Attacks by malware are continuously growing. These malicious files use high-obfuscation algorithms to hide from traditional anti-malware detection solutions, and unfortunately, the threat actors are becoming more and more successful.
One technique that has seen a positive track record for evading detection is when a malicious document is password-protected, and the password is given in the email body, making it easy to trick unsuspecting users into opening the malicious file.
Password protection makes it harder for traditional detection solutions to scan the attachment for malicious code.
Also Read: Most Common Windows Event IDs to Hunt – Mind Map
Example of the Malware Attack
The employee receives an email that appears to be from a trusted and well-known sender, or a common brand, with a catchy subject (ex. ‘Invoice’, ‘Payment verification’, etc). The email contains an attached file that is zipped and password-protected by the attacker, and they’ll also include a full name (e.g. Tenesha Mitchell) to make it seem human. The password creates the illusion the attachment must contain confidential personal information that had to be secured.
When an employee receives the compromised email with the password-protected file and the required password to access the file, it raised no suspicions.
Also Read: Threat Hunting Using Windows Security Log
Attack Detection with Windows Event Logs
Example 1: Attack Detection Case
This event occurs when a user performs a read operation on stored credentials in Credential Manager. Example: Users open up ZIP files which are password-protected files with valid credentials.
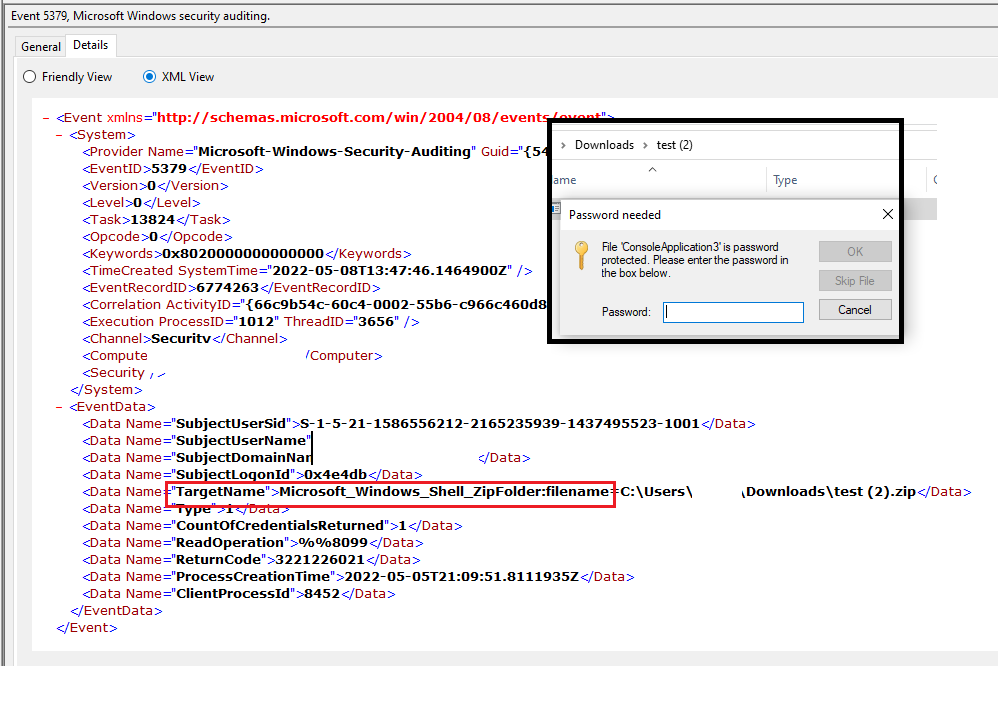
The above figure illustrates User has opened the test (2).zip file. SBousseaden says opening a password-protected zip file using Windows Explorer generates a credman event 5379 with Target “Microsoft_Windows_Shell_ZipFolder:filename=zip_fil_path”.
Also Read: Malware Hiding Techniques in Windows Operating System
This can be correlated when malware is executed with windows legitimate processes ( Explorer.exe ) on specific file paths. Similar cases are also observed when users download, cracks/keygens to enable the full features of legitimate software. But ending up with system/network infections.
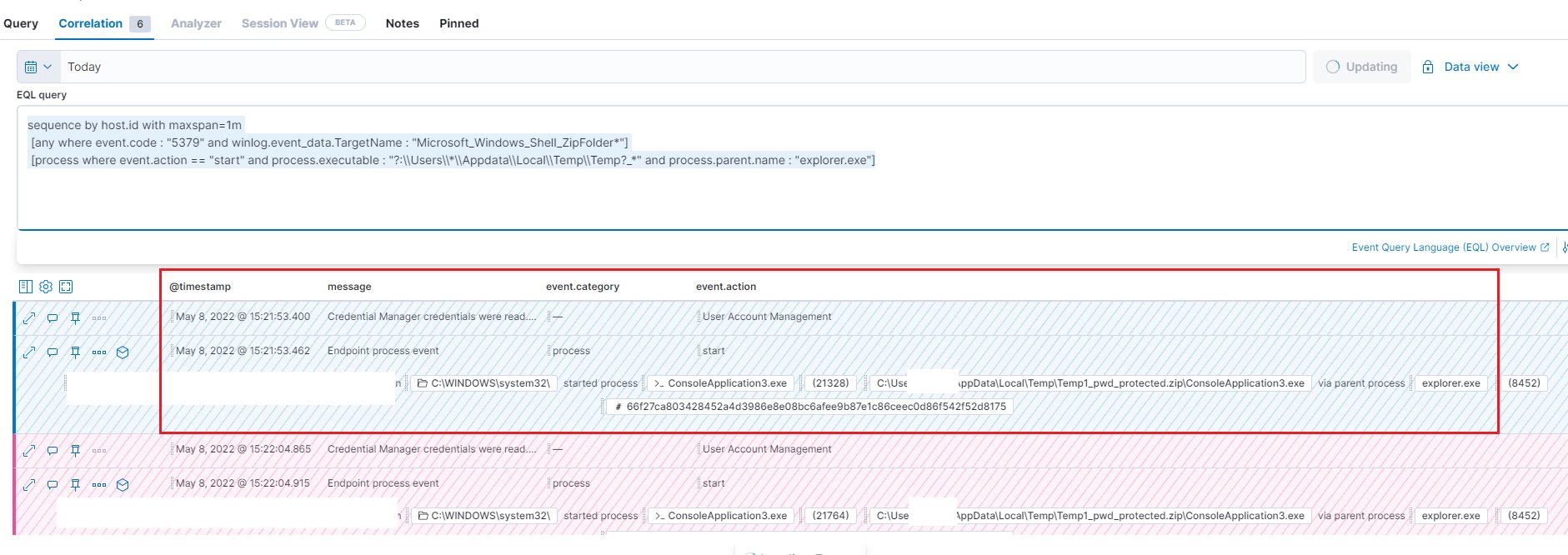
The above query shows that malware spread has been successfully detected using the event ID 5379.
Example 2: False Positive Case
Some people may experience Event ID 5379 flooding. It is good to review their user accounts/programs that are connected with the credential manager.
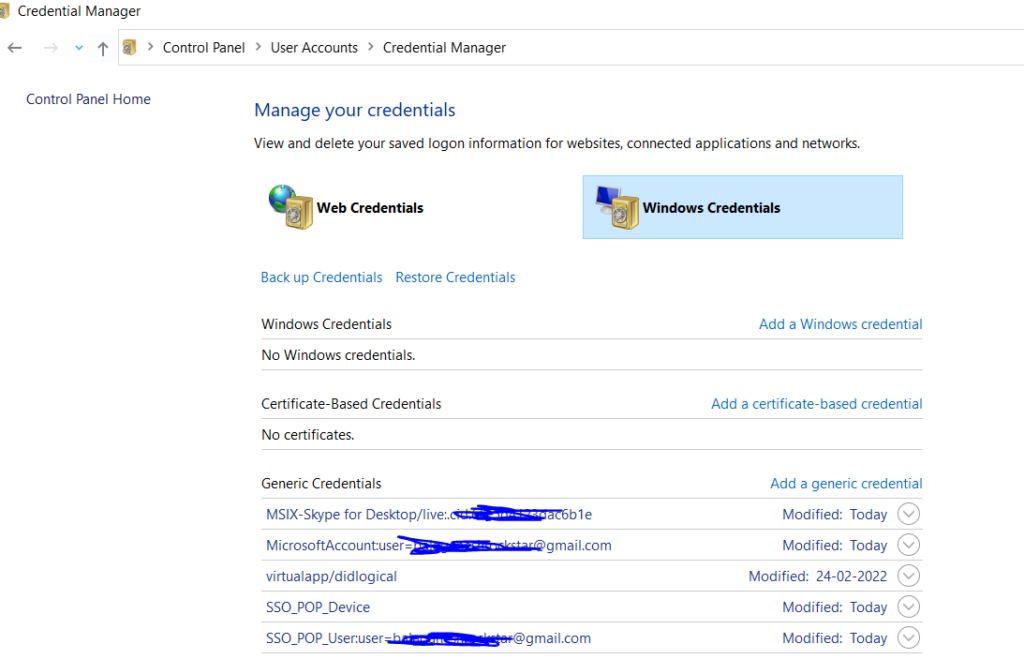
Assume Windows admin has disabled a user in my Active Directory (terminated the account). However, still getting the log that Event IDs 5379 (credential manager credentials were read.), 4673 (a privileged service was called.), 4656 (a handle to an object was requested.)
And the processes called are:
gfxdownloadwrapper.exe 4673
lsbupdater.exe 4673
cleanmgr.exe 4673
quickup.exe 4673
searchui.exe 4673
Disabling an account in AD doesn’t mean an account cannot log on to an endpoint due to cached credentials. The account may not have been disabled/removed from the machine in question, so some scheduled tasks associated with the account are still being executed on the machine (e.g. search indexing, disk cleanup, etc).
Considering the above scenario we can mark it as false-positive.
EQL Detection Query:
sequence by host.id with maxspan=1m [any where event.code : "5379" and winlog.event_data.TargetName : "Microsoft_Windows_Shell_ZipFolder*"] [process where event.action == "start" and process.executable : "?:\\Users\\*\\Appdata\\Local\\Temp\\Temp?_*" and process.parent.name : "explorer.exe"] Also Read: How to Detect Privilege Escalation Attacks and UAC Bypass on Windows
Other SIEM Products:
SOC analyst/ SOC Engineers use the below logic to create effective rules on their SIEMS to track Windows Event ID 5379 with malicious behaviors.
Correlate event ID 5379 with Target name "Microsoft_Windows_Shell_ZipFolder*" and process executable paths "?:\\Users\\*\\Appdata\\Local\\Temp\\Temp?_*" and parent process "explorer.exe" and process action is start.
Happy Hunting!
References:
https://www.ultimatewindowssecurity.com/securitylog/encyclopedia/event.aspx?eventid=5379
securityboulevard.com
https://serverfault.com/questions/1092543/a-user-activity-is-detected-from-a-disabled-account-in-active-directory