Emerging threats in cybersecurity, such as new malware or attack methods, require proactive defense. Analysts at ANY.RUN shared their hands-on recommendations on how to investigate and collect information on novel malicious software strains and phishing attacks early.
What makes a threat emerging?
An emerging threat in cybersecurity is characterized by its novelty and the challenges it poses to existing defenses. Several factors contribute to what makes a threat emerging:
- New Techniques and Tools: Emerging threats often employ methods, tools, or exploits that have not been widely observed before.
- Continuous Evolution: These threats are constantly evolving, with attackers continually refining their tactics to avoid detection and countermeasures.
- Unpredictability: Emerging threats can be highly unpredictable, appearing in unexpected ways and targeting new vulnerabilities.
- Serious Implications: Emerging threats can have severe consequences for their victims, including significant financial losses, data breaches, operational disruptions, and damage to a company’s reputation.
- Lack of Intelligence: The limited information available about the attack methods, strategies, and techniques of emerging threats.
Let’s now consider a few examples of emerging threats and see how they can be investigated.
Collecting Intelligence on Emerging Threats: 4 Use Cases
1. New Phishing Threats
Cyber attackers are always finding new ways to make their phishing attempts more believable. They do this by using real services, copying popular websites, and creating convincing tricks. Their goal is to fool users into giving away sensitive information or installing harmful software.
Example: Tycoon 2FA Phish-kit Abusing SES Accounts
Recently, ANY.RUN researchers identified a phishing campaign that exploited compromised Amazon Simple Email Service (SES) accounts to distribute phishing emails. The attack began with an email from Amazon SES, redirecting victims through various domains, including social networks and news outlets like India Times, ultimately leading to a page requesting their credentials.
To find more information, samples, and indicators of compromise (IOCs), ANY.RUN analysts use Threat Intelligence Lookup.
The service provides access to a searchable database of the latest threat intelligence. It allows users to utilize over 40 different search parameters and their combinations, including IPs, domains, MITRE TTPs, registry paths, to find relevant information on currently active threats.
Try Threat Intelligence Lookup for free with a 14-day trial.
Consider this combined query submitted to TI Lookup. It uses pieces of data used in Tycoon 2FA attacks to help us discover other indicators and more samples:
| commandLine:”/etl.php?url=” AND domainName:”.economictimes.indiatimes.com” |
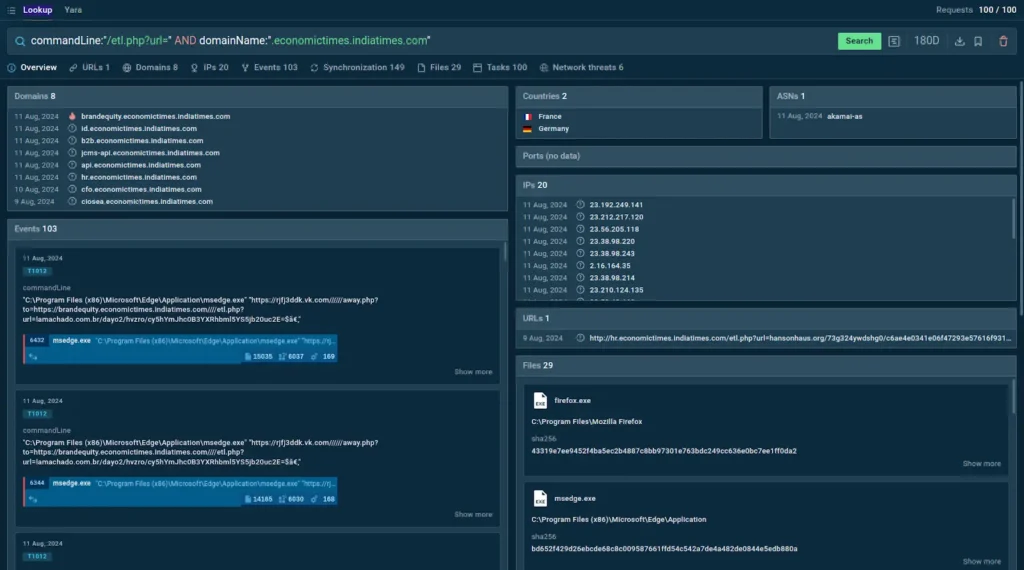
TI Lookup helps enrich existing data on threats with additional context
As a result of our search, we find 8 more domains used in the campaign, 20 IPs, 29 files, and other details.
Plus, we get to access and study a hundred sessions in the ANY.RUN sandbox to see analysis of actual examples of Tycoon 2FA phishing attacks, where these indicators were found.
2. New and Evolving Malware Families
New types of malware appear daily, some of which become serious global security threats. These can include ransomware, trojans, and other harmful software, often using advanced methods to avoid detection and blend in with normal activities.
Example: DeerStealer Malware
In July 2024, ANY.RUN identified a new malware family named DeerStealer. It was spreading through a phishing campaign designed to resemble the Google Authenticator website.
To detect this threat and collect new samples of this evolving malware, researchers created a YARA detection rule.
Using TI Lookup’s YARA Search feature, we can utilize the rule to find more samples with their corresponding sandbox sessions.
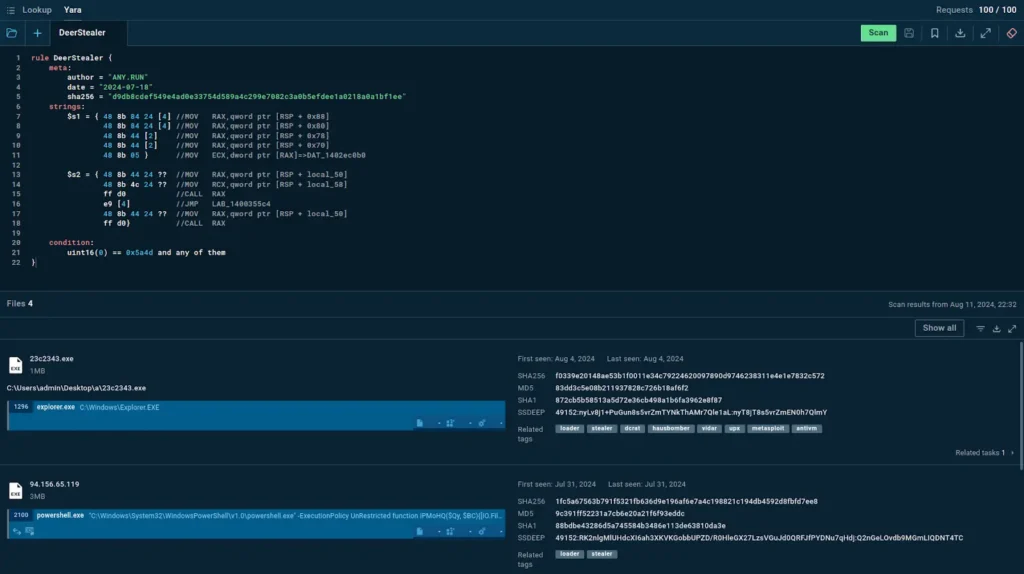
YARA Search lets you submit your custom rules
Using TI Lookup’s YARA Search feature, we can utilize the rule to find more samples with their corresponding sandbox sessions.
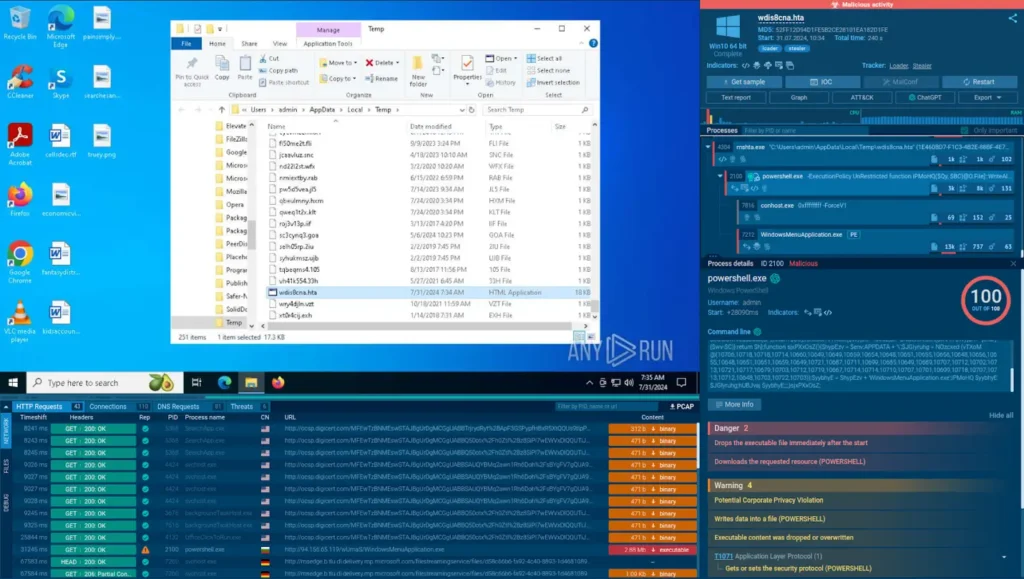
DeerStealer sample analyzed in ANY.RUN Sandbox
As a result, we can stay up-to-date on how the threat is evolving by having access to its latest samples.
3. TTPs (Tactics, Techniques, and Procedures)
TTPs are the ways attackers perform their actions. New types of malware often find novel methods to exploit flaws, avoid being noticed, and steal information. The MITRE ATT&CK matrix organizes these actions, giving a clear structure to understand different TTPs.
Example: New HijackLoader Version
HijackLoader is a malware family that received an update in 2024. One of the newly-acquired features for it was User Account Control (UAC) bypass (T1548.002), allowing it to run on infected devices without triggering Windows security controls.
By adding the identifier of the UAC to our search query along with the threat’s name, we can find many sandbox sessions featuring analysis of the updated threat:
| MITRE:”T1548.002″ AND threatName:”hijackloader” |
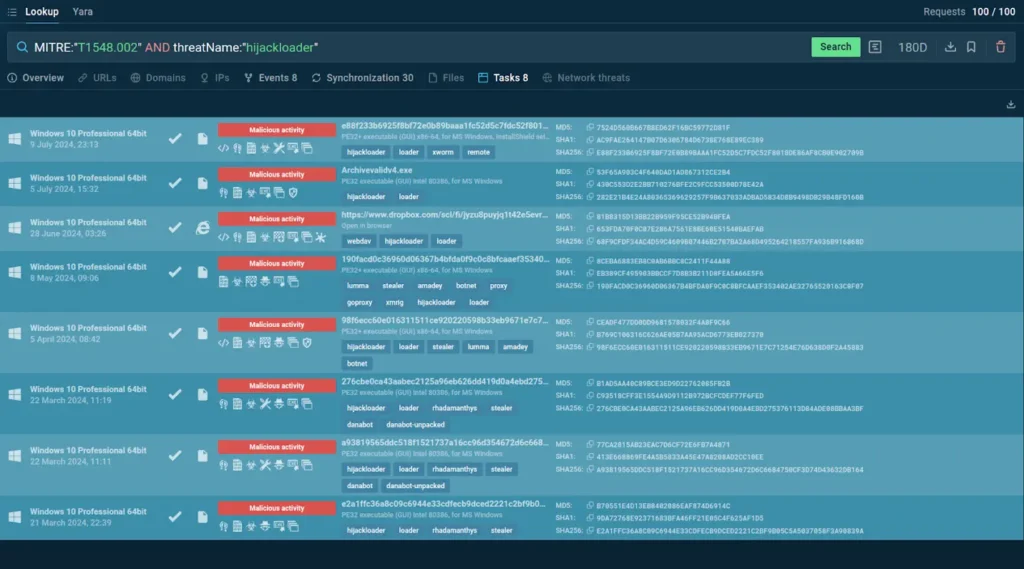
Each session also includes hash sums for the analyzed sample
We can extract all the information from the samples provided by the service to improve our understanding of the malware’s behavior and upgrade our detection capabilities.
4. Exploitation of World Events
Attackers are also quick to take advantage of major global events. For instance, the COVID-19 pandemic witnessed a surge in phishing emails and malicious websites falsely offering information or assistance related to the virus.
Example: CrowdStrike Incident
Threat actors recently exploited the CrowdStrike outage to disseminate malware and phishing attempts. Following the release of a faulty update by the cybersecurity company, millions of PCs were hit with the blue screen of death. This led to a surge in phishing emails and malicious websites offering bogus recovery guides.
ANY.RUN analysts used Threat Intelligence Lookup to investigate these threats, including using the query for finding fake websites hosting malicious content:
| domainName:”crowdstrike” AND threatLevel:”malicious” |
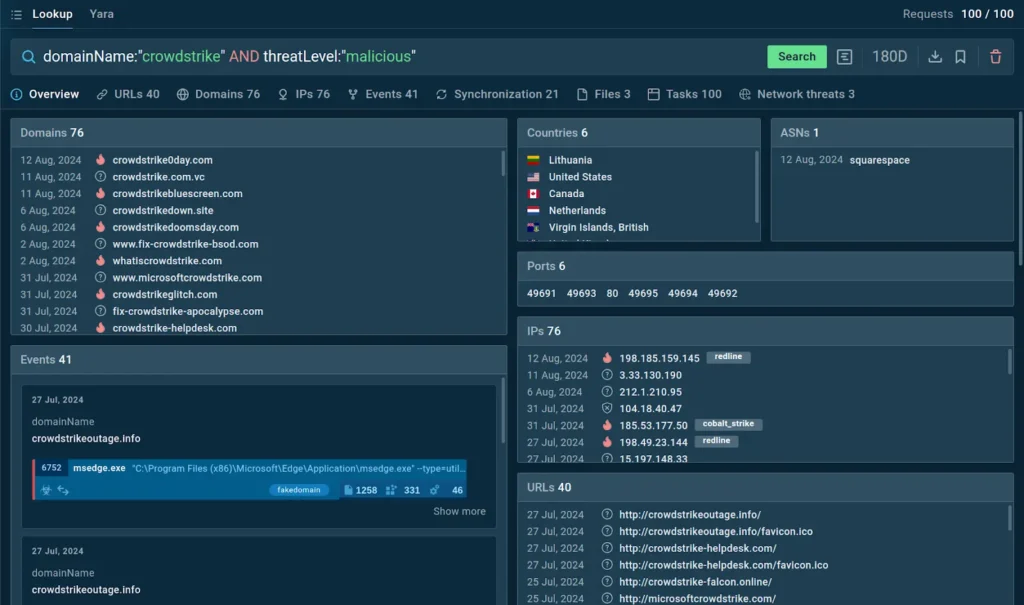
TI Lookup has an extensive database of threat info on CrowdStrike incident threats
The service responded with 76 domains, IPs, URLs, along with sandbox sessions.
Try Threat Intelligence Lookup from ANY.RUN
You can strengthen your organization’s threat intelligence capabilities with TI Lookup. Make sure to use it together with ANY.RUN’s interactive sandbox that not only detects threats in under 40 seconds and provides detailed threat reports with IOCs, but also gives you full control over the virtual analysis environment.
See how TI Lookup and sandbox fit in your security infrastructure by using a 14-day free trial.



































