BlueScreen with white fonts! obfuscated code? Post exploitation Framework capabilities! Yes! It’s a PowerShell, Windows administrator uses it for multi-purpose to control the windows environment locally and remotely to run the tasks and make their work much easier. This has attracted red teamers’ and cybercriminals’ attention too. The industry has seen lots of attacks with PowerShell tools such as SharpSploit, PowerSploit, PowerShell Empire, MailSniper, Bloodhound, Nishang, and Invoke-Obfuscation.
These attacks rapidly increased in cyberspace as fileless malware. As the name implies, attacks that avoid malware being placed onto a targeted system. Malware running on memory never leaves files on disk as it gives footprints for blue teamers. In this blog, we will see how we can hunt the malicious PowerShell activities with windows event IDs
Also Read: Latest IOCs – Threat Actor URLs , IP’s & Malware Hashes
Hunting the Fileless Malware & Powershell Activities:
- Event ID 4103 – Module logging – Attackers uses several obfuscated commands and calls self-defined variables and system commands , Hunting these Event ID provides soc operations to record all the obfuscated commands as pipeline execution details under the event ID 4103.It should be enabled to process and get the malicious commands.
- Event ID 4104 – Powershell Script Block Logging – Captures the entire scripts that are executed by remote machines. For Example Obfuscated scripts that are decoded and executed at the run time.This gives additional visibility on remote command.
- If an event exceeds the maximum event log message size, script block logging will split the logged events into multiple events and Suspicious commands can be observed at the logging level of “warning”.
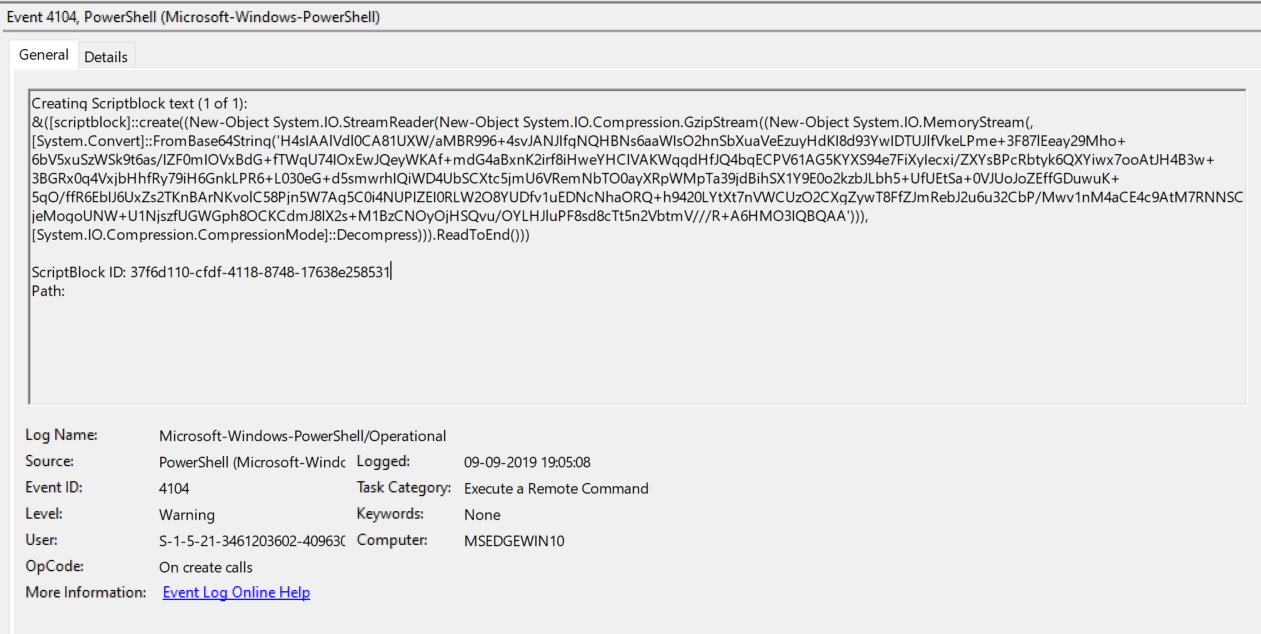
- Above figure shows , Script block ID is generated for the remote command execution from the computer “MSEDGEWIN10” and the security user ID S-1-5-21-3461203602-4096304019-2269080069-1000 and commands are fully encoded.
Also Read: Threat Hunting Using Windows Event ID 5143
- Enabling the Event ID 4104 as an added benefit as run time obfuscated commands will be processed to decode and all decoded scripts will be logged into this event ID 4104.
Also Read: Soc Interview Questions and Answers – CYBER SECURITY ANALYST
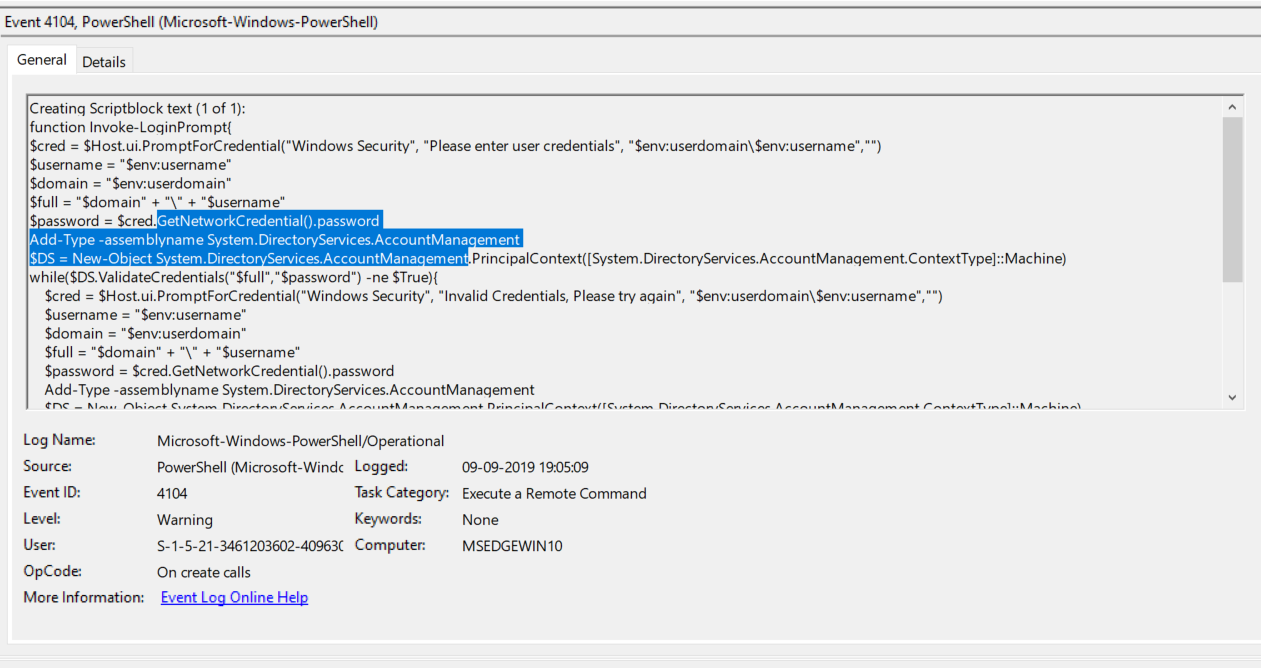
- Above figure shows , Encoded commands are decoded at the run time and above malicious code is try getting the users network credential password. Possible phishing attack.In addtion we can also track Mimikatz activites ,Lateral Movement via WinRM and more suspicious activities.
- Event ID 4688 – Audit Process Creation with Command Line Process Auditing – Enabling this Event ID provides the source process names which is executing the malicious commands that is processed in audit mode and logged. Command line arguments are commonly leveraged in fileless based attacks and is an good resource for the blue team.
- This provides insights on Parent and child process names which is initiating the powershell commands or command line arguments.
Configuring PowerShell Event ID 4103/4104:
Group Policy for logging configuration:
- Computer Configuration > Policies > Administrative Templates > Windows Components > Windows PowerShell.
- Select: Turn on Module Logging, and Select: Enabled, Select: OK
- Select: Turn on PowerShell Script Block Logging, and Select: Enabled, Select: Log script block invocation start /stop events:
Configuring Event ID 4688:
Group Policy for logging configuration:
- Computer Configuration > Policies > Windows Settings > Security Settings > Advanced Audit Configuration > Detailed Tracking
- Select: Audit Process Creation, Select: Success + Failure, Select: OK
- Computer Configuration > Policies > Administrative Templates > System > Audit Process Creation
- Select: Include command line in process creation events, Select: Enabled, Select: OK
Enabling these three Event IDs (4104, 4103, and 4688), blue teamers can effectively increase the visibility and context necessary to understanding “fileless” threats. Powershell logging should be enabled before you use Powershell.
Happy hunting!



































