In the previous article, we have seen more TTP about QakBot alias Qbot and affiliated malwares (IceID, etc.) behaviors. This article will give us more insights about compilation of Qbot TTPs and the recent phishing campaign which they carried out to deploy ransomware on many B2B organizations.
TTP Compilation:
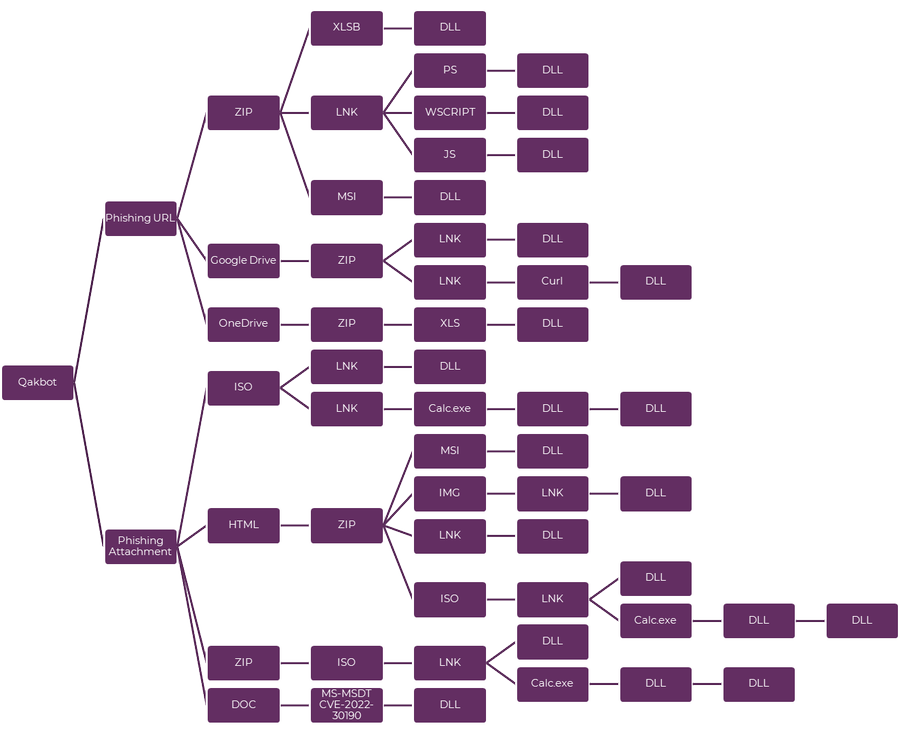
Qbot mode of conducting phishing campaigns are in 2 ways
- Phishing URL
- Phishing Attachment
Phishing URL contains – ZIP, Google Drive link and One Drive link
Phishing Attachment contains – ISO, HTML, ZIP, IMG, DOC, CVE-2022-30190
Irrespective of the above ways, the final payload to deploy the ransomware by the execution of .lnk file followed by .dll implantation.
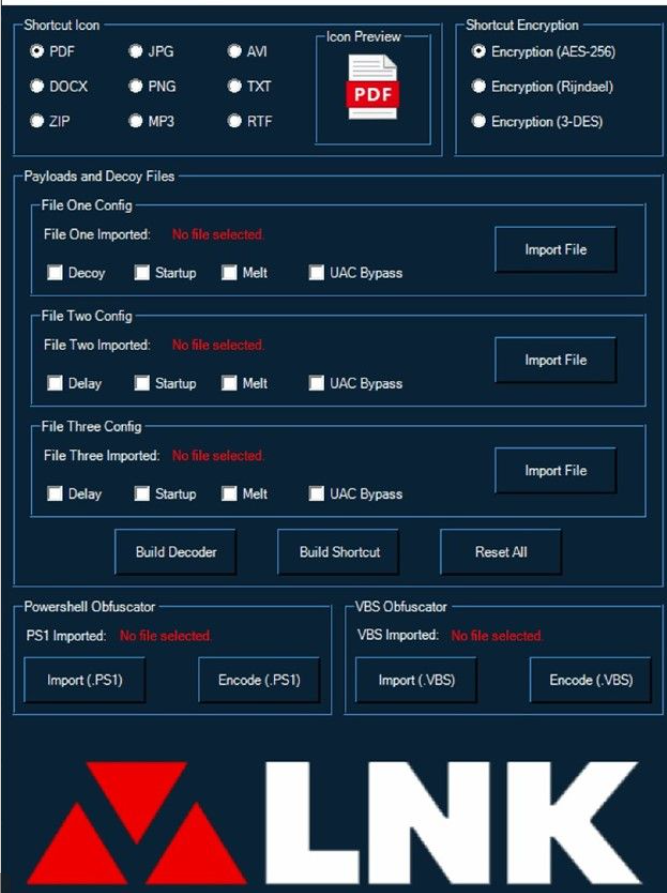
LNK file creation
The TA570 Oakboat (also known as Qbot), IcedID, AsyncRAT, and the newest strain of Emotet are the malware families that use LNK-based distribution the most frequently. Malicious Word documents utilizing the CVE-2022-30190 (Follina) zero-day vulnerability in the Microsoft Support Diagnostic Tool were also part of the most recent Qakbot dissemination campaign (MSDT).
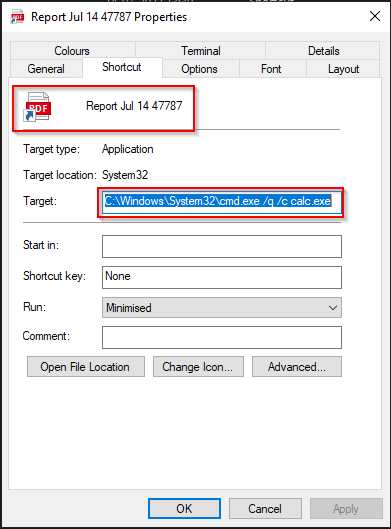
To trick antivirus software and endpoint security programs, the bad guys combine infected LNK files with ISO (through extension spoofing). It is intriguing to see how well-known industrial products can’t accurately recognize and evaluate them.
These files frequently have a professional appearance and occasionally share an icon with an already downloaded programs or document. When malicious code is included into LNK files (for instance, in a PowerShell scenario), the payload can be executed on the target computer.
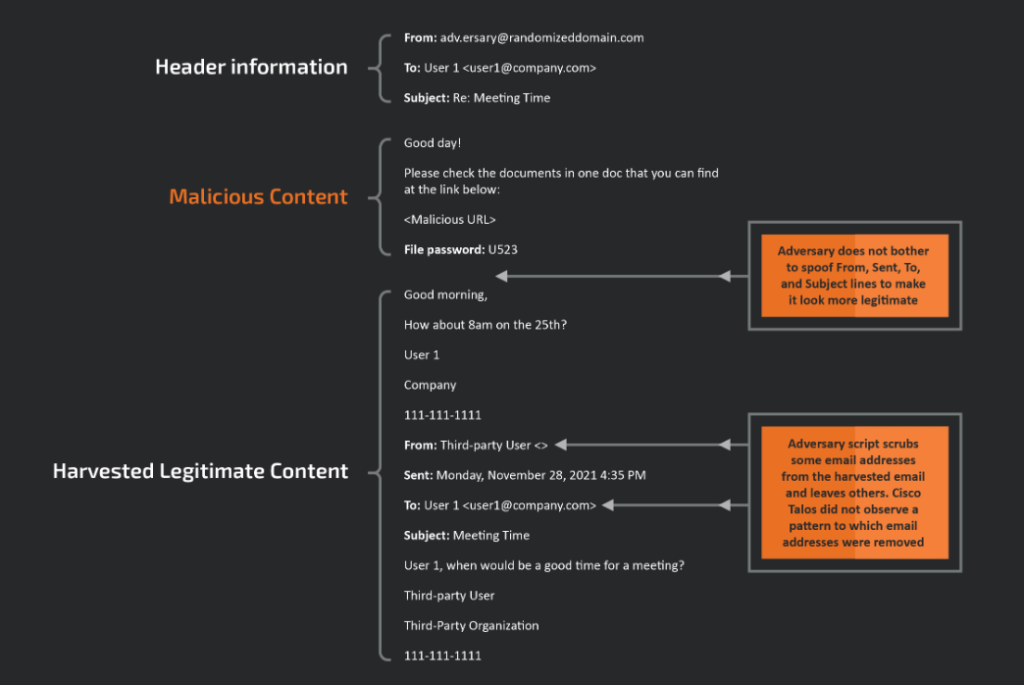
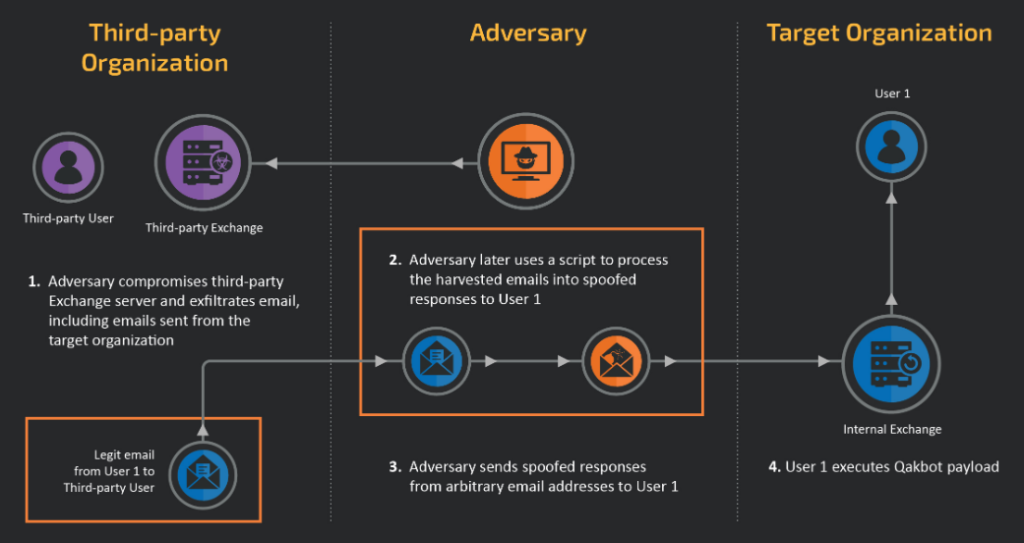
External Email Threat Hijacking
External thread hijacking is a technique used by attackers to turn emails that have already been taken from other companies into weapons. This is distinct from the more typical method of thread hijacking, in which attackers hack the Exchange server of the victim company to obtain email threads that are then turned into weapons.
In June 2022, as part of a larger operation to spread the Qakbot banking malware, we most recently noticed this. The attackers used existing emails that they had previously acquired from the 2021 Proxy Logon campaign, known as CVE-2021-26855, which was directed at susceptible Exchange servers, in this threat activity.
The Proxy Logon vector is a good theory because the majority of the originating Exchange servers we have also seen to be unpatched and publicly exposed. We have also seen a phishing email delivered internally on what looks to be an “internal” Exchange server, even though most of the Exchange servers used to send the phishing emails can be accessible by anybody over the Internet.
Additionally, some phishing emails have included the header “X-Mailer: Microsoft Outlook 16.0.” There is a “X-Originating-IP” header in other phishing emails. When using the web interface, the Exchange server adds this header. The client that connects to the server is identified by its IP address in the header. For the client IP, we have seen both non-commercial and hosting provider IP addresses.
They are two common patterns
- All the malicious crafted emails which have the attachment are from different sender domain most of them are in attacker control and the most important point to be noted here is “RE:” tag which is reply tag in the malicious email.
- The malicious attachments are having the second common pattern as the file name with slight tweaks. Sample file name “Report Jul 14 12345.html” in which the string from “Report Jul 14” are common but only the 5 numeric digits are random followed by “.html” as the extension. So the regex to be used to find all the file from the mail is “Report Jul 14 [0-9]+.html”.
Malicious Email Dissection
Campaign Summary
This campaign uses external thread hijacking, where the attacker launches targeted phishing efforts targeting previously uncompromised firms using a mass aggregation of emails from other organizations that have been stolen. This is distinct from the more typical method of thread hijacking, in which attackers send their threat via emails from a single compromised organization.
This many-to-one strategy differs from what we have typically seen in the past and is probably a side effect of the numerous hacks and large-scale email exfiltration that occurred in 2020 and 2021.
Defending Tips and Queries
Do vulnerability scanning on all the On Prem exchange server and run Thor lite scanner to identify the webshells based on yara signatures (make sure that business do not go down time by taking more resources on scanning the servers).
As the malware authors are getting evolved by making use of ISO files, so it is better to go for ISO mount blocking Blocking ISO mounting :: malicious.link — welcome
Email Defense
name: "Attachments with HTML smuggling"
type: "query"
source: |
map(filter(attachments, .file_extension in~ ('html', 'htm')
and any(beta.binexplode(.),
any(.scan.javascript.identifiers, . == "unescape"))), .file_name)
severity: "high"
tags:
- "Suspicious attachments"
- "HTML smuggling"name: "Attachment with HTML smuggling"
description: |
Recursively scans files and archives to detect HTML smuggling techniques.
references:
- "https://www.microsoft.com/security/blog/2021/11/11/html-smuggling-surges-highly-evasive-loader-technique-increasingly-used-in-banking-malware-targeted-attacks/"
type: "rule"
source: |
type.inbound and
any(attachments,
(
.file_extension in~ ("html", "htm",
"7z","bz2","gz","rar","tar","zip","zipx","iso","img") or
.file_type == "html"
)
and any(beta.binexplode(.),
any(.scan.javascript.identifiers, . == "unescape"))
)
tags:
- "Suspicious attachment"
- "HTML smuggling"sublime-rules/html_smuggling.yml at main · sublime-security/sublime-rules · GitHub
sublime-rules/attachment_html_smuggling.yml at main · sublime-security/sublime-rules · GitHub
Endpoint Defense
Qakbot Leveraging DLL-SideLoading to Deliver Malware – Detection & Response
HTML Smuggling Phishing Attacks on Rise – Detection & Response
Qakbot Attacks Evolving New Threat Techniques – Detection & Response



































