This event is generated when a process attempts an account logon by explicitly specifying that account’s credentials. This most commonly occurs in batch-type configurations such as scheduled tasks.
It is also a routine event that periodically occurs during normal operating system activity, what’s abnormal? Hunting specific processes at the timeline of the event ID 4648 provides more insights on adversaries. Please find the below cheatsheet.
Hunting with Event ID 4648:
- Event ID 4648 contains with the process name “C:\windows\System32\mstsc.exe” which is the indicator for user machine with outbound RDP connections detected. This can be mapped to T1076 of mitre and the active traces of lateral movement.
- Event message contains “*/TERMSRV/*” with the Event ID 4648 , Which is known to a RDP outbound connection from end user machine.Indicator for possible lateral movement detection.
- Process name “C:\Windows\System32\sc.exe” with the Event ID 4648 shows remote machine services are queried and executed.Indicator for Possible lateral movement detection. This can be mapped to mitre T1021/T1035.
Also Read: Soc Interview Questions and Answers – CYBER SECURITY ANALYST
- Threat actor persistence with new service account with alternate credentials were Event ID 4648 at the time of incident.This includes services running with specfic account other than local system or Network Service , I.E “Account Name” equals sshd_server & process_name equals services.exe , This can be mapped to mitre T1050.
- Adversaries may use Valid Accounts to interact with remote machines by taking advantage of Distributed Component Object Model (DCOM) , Mostly it is called as RPC Calls , Remote Procedure Call (RPC) is a protocol that one program can use to request a service from a program located in another computer on a network without having to understand the network’s details. A procedure call is also sometimes known as a function call or a subroutine call.To detect such behaviours , Check for event messages contains Event ID 4648 contains with the event message contains “RPCSS/“. This can be mapped to mitre T1021/T1175.
The RPCSS service is the Service Control Manager for COM and DCOM servers. It performs object activations requests, object exporter resolutions, and distributed garbage collection for COM and DCOM servers. If this service is stopped or disabled, programs using COM or DCOM will not function properly – Microsoft Says
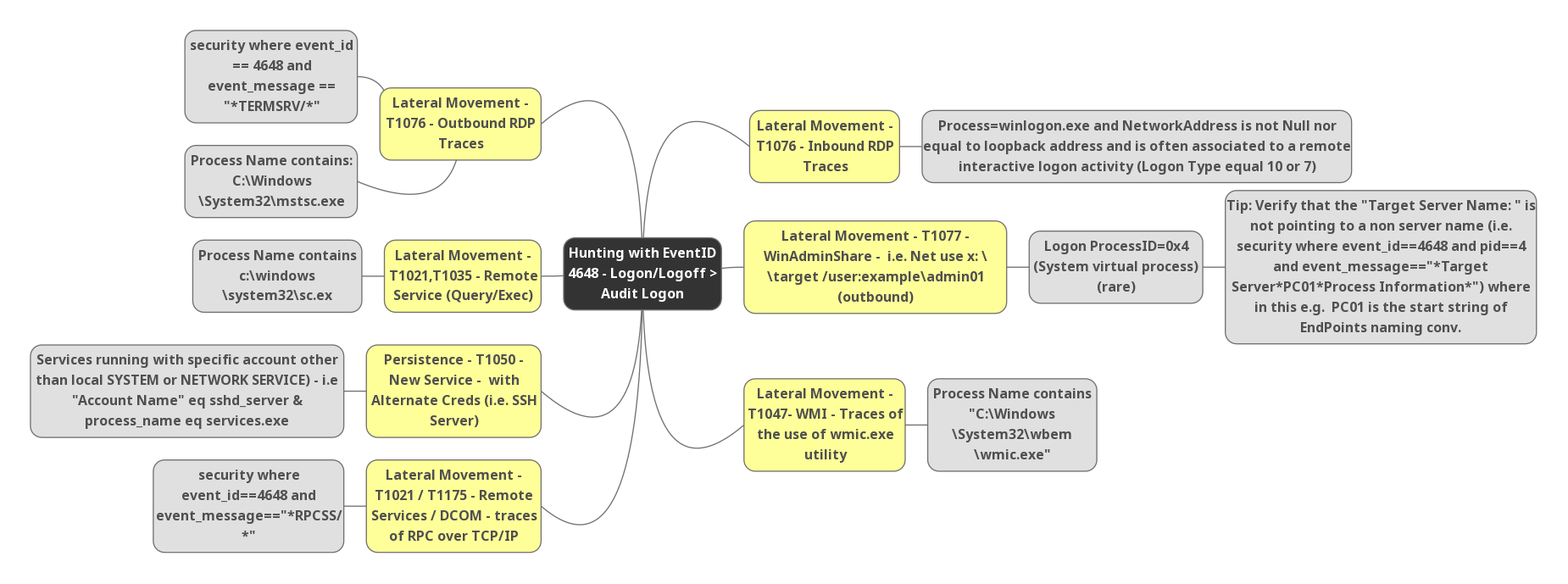
- Detecting possible inbound RDP Connections , Event ID 4648 detected with Process name “Winlogon.exe” and Network address is not empty nor equal to loopback address and this is often associated with a remote interactive logon activity ( Logon Type equals 10 or 7 ) . This can be mapped to mitre T1076.
Also Read: FireEye’s Open-Source Tool – CAPA to Identify Malware Capabilities
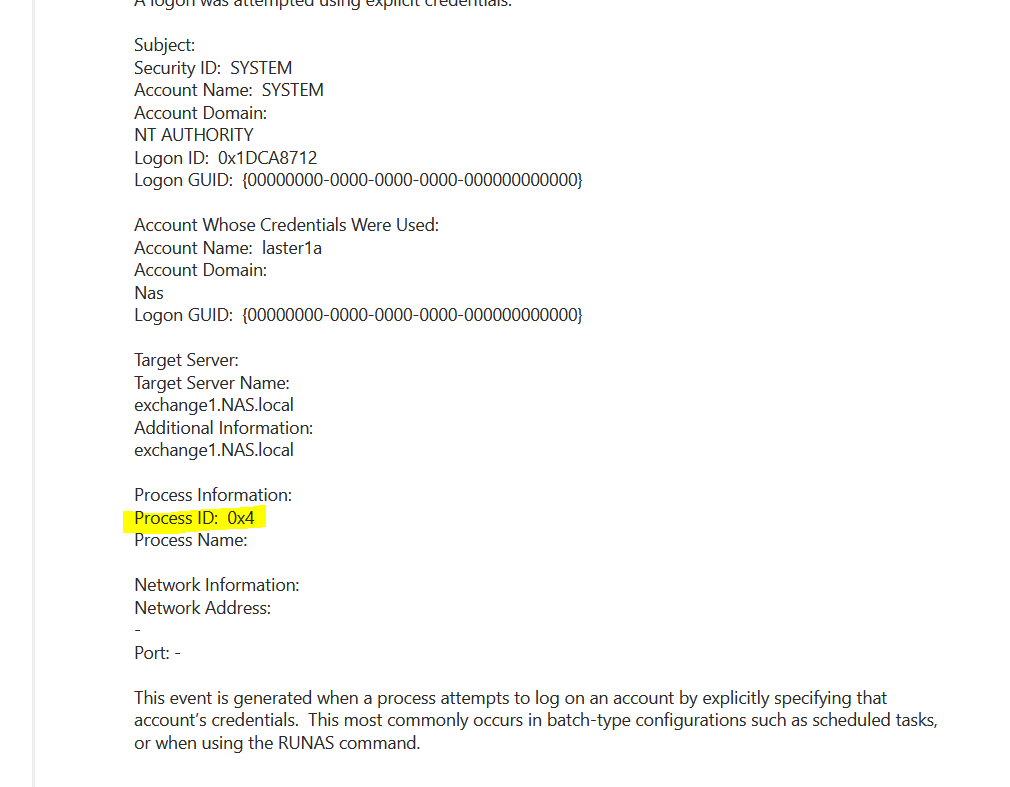
- Possible windows admin shares access , Event ID 4648 with cmd commands I.E Net use x:\target/user:example\admin01 ( Outbound connections ) , and logon process ID “0x4” or 4 and target server name contains *Targetserver*PC01*processinfromation* , Where in this example PC01 start sting of endpoint naming conversions. This can be mapped to mitre T1077.
Also Read: Threat Hunting using DNS logs – Soc Incident Response Procedure
- Event ID 4648 contains with the process name “wmic.exe” , Indicator of lateral movement with Windows Management Instrumentation. This can be mapped to mitre T1047.
Happy Hunting



































