SocGholish is an attack framework that malicious actors have used since at least 2020. The term Soc refers to the use of social engineering to deploy malware on systems. SocGholish operators host a malicious website that implements a drive-by-download mechanism, such as JavaScript code or uniform resource locator (URL) redirections, to trigger the download of an archive file that contains malware.
The website displays content that might lure end-users, such as critical browser updates. To infect the system, an end-user has to first manually decompress the archive file and then execute the malware by double-clicking. An infection with SocGholish may result in the deployment of the Cobalt Strike framework and ransomware.
A drive-by attack is when a user visits an infected website and the website triggers a malicious download without user intervention.
SocGholish Infection Chain:
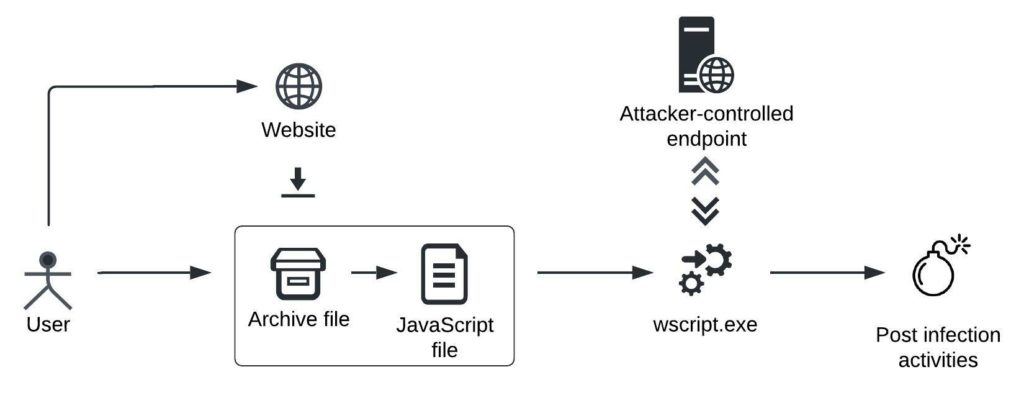
SocGholish operators host a malicious website that implements a drive-by-download mechanism. SocGholish operators use a legitimate website and host another, malicious website in its context, for example, in an inline frame (iframe) object. The legitimate website displays content to which end-users may be lured, such as critical browser updates. The malicious website may implement, for example, JavaScript code, or conduct URL redirections to trigger the download of an archive file that stores a malicious JavaScript script.
Also Read: Latest Cyber Security News – Hacker News !
To infect the system, an end-user has to first manually decompress the JavaScript script, for example, by using the Windows built-in archive utility or third-party utilities such as WinRAR, and then execute the script. If the Microsoft Windows Script Host (WSH) mechanism is not disabled on the system, WSH executes the script using the wscript or the cscript utility and the WSH JavaScript/JScript execution engine
Post Infection
SocGholish employs several scripted reconnaissance commands. While much of this activity occurs in memory, one that stands out is the execution of whoami with the output redirected to a local temp file with the naming convention rad<5-hex-chars>.tmp.
Enumerating domain trust activity with nltest.exe. SocGholish may lead to domain discovery. This type of behavior is often a precursor to ransomware activity and should be quickly quelled to prevent further progression of the threat.
The majority of SocGholish infections detected did not result in a second-stage payload, sometimes due to existing mitigations or rapid response to isolate the host. In most cases, we observed reconnaissance activity that only identified the infected endpoint and user. In some cases, Active Directory and domain enumeration followed user discovery.
Also Read: Latest IOCs – Threat Actor URLs , IP’s & Malware Hashes
Both of these can be a precursor to lateral movement, however, the hosts were isolated before any lateral movement activity could begin. Much of the reconnaissance conducted by the malicious JavaScript file happens in memory, with data being exfiltrated directly via POST commands to the C2 domain.
Summary
| Archive file and JavaScript script | To infect the system, an end-user has to download an archive file that stores a malicious JavaScript script. The script has a filename that relates to known browsers and browser updates, such as Opera.Update.a99283.js and Firefox.js. The end-user then has to manually decompress and execute the JavaScript script to infect the system. |
| Intensive reconnaissance | SocGholish operators conduct intensive reconnaissance activities and gather AD-related information by executing the commands whoami, systeminfo, nltest, net, and cmdkey. |
| Output redirection | The SocGholish operators redirect the output of executed commands to files with the filename extension .tmp, placed in the end-user’s AppData folder, for potential future exfiltration, such as C:\Users\<user>\AppData\Local\Temp\radF9A4F.tmp. |
| Injection of code into werfault.exe | Infections with SocGholish involve an injection of code into multiple instances of the werfault.exe process. The injected code typically implements tools with offensive capabilities. |
| Two attacker-controlled endpoints per infection | Over the course of an infection with SocGholish, the infected system communicates with two separate attacker-controlled endpoints. |
Indicator of Compromise:
File Names:
7b3f8c85c34fbda4125704220773509d578cbf862b0c3311241db1fe3003c8a5
bcab0580712475c75baee610f1f372ef524156bf097662fba710f293c8656f9f
75bec26067d15141bbfb8d18f0af2be190d6ae1a276640c182a5bf3137f76ffa
Also Read: FormBook Malware on The Rise – Detection & Response
Detection & Response:
Qradar:
SELECT UTF8(payload) from events where LOGSOURCETYPENAME(devicetype)='Microsoft Windows Security Event Log' and (((("Image" ilike '%\wscript.exe') and ("Process CommandLine" ilike '%.zip%' or "Process CommandLine" ilike '%.js%')) or ("ParentImage" ilike '%\wscript.exe' and ("Image" ilike '%\cmd.exe') and ("Process CommandLine" ilike '%whoami /all%'))) or ("Image" ilike '%\nltest.exe' and ("Process CommandLine" ilike '%/domain_trusts%' or "Process CommandLine" ilike '%/all_trusts%')))Splunk:((((Image="*\\wscript.exe") AND (CommandLine="*.zip*" OR CommandLine="*.js*")) OR (ParentImage="*\\wscript.exe" AND (Image="*\\cmd.exe") AND (CommandLine="*whoami /all*"))) OR (Image="*\\nltest.exe" AND (CommandLine="*/domain_trusts*" OR CommandLine="*/all_trusts*"))) AND source="WinEventLog:*"Elastic Query:(((process.executable:*\\wscript.exe AND process.command_line:(*.zip* OR *.js*)) OR (process.parent.executable:*\\wscript.exe AND process.executable:*\\cmd.exe AND process.command_line:*whoami\ \/all*)) OR (process.executable:*\\nltest.exe AND process.command_line:(*\/domain_trusts* OR *\/all_trusts*)))Arcsight:(((((((destinationProcessName CONTAINS "*\\wscript.exe" OR sourceProcessName CONTAINS "*\\wscript.exe" OR deviceProcessName CONTAINS "*\\wscript.exe")) AND ((destinationServiceName CONTAINS "*.zip*" OR destinationServiceName CONTAINS "*.js*" OR deviceCustomString1 CONTAINS "*.zip*" OR deviceCustomString1 CONTAINS "*.js*"))) OR (sourceProcessName ENDSWITH "*\\wscript.exe" AND ((destinationProcessName CONTAINS "*\\cmd.exe" OR sourceProcessName CONTAINS "*\\cmd.exe" OR deviceProcessName CONTAINS "*\\cmd.exe")) AND ((destinationServiceName CONTAINS "*whoami /all*" OR deviceCustomString1 CONTAINS "*whoami /all*"))))) OR (((destinationProcessName ENDSWITH "*\\nltest.exe" OR sourceProcessName ENDSWITH "*\\nltest.exe" OR deviceProcessName ENDSWITH "*\\nltest.exe")) AND ((destinationServiceName CONTAINS "*/domain_trusts*" OR destinationServiceName CONTAINS "*/all_trusts*" OR deviceCustomString1 CONTAINS "*/domain_trusts*" OR deviceCustomString1 CONTAINS "*/all_trusts*")))))Carbonblack:(((process_name:*\\wscript.exe AND process_cmdline:(*.zip* OR *.js*)) OR (parent_name:*\\wscript.exe AND process_name:*\\cmd.exe AND process_cmdline:*whoami\ \/all*)) OR (process_name:*\\nltest.exe AND process_cmdline:(*\/domain_trusts* OR *\/all_trusts*)))Crowstike:((((ImageFileName="*\\wscript.exe") AND ((CommandLine="*.zip*" OR CommandLine="*.js*") OR (CommandHistory="*.zip*" OR CommandHistory="*.js*"))) OR (ParentBaseFileName="*\\wscript.exe" AND (ImageFileName="*\\cmd.exe") AND ((CommandLine="*whoami /all*") OR (CommandHistory="*whoami /all*")))) OR (ImageFileName="*\\nltest.exe" AND ((CommandLine="*/domain_trusts*" OR CommandLine="*/all_trusts*") OR (CommandHistory="*/domain_trusts*" OR CommandHistory="*/all_trusts*"))))Fireeye:(metaclass:`windows` (((process:`*\wscript.exe` args:[`.zip`,`.js`]) OR (pprocess:`*\wscript.exe` process:`*\cmd.exe` args:`whoami /all`)) OR (process:`*\nltest.exe` args:[`/domain_trusts`,`/all_trusts`])))GrayLog:(((Image.keyword:*\\wscript.exe AND CommandLine.keyword:(*.zip* *.js*)) OR (ParentImage.keyword:*\\wscript.exe AND Image.keyword:*\\cmd.exe AND CommandLine.keyword:*whoami\ \/all*)) OR (Image.keyword:*\\nltest.exe AND CommandLine.keyword:(*\/domain_trusts* *\/all_trusts*)))Logpoint:(((Image IN "*\\wscript.exe" CommandLine IN ["*.zip*", "*.js*"]) OR (ParentImage="*\\wscript.exe" Image IN "*\\cmd.exe" CommandLine IN "*whoami /all*")) OR (Image="*\\nltest.exe" CommandLine IN ["*/domain_trusts*", "*/all_trusts*"]))Microsoft Defender:DeviceProcessEvents | where ((((FolderPath endswith @"\wscript.exe") and (ProcessCommandLine contains ".zip" or ProcessCommandLine contains ".js")) or (InitiatingProcessFolderPath endswith @"\wscript.exe" and (FolderPath endswith @"\cmd.exe") and (ProcessCommandLine contains "whoami /all"))) or (FolderPath endswith @"\nltest.exe" and (ProcessCommandLine contains "/domain_trusts" or ProcessCommandLine contains "/all_trusts")))Microsoft Sentinel:SecurityEvent | where EventID == 4688 | where ((((NewProcessName endswith @'\wscript.exe') and (CommandLine contains '.zip' or CommandLine contains '.js')) or (ParentProcessName endswith @'\wscript.exe' and (NewProcessName endswith @'\cmd.exe') and (CommandLine contains 'whoami /all'))) or (NewProcessName endswith @'\nltest.exe' and (CommandLine contains '/domain_trusts' or CommandLine contains '/all_trusts')))Sumologic:(_sourceCategory=*windows* AND ((((((Image = "*\wscript.exe") AND (CommandLine = "*.zip*" OR CommandLine = "*.js*")) OR (ParentImage="*\wscript.exe" AND (Image = "*\cmd.exe") AND (CommandLine = "*whoami /all*")))) OR (Image="*\nltest.exe" AND (CommandLine = "*/domain_trusts*" OR CommandLine = "*/all_trusts*")))))RSA Netwitness:((((Image contains '\wscript\.exe') && (CommandLine contains '.zip', '.js')) || ((ParentImage contains 'wscript.exe') && (Image contains '\cmd\.exe') && (CommandLine contains 'whoami /all'))) || ((Image contains 'nltest.exe') && (CommandLine contains '/domain_trusts', '/all_trusts')))Source/Credits: cybereason.com/blog/threat-analysis-report-socgholish-and-zloader-from-fake-updates-and-installers-to-owning-your-systems redcanary.com/threat-detection-report/threats/socgholish/



































