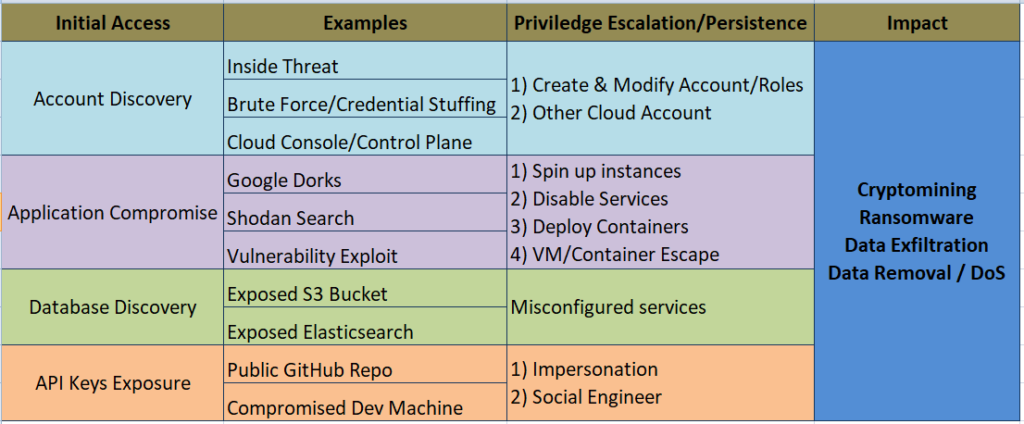
Traditional on-premise systems have the potential to be less secure than cloud-based solutions. Literally, because the cloud can be more secure does not mean that organizations will always be safer once they make the switch. We are seeing more attacks against cloud infrastructures. For the past few years, cloud security has been in the top two. Obviously, many enterprises are rapidly migrating to the cloud, and as a consequence, they must explore how to secure it. Here’s a quick rundown of what we’re seeing in case of cloud attacks:
As risks have developed and new attacks have become more complex, it’s become more necessary than ever for businesses to implement security-first approaches. Here are some of the most important concerns, as well as how cloud security solutions can support your company in tackling them:
Also Read: Latest IOCs – Threat Actor URLs , IP’s & Malware Hashes
1-Data Breaches:
- There is no greater source of anxiety than a data breach. It’s which every company is concerned about.
- As a consequence, it is a real concern that has to be dealt with in a proactive and preventative way. Inability to properly handle data (via purposeful encryption) exposes your company to significant compliance concerns, as well as data breach penalties, fines, and substantial breaches of customer trust.
- Regardless matter what your Service-Level Agreement (SLA) says, you are responsible for protecting your customer and employee data.
2- Compliance with Regulatory Mandates:
- It’s common for businesses, particularly small and mid-sized businesses, to believe that simply cooperating with a cloud solutions provider will offer them with optimal security.
- International and federal regulations aren’t the only ones that must be followed. There are also extra industry requirements that must be met. EU data protection, PCI DSS, FISMA, GLBA, HIPAA, and FERPA are just a few examples.
- Cloud security solutions provide the technical capability to comply with regulatory standards, but constant oversight and specific technical skill are required. Under the responsibility approach, the cloud provider offers security of the cloud, while the end user provides security in the cloud.
Also Read: Threat Hunting with EventID 5145 – Object Access – Detailed File Share
3- Lack of IT Expertise:
- As per the Cloud Security Group’s “Cloud Adoption Practices & Priorities Survey Report,” 34% of businesses are avoiding cloud computing because they believe their IT and business management lack the skills and experience to handle the expectations.
- As a consequence, it is one of the top four concerns that businesses have about cloud security.
- In today’s world, the average company has three to four clouds. This adds levels of complexity, necessitating technical expertise and appropriate experience.
- These points to a wider pattern that we’ll see develop in the months and years ahead. IT and business managers would be expected to bring technical cloud knowledge to the table, rather than just managerial experience and financial awareness.
- This does not imply that they must be cloud experts; however, a fundamental awareness of the cloud and the capacity to lead specific projects are required.
4- Issues with Cloud Migration:
- Cloud migration is on the rise, but it must be managed appropriately. Otherwise, the company is exposed to unnecessary danger.
- Visibility into infrastructure security, compliance, creating security rules, and security failing to keep up with the rate of change in applications are the four largest difficulties confronting firms, according to one survey.
- As a consequence, security and IT professionals are feeling overwhelmed by the amount of work they’re being asked to do.
- Easier and more uncomplicated migration solutions will provide in smoothly navigating this transition. It’s a big mistake to try to do everything at once.
- To limit the possibility of critical errors that could corrupt data and/or lead to vulnerabilities, the migration process should be broken down into stages.
Also Read: Top Windows Security Events Logs You Must Monitor
5- Unsecured APIs:
- The problem with the cloud is that there are so many different ways for attackers to gain access.
- As a consequence, while the total surface attack area is less, it is much more scattered. Perhaps nowhere is this more evident than in microservice design and the growing popularity of serverless operations.
- APIs are excellent, but you must consider how they will affect the overall system.
- Even if the cloud is technically secure, data can be stolen if criminals gain access to less-secure APIs.
- This is a serious issue. The right cloud security solutions can assist you in thoroughly evaluating each application to protect against vulnerabilities like these.
6- Insider Threats:
- Trusting your employees is a good business practise.
- Unfortunately, many firms go too far with their trust – or fail to evaluate the things that drive their trust up front.
- Organizations, in especially, should consider access management and limiting who has access to what and when.
- Cloud apps and data sources should be made available on a need-to-know basis. Nobody should have more access than they need to fulfill their work responsibilities.
Also Read: Threat Hunting Using Windows Event ID 5143
7- Open Source:
- Open source software is used to create apps and open source packages are vulnerable.
- Typically, hackers poison the well in the Git repo, waiting for developers to use the packages and then compromise the application via a well-planned attack vector.
Conclusion:
It can be difficult to understand how these work and, more significantly, how to safeguard them. Using a security platform strategy can help you develop a more secure cloud, but you should also educate your architects and administrators. One important area to consider is strengthening your cloud account credentials, which are frequently targeted by hostile actors. Using multi-factor authentication to access the accounts can greatly reduce this risk.