A week ago, VMware released updates to address the vulnerability (CVE-2022-31656) affecting VMware Workspace ONE Access, Identity Manager, and vRealize Automation. Multiple other flaws were patched the same day, including a high severity SQL injection flaw (CVE-2022-31659) that allows remote attackers to gain remote code execution.
The researcher who discovered two critical vulnerabilities in VMware ONE Workspace Access has released a proof-of-concept exploit for one of the bugs, an authentication bypass that can allow an attacker to gain admin privileges.
Also Read: New ‘DogWalk’ Windows zero-day gets free unofficial patches – Detection & Response
Today, VMware “confirmed malicious code that can exploit CVE-2022-31656 and CVE-2022-31659 in impacted products is publicly available” in an update to the original advisory.
The researcher posted the PoC for the vulnerability, along with a technical, step-by-step description of the bug and the exploitation process.
“VMware Workspace ONE Access, Identity Manager, and vRealize Automation contain an authentication bypass vulnerability affecting local domain users. A malicious actor with network access to the UI may be able to obtain administrative access without the need to authenticate,” the vulnerability advisory says.
In addition to the authentication bypass, Petrus Viet also discovered a remote code execution bug VMware ONE Access, which the company patched last week, as well. That flaw (CVE-2022-31659) is a SQL injection.
Also Read: Latest IOCs – Threat Actor URLs , IP’s & Malware Hashes
“A malicious actor with administrator and network access can trigger remote code execution. VMware has confirmed malicious code that can exploit CVE-2022-31659 in impacted products is publicly available,” the VMware advisory says.
Detection & Response:
- Check for the VMware logs with URL parameter which contains “/SAAS/t//;/auth/login/embeddedauthbroker/callback” and the HTTP method is POST. This is the indicator of successfully bypassed authentication.
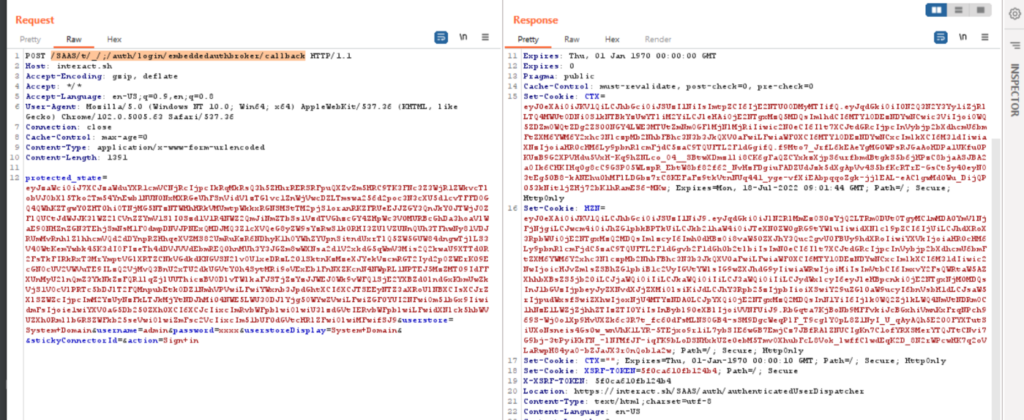
- The web request starts with the parameter “/SAAS/t//;/” with the HTTP method GET is the indicator of reading arbitrary files.
Also Read: Mapping MITRE ATT&CK with Window Event Log IDs
- Also, monitor for SQL and OS commands on the URL parameter. This is the indicator of remote code execution.
Still, this vulnerability is Not yet exploited in the wild. But it’s very important to take steps to apply the patch and mitigate it.



































