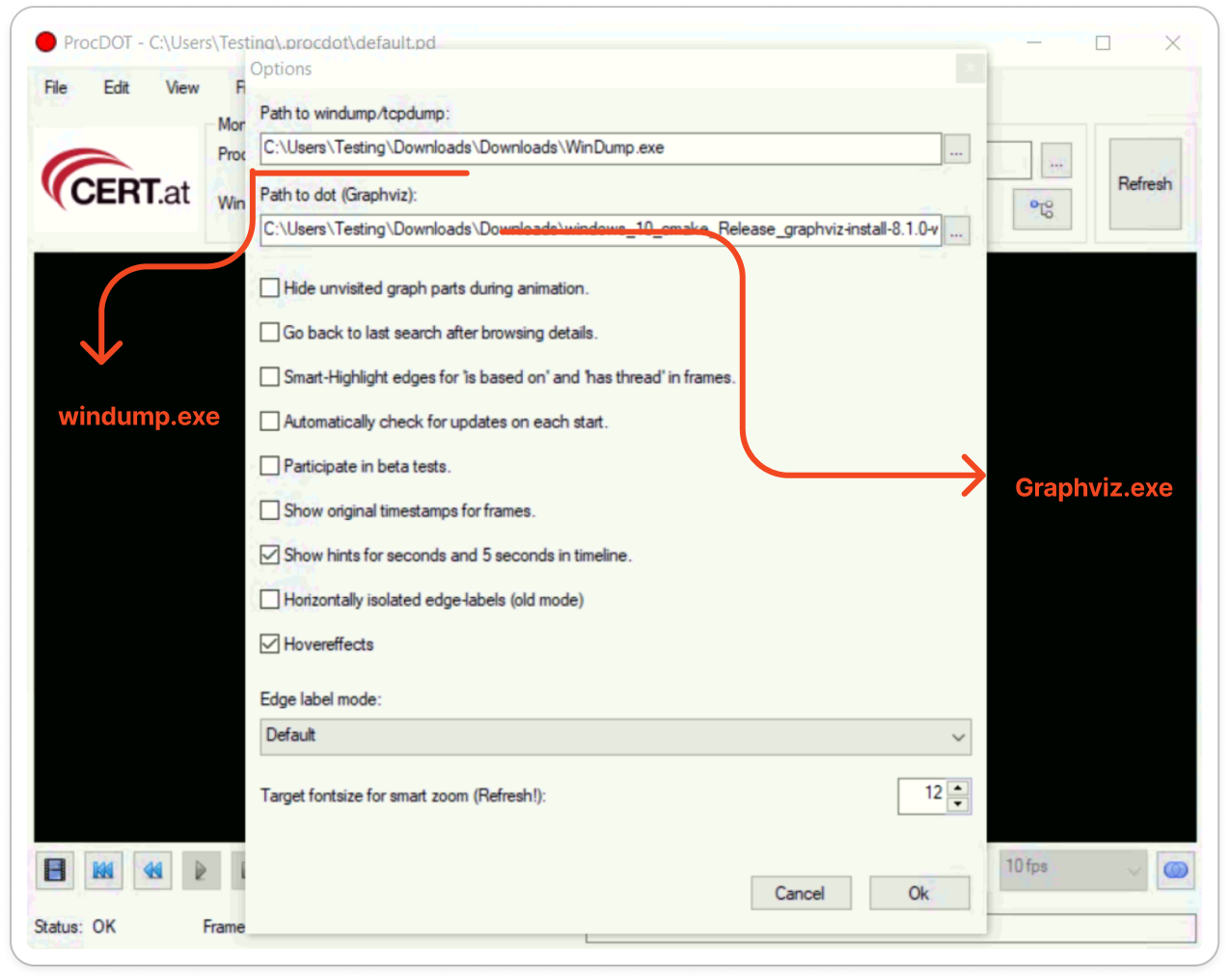
Edit > Options > Browse the path to import Windump and Graphviz
How does it work?
ProcDOT is a tool that looks at how programs run on Windows computers. It makes graphs and timelines to show how programs are connected and what they do. This helps investigators find unusual or dangerous activities. They can also focus on specific programs and share their findings with others.
Let’s dive in and explore its capabilities!!
Before running any malware samples, To ensure ProcDOT works correctly, open Procmon (Process Monitor) and make a few adjustments to its settings.

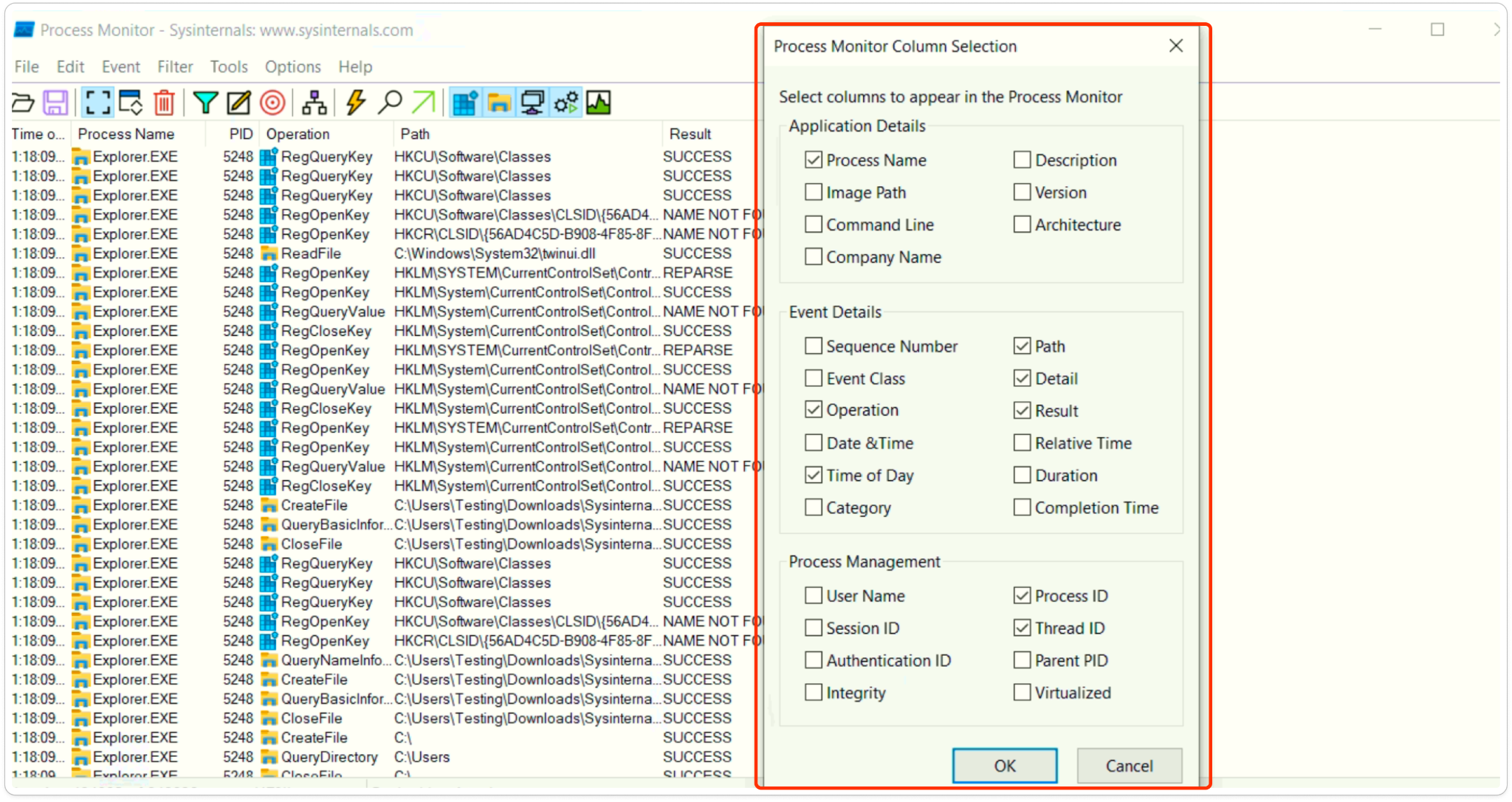
After that Open Procmon (Process Monitor) and Wireshark in separate windows. Once both are set up, execute the malware sample and save the captured data in Procmon (.CSV) and Wireshark (.TXT) formats.
Here are some snapshots to guide you through the process, and it’s straightforward to follow.
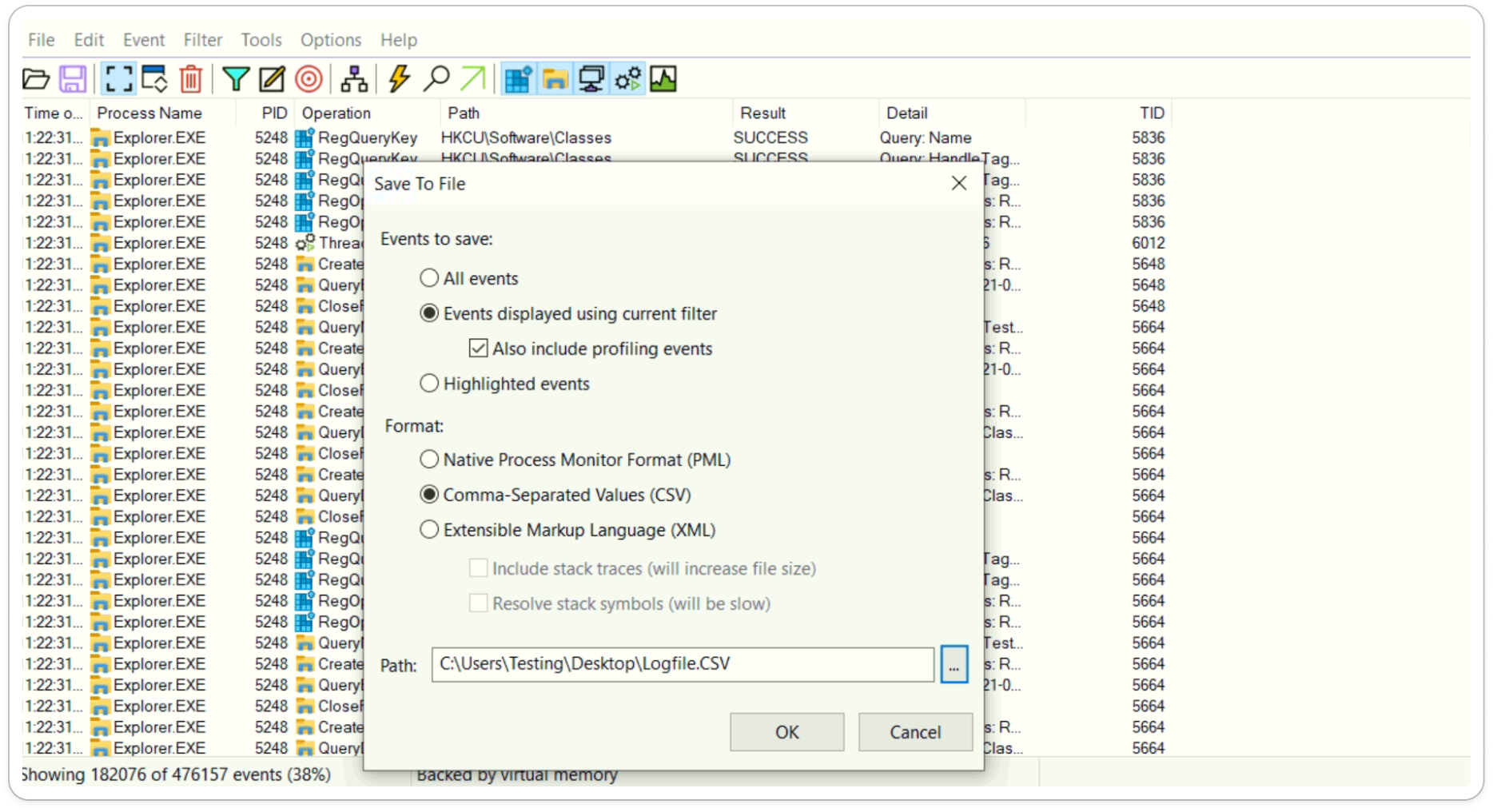
File > Save > Format (.CSV)
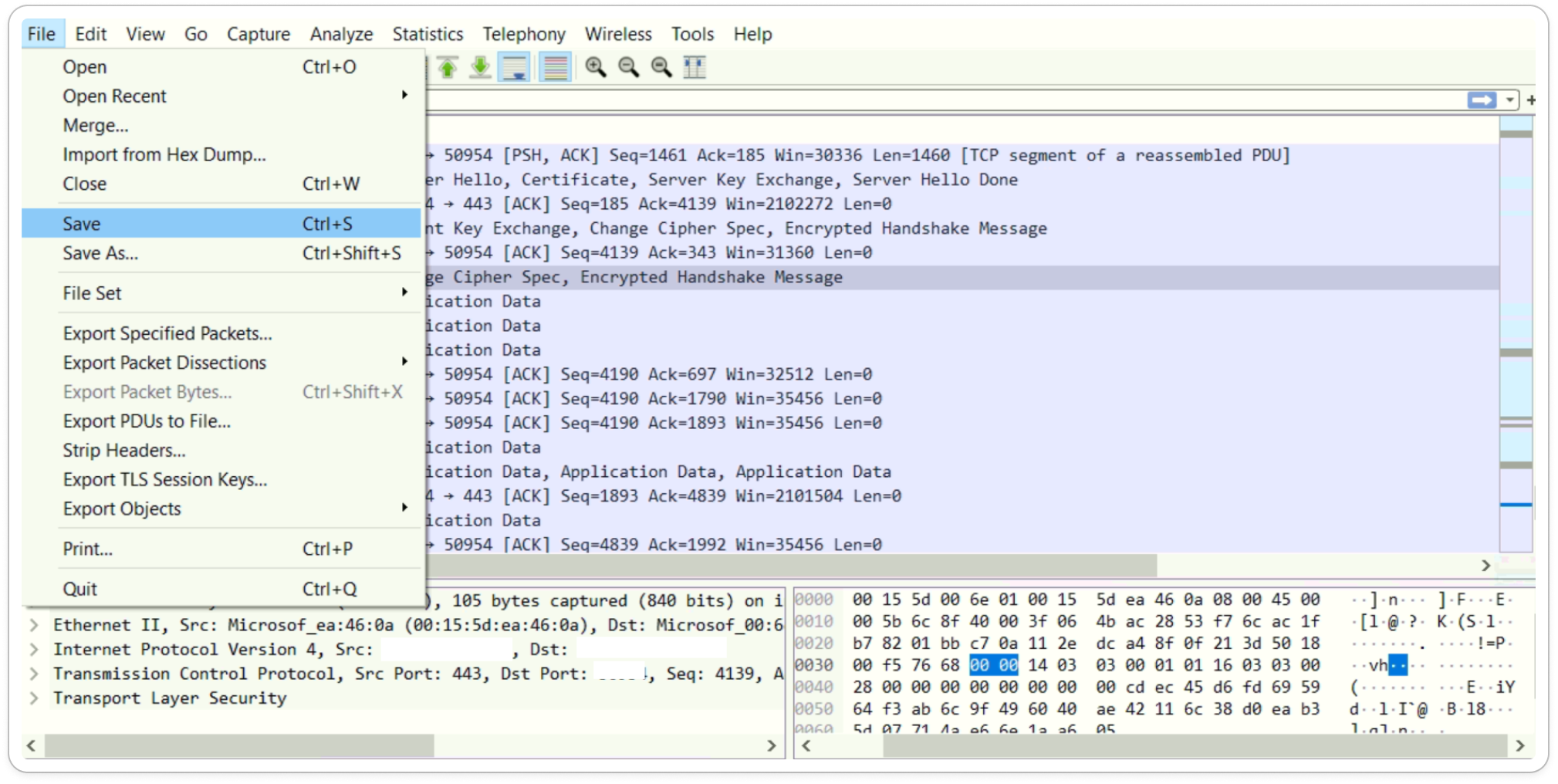
Wireshark (Packet Capture)
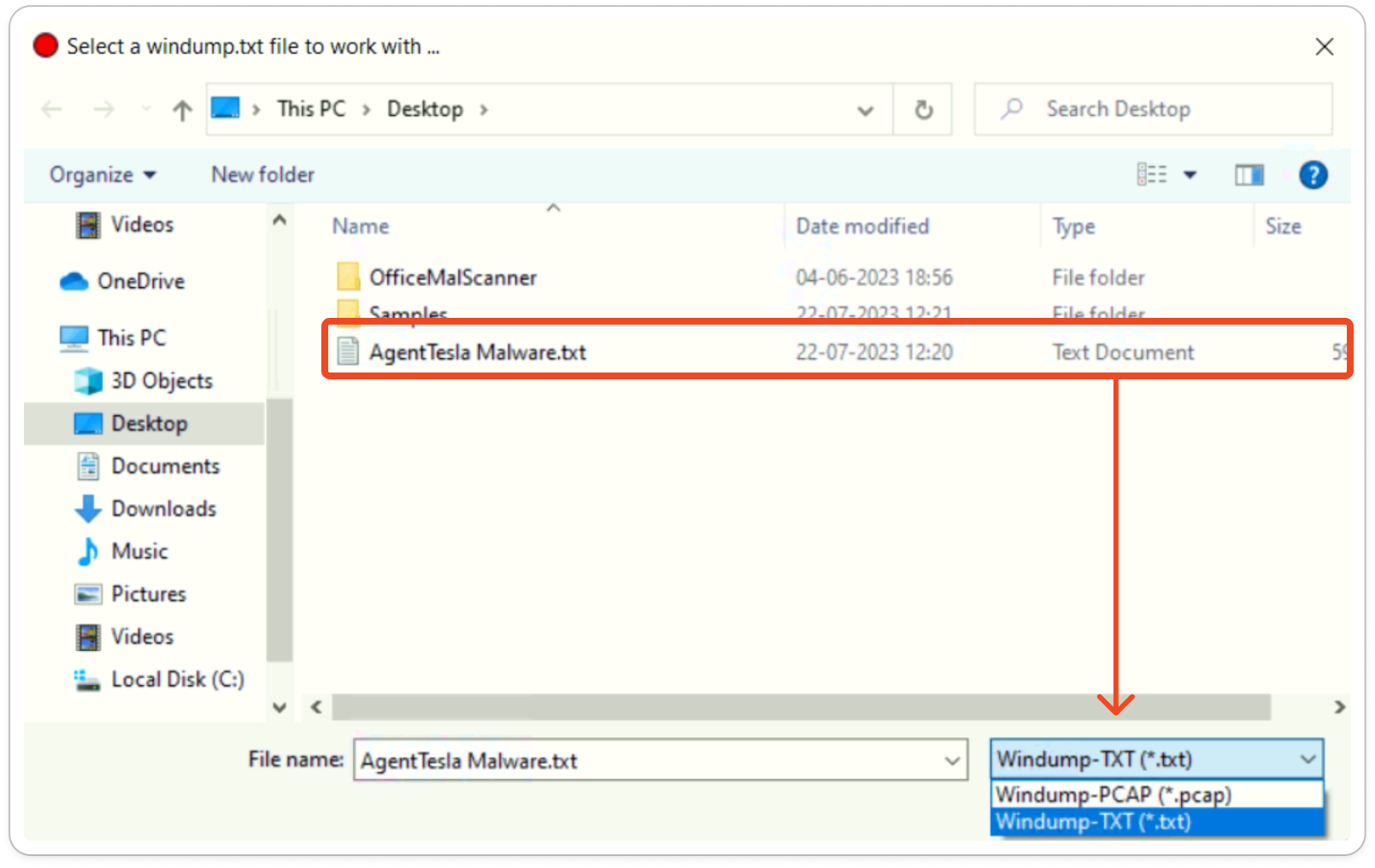
File > Save > Format (.TXT) Rather than .pcap
In Render Configuration, After launching the sample, click the “Refresh” button, and within a few seconds, the graph will be displayed.
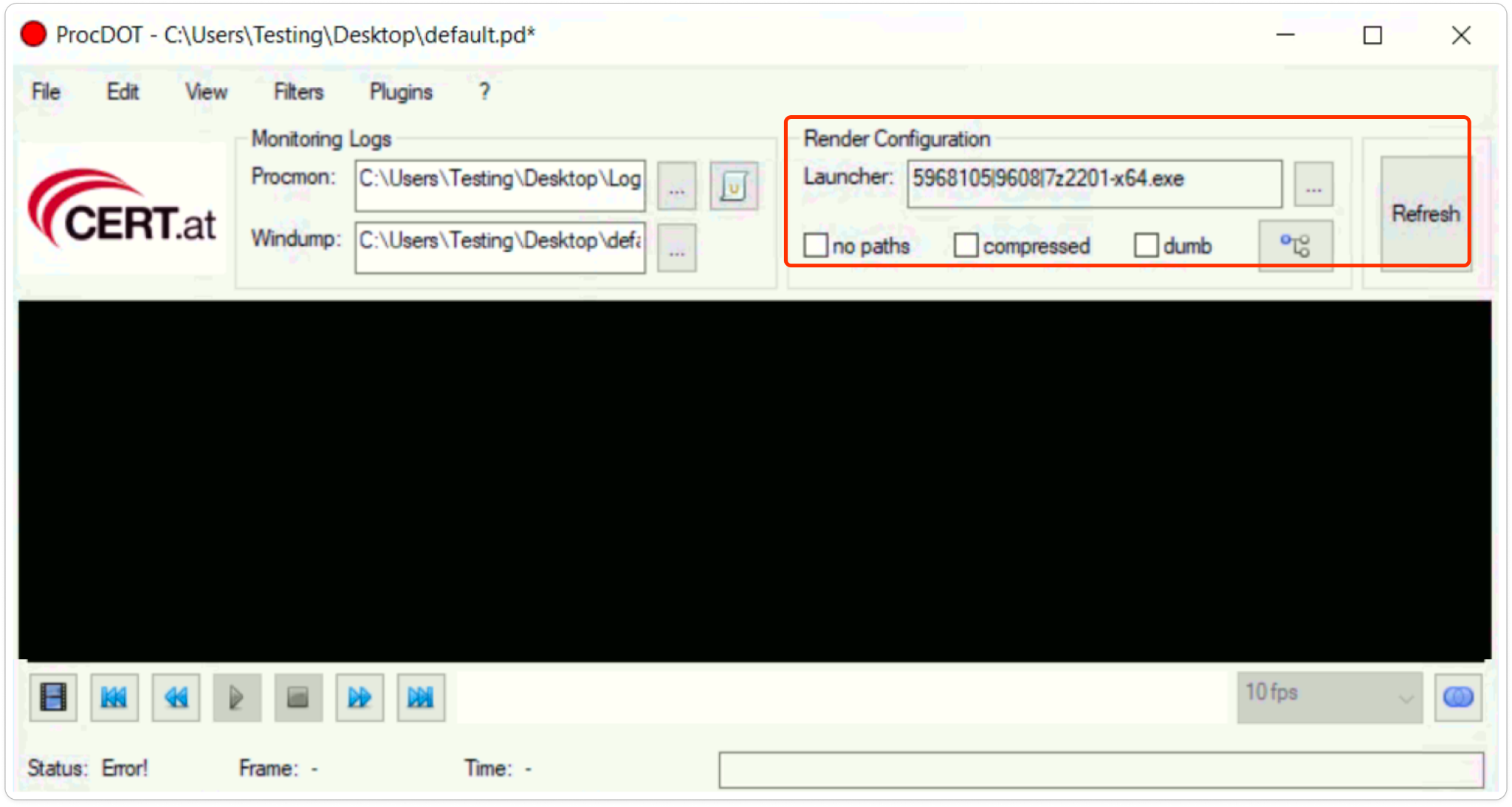
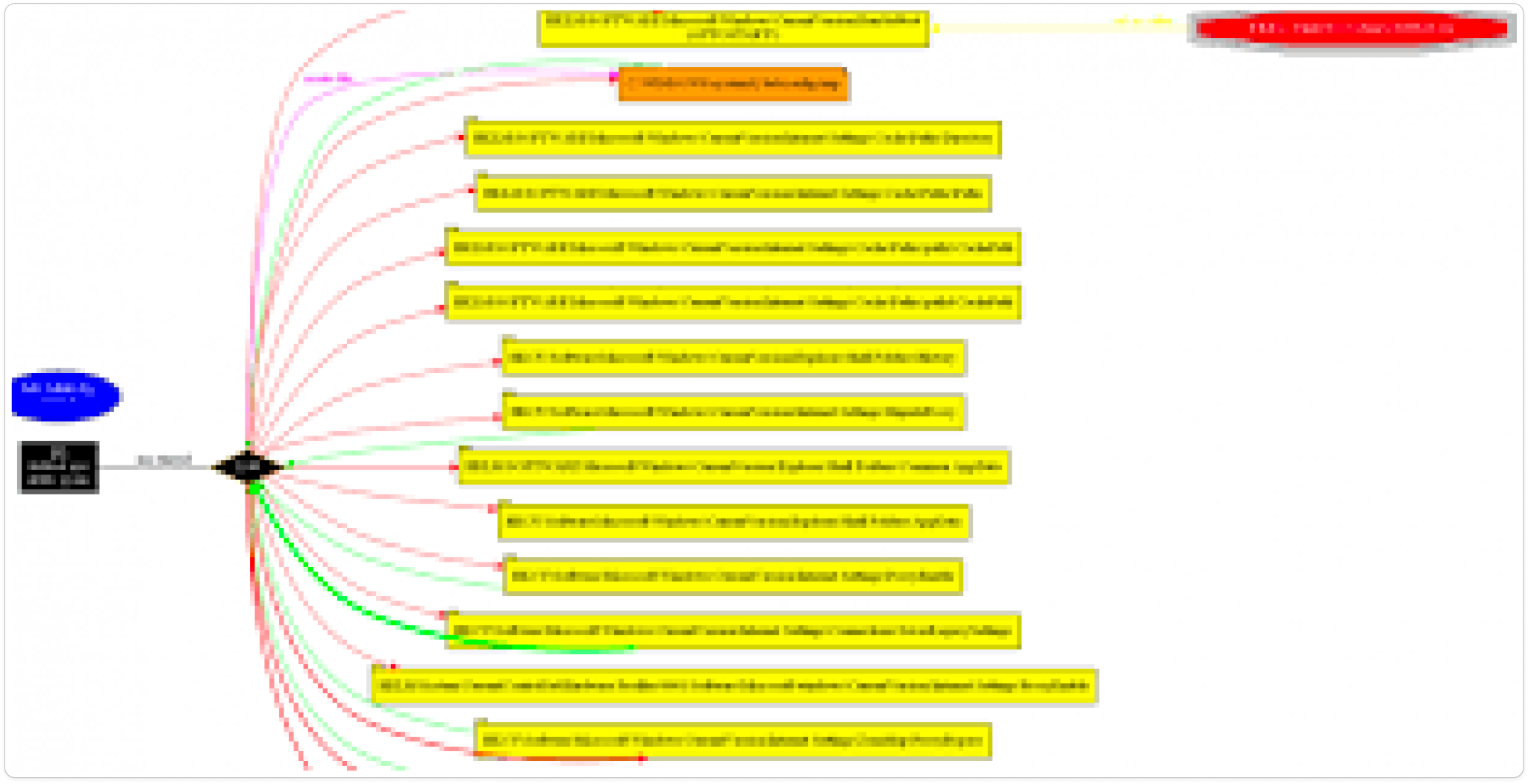
Conclusion:
ProcDOT proves to be a valuable tool for malware analysis. By visualizing process relationships and behaviors in Windows systems, it aids in identifying malicious activities and potential threats. Its interactive process graphs and timelines offer insights into the malware’s execution flow and behavior patterns. The ability to filter and inspect down into specific processes enhances the in-depth analysis, helping investigators to pinpoint critical details. Overall, ProcDOT streamlines the malware analysis process, empowering investigators to efficiently detect and mitigate security risks.
Keep learning and stay tuned for the next blog! PD



































