We are all aware of the new ransomware “WIZARD SPIDER”. We believe that there is a curious connection between WIZARD SPIDER’s Ransomware Infrastructure and a Windows Zero-Day Exploit.
Introduction:
RiskIQ’s Team Atlas and Microsoft’s Threat Intelligence Center (MSTIC) collaborated in September 2021 to release technical findings on a wave of malicious activity that used CVE-2021-40444, a vulnerability in MSHTML that allows remote code execution on a victimized Windows PC. This activity’s operational origins are said to have started in February of 2021. The network infrastructure employed in this campaign has a lot of overlap with the network architecture linked with WIZARD SPIDER, according to RiskIQ and Microsoft.
Who is WIZARD SPIDER (aka UNC1878)?
WIZARD SPIDER (aka UNC1878) is a large, Russia-based, criminal enterprise that has operated the Trickbot, Bazar, and Anchor families of malicious Remote Access Trojans (RATs) and has been observed deploying the Conti and Ryuk ransomware families in “Big-Game Hunting” campaigns that target large enterprises.
Initial Gatherings:
- WIZARD SPIDER used non-public IP addresses as Command and Control (C2) nodes for Cobalt Strike, which the group used as a post-intrusion tool prior to the deployment of Ryuk and Conti ransomware. The overlaps that Microsoft and RiskIQ discovered were related to supporting infrastructure, in the form of non-public IP addresses, used by WIZARD SPIDER as C2 nodes for Cobalt Strike, which the group used as a post-intrusion tool prior to Domain registrant information (particularly the registrant email address) provided when purchasing the domains used to create TLS certificates revealed additional overlap (thus enabling TLS encryption for the Cobalt Strike C2 traffic between victim and attacker).
- WIZARD SPIDER’s C2 infrastructure was ascribed to an extensive list of IP addresses and TLS certificates (and their associated domain names) provided by RiskIQ’s Team Atlas. PACT was able to cross-reference and validate the Naver-themed phishing activity detected with WIZARD SPIDER’s operations using this list.
- During their studies, both research teams discovered anomalies that suggest the overlap isn’t indicative of a WIZARD SPIDER operation, but rather of numerous actors using the same network infrastructure. Multiple operators utilising known compromised servers, a “kind of command-and-control infrastructure as a service for cybercriminals,” or some other shared resource not owned by a single threat actor might all be to blame for the overlap.
- PACT found a research area (mailmangecorp[.]us) via a tweet by Joe Slowik within 4 months while conducting standard investigation and analysis of harmful web-based infrastructure. PACT analysts began painstakingly establishing a network of targeted phishing infrastructure geared to gather legitimate Naver login credentials after this initial discovery. The Naver Corporation is a major, regionally popular internet platform that offers dozens of customer-facing services (e.g., email, search, social, and payment) and is comparable to a South Korean Google.
- PACT analysts discovered commonalities with the WIZARD SPIDER architecture, discussed above, while researching the hosting infrastructure used to deliver the Naver-themed phishing pages, based on RiskIQ’s and Microsoft’s joint reports. This blog will go over PACT’s findings and methods, as well as the overlaps with WIZARD SPIDER infrastructure and significant conclusions that may offer fresh light on Microsoft and RiskIQ’s alternate hypothesis.
Findings:
Naver-themed Phishing Activity:
PACT discovered 542 unique domains as part of this malicious cluster of web infrastructure, 532 of which were assessed with high confidence to be part of the ongoing phishing campaign targeting Naver logins; the oldest domain identified by PACT was registered in August of 2021, while others were registered as recently as February of 2022. The remaining domains were of unknown provenance, were part of previously disclosed prior malicious infrastructure that PACT observed as part of this cluster, or was otherwise abnormal but linked by hosting or registration connections. The complete list of 532 Naver-themed phishing domains may be seen in the report’s annex.
PACT’s investigation’s “critical nodes*” turned out to be IP addresses and, when available, domain registrant personalities (identified and tracked by the registration email address used to register the domain). The first critical node discovered was IP 172.93.201[.]253; PACT’s analysis immediately revealed that this IP was used by a huge number of Naver-themed phishing pages with a common registrant (mouraesse[@]gmail[.]com).
Image 1-The below image represents the Numerous domains registered by mouraesse@gmail[.]com resolved to 172.93.201[.]253:
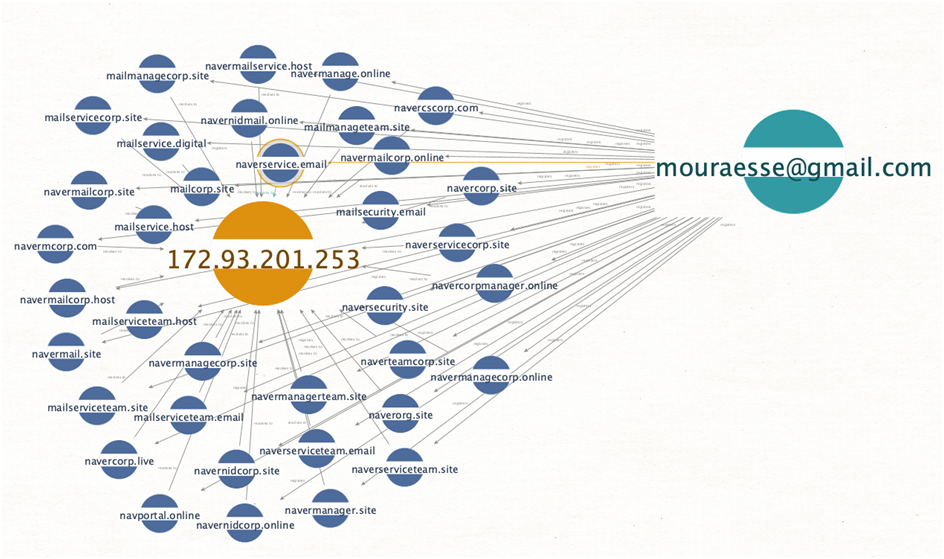
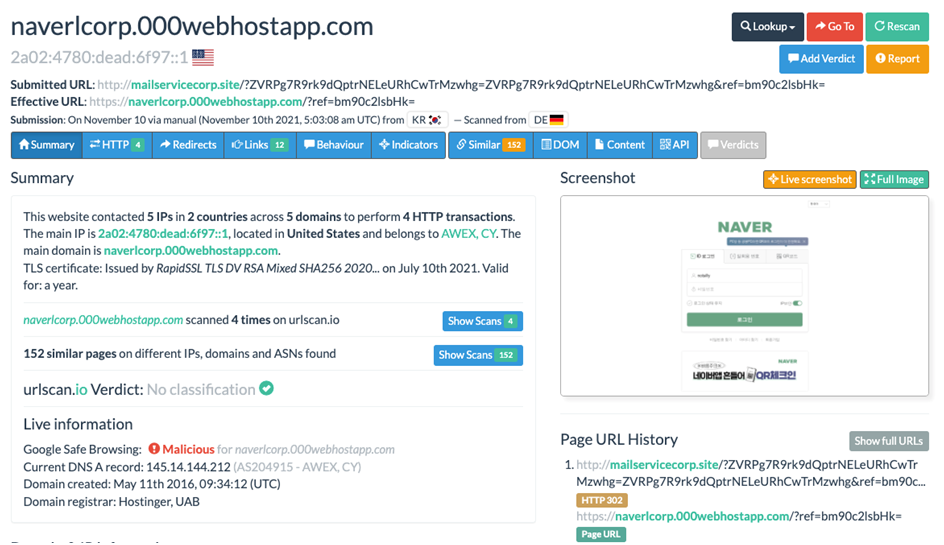
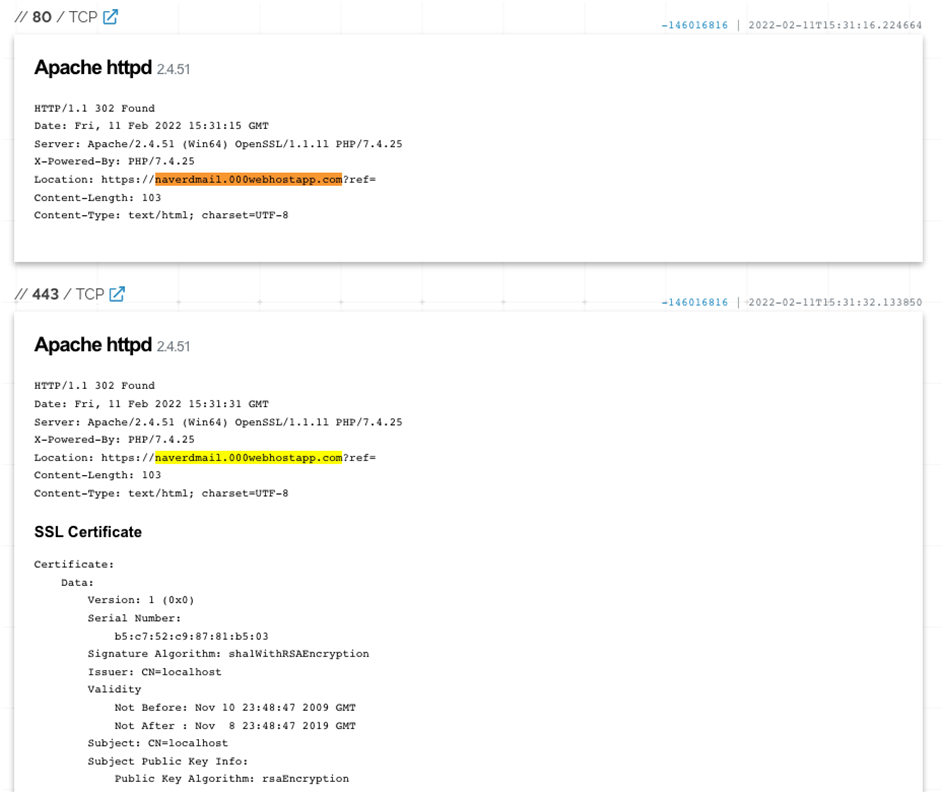
Image 2-Naver-themed domain hosted on IP 172.93.201[.]253 displaying an HTTP/302 redirect to a spoofed Naver login page on “000webhostapp[.]com” as seen below –
PACT was able to determine that many domains registered with the registrant email “mouraesse@gmail[.]com” were resolving to another IP address, 23.81.246[.]131, by pivoting on the registrant email “mouraesse@gmail[.]com.” The initial link between the Naver credential phishing activity and the claimed WIZARD SPIDER infrastructure was created by this IP address, which became a significant node in PACT’s investigation. However, before we go into detail about our results on these reported overlaps, there are a few more crucial nodes that are entirely within the Naver-themed phishing activity cluster:
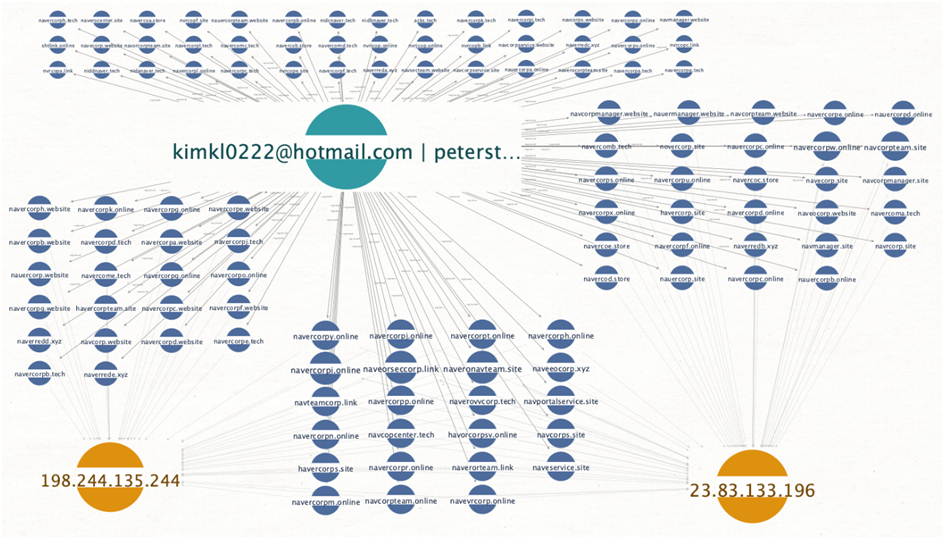
- Registrant email addresses “peterstewart0326@gmail[.]com” and “kimkl0222@hotmail[.]com”, which appear to have been used jointly and by the same actor, registered over 100 Naver-themed phishing domains.
- Registrant email addresses “tree99111@hotmail[.]com” and “jhonsteven0001@hotmail[.]com”, which also appear to have been used jointly and by the same actor, registered 69 domains, some of which had previously resolved to critical node 23.81.246[.]131.
Image 3- The below image shows the Persona behind the email addresses “peterstewart0326@gmail[.]com” and “kimkl0222@hotmail[.]com” shown along with Naver-themed domain registrations and the associated resolutions.
IP addresses:
23.83.133[.]196:
- Part of ASN 19148 (LeaseWeb USA, Inc.), along with critical node 23.81.246[.]131
- Linked via pDNS resolutions to many domains registered by the “kimkl0222@hotmail[.]com / peterstewart0326@gmail[.]com” actor
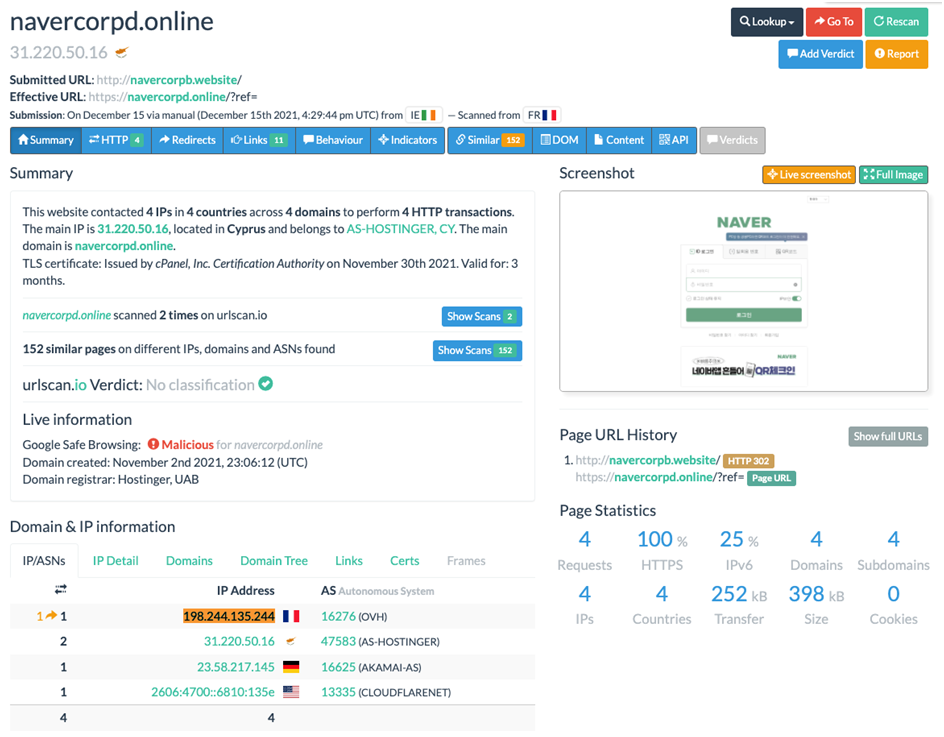
198.244.135[.]244:
- Part of ASN 16276 (OVH SAS), along with critical node “15.235.132[.]77”, seen below
- Linked via pDNS resolutions to many domains registered by the “kimkl0222@hotmail[.]com / peterstewart0326@gmail[.]com” actor
- Displayed TTP overlap (IP seen serving HTTP/302 redirects to Naver phishing pages).
Image 4-This the picture that shows critical node IP address 198.244.135[.]244 observed serving HTTP/302 redirects, a TTP overlap with the Naver-phishing actor:
15.235.132[.]77
- Part of ASN 16276 (OVH Singapore PTE. LTD), along with critical node “198.244.135[.]244”, seen above
- Provided overlap with domains registered by the “kimkl0222@hotmail[.]com / peterstewart0326@gmail[.]com” actor that allowed PACT to identify additional WHOIS domain registrant “gameproducters@outlook[.]com”
108.177.235[.]15
- Part of ASN 395954 (Leaseweb USA, Inc.)
- Provided overlap with domains registered by the “kimkl0222@hotmail[.]com / peterstewart0326@gmail[.]com” actor
- Displayed TTP overlap (IP seen serving HTTP/302 redirects, notably to the legitimate Naver login page).
Notably, none of the crucial node IP addresses listed above, including 23.81.246[.]131, appear to be commercial shared web hosting addresses (as historic resolutions only include the Naver phishing activity). Furthermore, despite the fact that public scan data for all 5 IP addresses is limited, they all appear to be Windows workstations with self-issued TLS certificates.
The reader should also be aware of the typical use of the HTTP 302 Redirect to guide victims to the intended page. On Hostinger’s web hosting platform “000webhostapp[.]com,” PACT discovered HTTP 302 Redirects to both additional Naver-themed phishing domains (as seen in Image 4 above) and to various Naver-themed phishing subdomains. On the crucial node IP address 23.81.246[.]131 (along with an expired, self-signed TLS certificate), an example displays below:
Image 5: HTTP/302 redirect to 000webhostapp[.]com (a TTP overlap) identified on critical IP 23.81.246[.]131
This screenshot from Shodan’s ‘host’ page for 23.81.246[.]131 (last seen date: 2022-02-15) shows how phishing infrastructure can be set up, regardless of the final phishing URL hosted on “000webhostapp[.]com”:
- Victim clicks or otherwise navigates to one of the 500+ Naver-themed domain names.
- The DNS A-record for an arbitrary number of them is set to an IP address with a web server configured similar to the way that 23.81.246[.]131 is set up (with a generic, catchall HTTP 302 Redirect) to a subdomain of “000webhostapp[.]com.
- Victim’s browser redirects them to the “000webhostapp[.]com” domain, where they are served a convincing replica of the Naver login page.
- Victim enters their credentials, which are captured and now compromised.
This setup is built to endure domain attrition, which is frequent in widely-distributed phishing campaigns and is caused by phishing domains being recognized, reported, and taken down or blocked listed. The threat actor’s infrastructure becomes more resilient by separating the final phishing URL from the first victim-facing URL. Additionally, because the phishing kit is hosted on a reputable hosting platform, the final URLs hosting the phish kit are more likely to be “allow listed” or not extensively scrutinized.
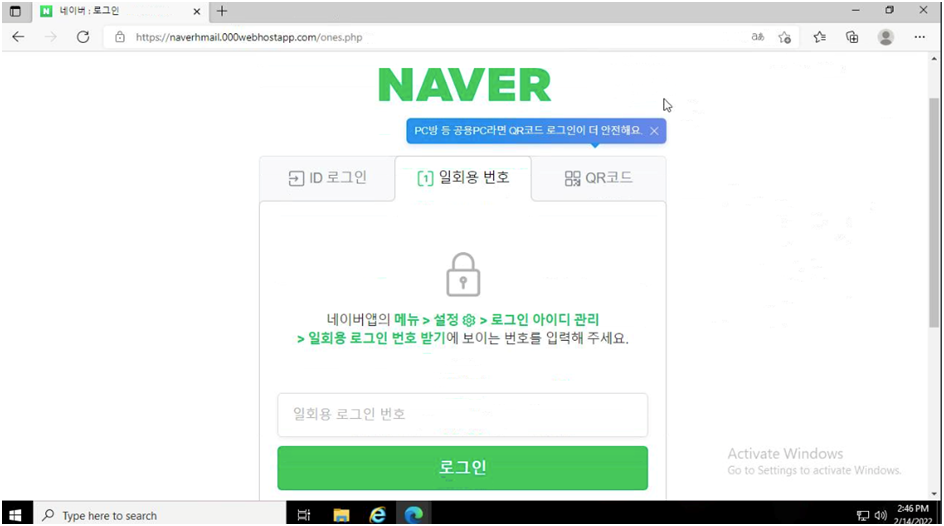
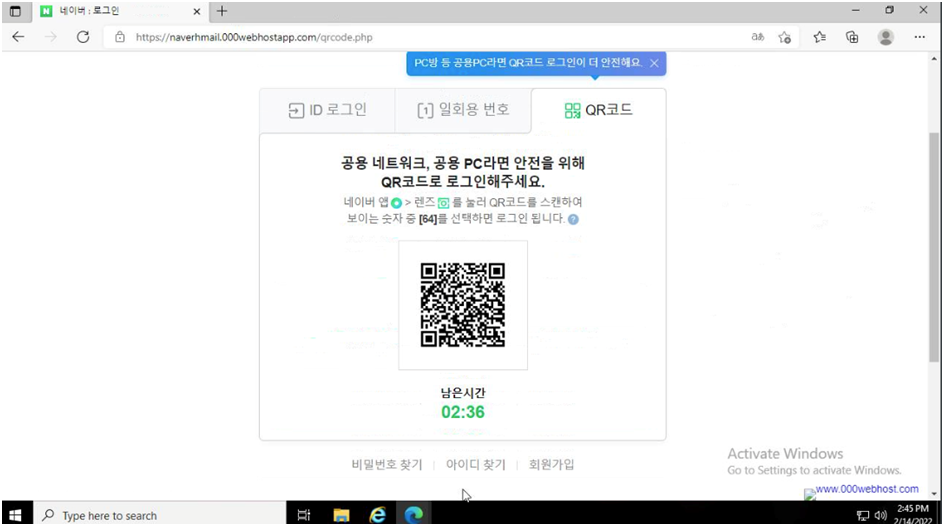
Phishing for Naver credentials looks to be common, which could suggest how valuable authentic logins are. The threat actor’s TTP differed from those seen by AhnLab’s ASEC: they didn’t employ tech-themed domains, didn’t use HTTP 302 Redirects to guide victims to the final credential-gathering page, and the one-time-use number and QR code functionality wasn’t configured. Although we were unable to verify if users were effectively compromised using these methods, the Naver-themed phishing pages that PACT evaluated featured working one-time-use number and QR code functionality.
Images 6 & 7: the Naver phishing pages PACT analyzed supported one-time-password and QR code functionality
The subdomains that PACT was able to identify on “000webhostapp[.]com” serving spoofed-Naver phishing pages are included in the annex at the end of this report. Due to the ease with which the operator can create new subdomains on this hosting platform, this list is likely outdated and/or incomplete.
IIb: Overlaps with Reported WIZARD SPIDER Infrastructure:
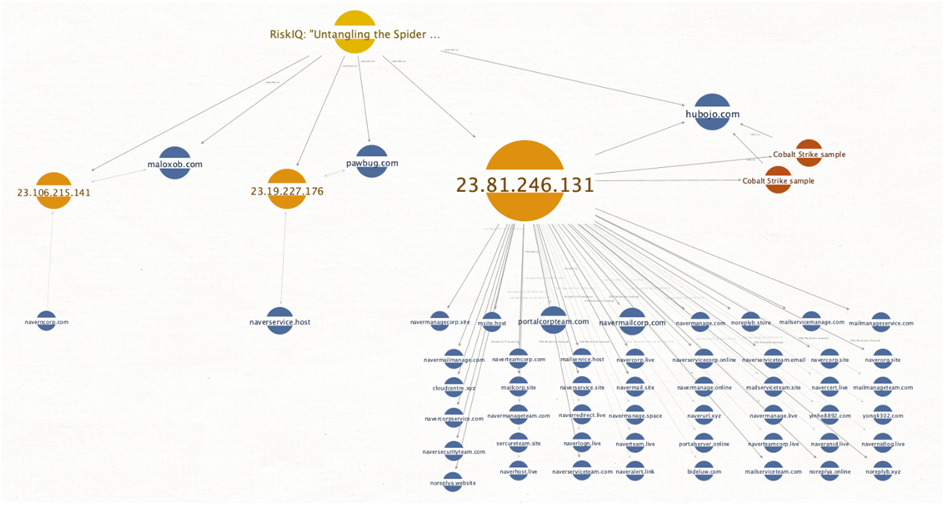
- PACT claimed in section ‘IIa: Naver-themed Phishing Activity’ that there were parallels between the network infrastructure supporting the Naver phishing activity and that of WIZARD SPIDER’s prior network infrastructure. IP 23.81.246[.]131 was the first to notice the overlap (seen in Image 5, above, displaying TTP overlap).
- PACT’s analysts first found this IP address when trying to figure out which of the 58 phishing domains registered by “mouraesse@gmail[.]com” were actively resolving, if any. The domain “navermailcorp[.]com” was resolving to “23.81.246[.]131” at the time of initial analysis, which PACT determined resulted in an HTTP Redirect to a faked Naver login page on “*.000webhostapp[.]com.”
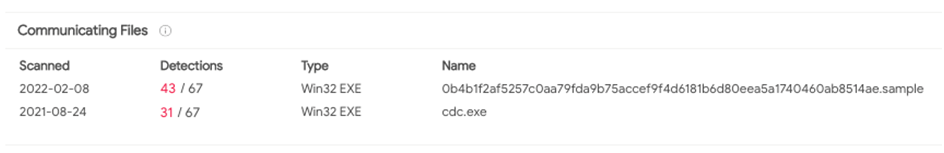
- Additional research turned up two malware samples associated with IP 23.81.246[.]131, according to VirusTotal:
Image 8: Malicious files seen communicating with IP of interest 23.81.246[.]131
The extracted Cobalt Strike Beacon (post-exploitation payload) configuration for one of the samples displays the same watermark identified by a security researcher on Twitter who identified these samples as part of a cluster of activity exploiting CVE-2021-40444, which was confirmed by open-source reporting. In addition, the other sample’s network behavior indicates HTTP connections to “hubojo[.]com” and “bideluw[.]com.” These two domains are significant since they both match the recovered Beacon configuration from the previous sample and represent additional, distinct linkages to 23.81.246[.]131:
- “bideluw[.]com” was observed resolving to this IP via pDNS
- RiskIQ reported that this IP previously served the certificate for “hubojo[.]com”, tying it to a Cobalt Strike C2 server (validating the extracted Beacon configuration from VirusTotal).
These observations all serve to bolster the previous reports of an actor using this infrastructure to support a campaign exploiting CVE-2021-40444 and to host Cobalt Strike.
PACT noticed that more than 40 of the Naver-themed phishing domains had resolved to IP 23.81.246[.]131, which was noteworthy given the historical findings. Throughout the research, PACT discovered a number of emergent resolutions, indicating that this activity is still occurring on and that this infrastructure is still in use. Throughout the pre-publication pipeline, PACT’s analysis found several domains registered in March 2022.
Additional Findings:
In addition to the connections supplied by 23.81.246[.]131, IP 23.19.227[.]176 revealed another overlap. This IP was originally linked to “naverservice[.]host” (a Naver phishing cluster), but it was also included in RiskIQ’s analysis as part of the same Cobalt Strike C2 infrastructure used by the actor that exploited CVE-2021-40444. It was linked to “pawbug[.]com” in this example, which PACT independently confirmed using pDNS.
Another link to the infrastructure outlined in RiskIQ’s research is IP 23.106.215[.]141, which is formed by a link between “naverncorp[.]com” and “maloxob[.]com.” A Cobalt Strike C2 server was also discovered at the domain “maloxob[.]com.” PACT’s analysts were also led to another domain, cebuwu[.]com, which will be discussed later in this report.
Image 9: Critical overlaps between RiskIQ’s previous findings & the Naver-themed phishing activity.
Two more IP addresses that are believed to represent shared resources were discovered to have overlaps:
- 184.168.221[.]39: ties together “mailhelp[.]online” (part of the cluster targeting Naver) with “jumpbill[.]com” and “raills[.]com” (reported as Cobalt Strike C2s by RiskIQ).
- 195.186.208[.]193: ties together at least two of the domains seen in the Naver phishing activity (“navrcorp[.]site” & “navercorps[.]online”) and dozens of the Cobalt Strike domains reported by RiskIQ
Summary:
IIIa. Analytic Gaps & Anomalous Findings:
PACT discovered a number of abnormalities and anomalies when evaluating and processing the data revealed in this inquiry. They are listed in no particular order below:
- The majority of the domains identified as part of the Naver-phishing cluster of activity were not protected by privacy settings, making it easy for analysts to find other domains with the same registrant information (e.g., email address). Privacy has become a de facto standard during the domain registration process as a result of WHOIS Privacy and GDPR. It’s unusual to come across a cluster of activity, particularly one linked to a named threat group like WIZARD SPIDER, in which all of the domain-based infrastructure is unobscured by privacy protection services.
- The domain-generation algorithm and other TTPs of the Threat Actor managing the Cobalt Strike infrastructure were revealed by RiskIQ’s study. As a result of this insight, PACT identified two domains: cebuwu[.]com and lertwo[.]com, which matched RiskIQ’s evaluation of the actor’s TTPs. In the following ways, these two domains intersected with earlier reporting:
- They are between six to eight alphabetic characters in length, which aligns with the Domain Generation Algorithm (DGA) likely used by the threat actor(s).
- They utilize the “.COM” top level domain (TLD).
- The domain cebuwu[.]com used the legitimate Certificate Authority “Sectigo”.
- The domain cebuwu[.]com was identified via 23.106.215[.]141, which also links another Cobalt Strike C2 domain reported by RiskIQ (maloxob[.]com) and the Naver-themed activity (via naverncorp[.]com).
- Likewise, past resolutions link the domain lertwo[.]com to both the Cobalt Strike C2 activity (195.186.208[.]193, 195.186.210[.]241) as well as the naver activity (navrcorp[.]site, navercorps[.]online, navertechp[.]online). It is likely that these resolutions are the result of shared hosting or a pooled resource with many customers but the overlap is notable nonetheless, as it may indicate an operator preference or behavioral TTP.
- The domain disneycareers[.]net was discovered during an investigation of important node IP 172.93.201[.]253, which appears to be a convincingly designed imitation of Disney’s real careers page: jobs.disneycareers[.]com. In addition to being labelled as malicious by Google’s Safebrowsing service, the mimic site is hosted on Namecheap’s network and is not registered with CSC CORPORATE DOMAINS, INC. (as Disney’s actual site is). The simulated site’s appearance altered dramatically during the examination, presumably indicating active development. Furthermore, the TLS certificate was issued by Sectigo, which corresponds to the behaviour described above for the Cobalt Strike C2 domains’ Certificate Authority of Choice.Although the purpose of this mockup domain is unknown, the criminal nexus surrounding the rest of the associated infrastructure should be enough to trigger further investigation and could perhaps imply targeted attacks.
Takeaways:
- PACT believes that the Naver-themed phishing activity is extremely likely to be operationally tied to the Cobalt Strike infrastructure discovered by RiskIQ (and mentioned by Microsoft).
- Furthermore, PACT would like to highlight that these findings do not necessarily imply that WIZARD SPIDER is responsible for the discrete clusters of activity discovered on this infrastructure.
- The fact that this infrastructure has been utilised to close several different killchain links across multiple campaigns (and maybe by different actors), along with the observations made by RiskIQ and Microsoft, may lend more credence to the ideas they’ve put up.
According to Risk IQ,
“Despite the historical connections [between WIZARD SPIDER and the Cobalt Strike C2 infrastructure], we cannot say with confidence that the threat actor behind the zero-day campaign is part of WIZARD SPIDER or its affiliates, or is even a criminal actor at all, though it is possible.”
According to Microsoft,
“The infrastructure we associate with DEV-0365 has significant behavioral overlaps and distinct identifying traits with Cobalt Strike infrastructure, implying that it was constructed or controlled by a different set of operators.” However, further behavior from this infrastructure suggests that human-operated ransomware attacks are linked to various threat actors or clusters (including the deployment of Conti ransomware). DEV-0365 may be involved in a type of command-and-control infrastructure as a service for cybercriminals, according to one theory.”
Conclusion:
The latter is particularly noteworthy, according to PACT, because the Naver-themed phishing activity that was first uncovered does not appear to be the work of a ransomware gang. Pre-ransomware activity (such as mass phishing and credential gathering) is often handled by affiliates or brokers that provide access to ransomware operators, while post-compromise operations, ransomware development, and deployment/encryption are handled by other organizations.
Within the illegal business model of ransomware-as-a-service (RaaS), this separation of roles is typical. PACT’s findings of the additional “uncertainty surrounding the nature of the shared qualities” of this infrastructure and the “significant variation in malicious activity,” similar to what Microsoft and RiskIQ reported, strengthen the hypotheses put forward by both firms: multiple entities could be utilizing the same third party providing “bulletproof hosting” services to conduct their operations. PACT was unable to rebut this theory, and as a result, it has a moderate level of confidence that an unreported illicit hosting business is operating on this infrastructure. PACT was only able to find ties to the alleged WIZARD SPIDER activity through hosting and DNS resolutions; no additional operational mechanisms were found to link to the reported WIZARD SPIDER activity (such as registrants, malicious samples, etc).
As a result, the evidence points to a new and rising “infrastructure as a service for cybercriminals.
Detection Opportunities & Indicators of Compromise:
acc-center[.]site naveewteam[.]site navermailservice[.]host navportal[.]online
acks[.]tech naveloga[.]online navermailservice[.]online navportalcenter[.]site
centersecurity[.]link navelosa[.]host navermailservice[.]site navportalcorp[.]site
cloudalarm[.]online naveoccorp[.]link navermailteam[.]online navportalsec[.]site
cloudalarm[.]site naveoccorp[.]online navermanage[.]com navportalsecs[.]site
cloudalarm[.]space naveocenter[.]link navermanage[.]live navportalservice[.]site
cloudalarm[.]tech naveocop[.]link navermanage[.]online navrcenter[.]site
cloudalarm[.]website naveocorp[.]link navermanage[.]space navrcorp[.]site
cloudalarm[.]xyz naveocorp[.]online navermanagecorp[.]online navrcorp[.]tech
cloudcentre[.]online naveocorp[.]site navermanagecorp[.]site navrcorp[.]xyz
cloudcentre[.]site naveocorp[.]tech navermanager[.]online navrpcenter[.]site
cloudcentre[.]space naveocorp[.]website navermanager[.]site navrrcorp[.]site
cloudcentre[.]store naveocorps[.]link navermanagerteam[.]site navrrcorp[.]tech
cloudcentre[.]tech naveoecorp[.]tech navermanageteam[.]com navsceteam[.]site
cloudcentre[.]website naveogains[.]tech navermcorp[.]com navseccenter[.]site
cloudcentre[.]xyz naveolink[.]online navermgr[.]site navseccorp[.]link
corpcenternav[.]site naveologs[.]online navermgr01[.]host navseccorp[.]online
corpnavcenter[.]site naveooccorp[.]online navermgr01[.]site navseccorp[.]site
corpnavsec[.]site naveoocorp[.]link navermgr02[.]site navsecncenter[.]site
corprsecurity[.]tech naveoocorp[.]online naverncorp[.]com navsecnet[.]online
corpseccenter[.]site naveoocorp[.]site navernidcorp[.]com navsecorg[.]tech
corpsecnav[.]site naveoocorp[.]xyz navernidcorp[.]online navsecportal[.]site
corpsecservice[.]site naveoorcorp[.]link navernidcorp[.]site navsecportal[.]tech
havcorp[.]site naveorcorp[.]host navernidlog[.]live navsecportals[.]tech
havecorp[.]link naveorcorp[.]link navernidmail[.]com navsecsite[.]tech
havecorp[.]tech naveorcorp[.]online navernidmail[.]online navsecteam[.]tech
haveecorp[.]site naveorcorp[.]site naverocenter[.]site navsecteam[.]website
haveorcorp[.]tech naveorcorp[.]tech naverocorp[.]link navsecuritycenter[.]site
havercorp[.]site naveorrcorp[.]online naverocorp[.]online navsecuritycenter[.]tech
havercorp[.]tech naveorrcorp[.]tech naverocorp[.]site navsecuritycorp[.]link
havercorps[.]site naveorseccorp[.]link naverocorp[.]tech navsecuritycorp[.]site
havercorpteam[.]site naveorteam[.]site naverocorpteam[.]site navsecurityportal[.]online
haverocorp[.]link naveoscorp[.]link naveronavteam[.]site navsecurityteam[.]tech
havoocorp[.]online naveoteam[.]online naveroocorp[.]link navsecvcorp[.]online
havoocorp[.]tech naveoteam[.]site naveroocorp[.]site navsecvteam[.]site
havorcorp[.]link naver-accounts[.]com naverooteam[.]site navserveportal[.]site
havorcorp[.]online naver-sec[.]net naverooteam[.]tech navservicecenter[.]site
havorcorp[.]site naver-sec[.]org naverorcorp[.]tech navservicescenter[.]online
havorcorp[.]tech naver-security[.]net naverorg[.]site navserviceteam[.]com
havorcorpsv[.]online naver-security[.]org naverorteam[.]link navserviceteam[.]site
mailcontactteam[.]online naver-services[.]com naverorteam[.]online navserviceucenter[.]site
mailcorp[.]site naveradmin[.]online naveroscope[.]tech navservicevcenter[.]site
mailcorpcenter[.]online naveradmin00[.]tech naveroteam[.]online navsite[.]online
mailcorpcenter[.]site naveradmin01[.]link naveroteam[.]tech navsvcorp[.]tech
mailcustomerservice[.]site naveradmin01[.]site naverovocorp[.]site navsvportal[.]tech
mailhelp[.]online naveradmin02[.]site naverovvcorp[.]tech navteam[.]online
mailmanagecorp[.]online naveradmin03[.]site naverrcorp[.]site navteamcorp[.]link
mailmanagecorp[.]site naveradmin04[.]tech naverreda[.]xyz navvccenter[.]online
mailmanageservice[.]com naveradmin05[.]site naverredb[.]xyz navvcorp[.]host
mailmanageteam[.]com naveradmin06[.]online naverredc[.]xyz navvcorp[.]link
mailmanageteam[.]site naveradmin07[.]site naverredd[.]xyz navvcorp[.]online
mailmangecorp[.]us naveradmina[.]tech naverrede[.]xyz navvcorp[.]site
mailportalcenter[.]online naveralert[.]link naverredirect[.]live navvctr[.]link
mailportalcenter[.]site naveranid[.]live naverrteam[.]site navvctr[.]site
mailscropcenter[.]site naverccorp[.]com naversec[.]site navvctr[.]tech
mailsecurity[.]email navercert[.]live naversecurity[.]site navvctvr[.]site
mailservice[.]digital navercert[.]online naversecurityservice[.]online navveoocorp[.]online
mailservice[.]host navercoa[.]store naversecurityteam[.]com navvocorp[.]online
mailservicecenter[.]site navercob[.]store naverservice[.]email navvocorp[.]site
mailservicecenters[.]site navercoc[.]store naverservice[.]host navvrcorp[.]site
mailservicecorp[.]online navercod[.]store naverservice[.]link navvsecurity[.]site
mailservicecorp[.]site navercoe[.]store naverservice[.]online navvtr[.]site
mailservicemanage[.]com navercoma[.]tech naverservice[.]site navvtrr[.]site
mailserviceteam[.]com navercomb[.]tech naverservicecorp[.]com navvtrs[.]site
mailserviceteam[.]email navercomc[.]tech naverservicecorp[.]online navvtrw[.]site
mailserviceteam[.]host navercomd[.]tech naverservicecorp[.]site nevercorp[.]online
mailserviceteam[.]online navercome[.]tech naverserviceteam[.]com nevercorp[.]site
mailserviceteam[.]site navercop[.]link naverserviceteam[.]email nevercorp[.]tech
mailteam[.]site navercop[.]online naverserviceteam[.]site neverrcorp[.]tech
msite[.]host navercorp[.]email navertcorp[.]com nidanaver[.]tech
naswsteam[.]site navercorp[.]live naverteam[.]live nidbnaver[.]tech
nauercorp[.]site navercorp[.]site naverteam[.]site nidcnaver[.]com
nauercorp[.]website navercorpa[.]tech naverteam01[.]site nidcnaver[.]tech
nauercorpa[.]online navercorpa[.]website naverteamcorp[.]com niddnaver[.]tech
nauercorpb[.]online navercorpb[.]online naverteamcorp[.]live nidinaver[.]com
nauercorpc[.]online navercorpb[.]tech naverteamcorp[.]site nidnavcenter[.]link
nauercorpd[.]online navercorpb[.]website navertecha[.]host nidnavcenter[.]online
nauercorpteam[.]website navercorpc[.]online navertechb[.]site nidnavcenter[.]site
nauermanager[.]website navercorpc[.]tech navertechc[.]email nidnavportal[.]site
navaccountcenter[.]online navercorpc[.]website navertechd[.]net nidnavscenter[.]xyz
navadmin[.]site navercorpd[.]online naverteche[.]link nidnavsecurity[.]tech
navadmin01[.]site navercorpd[.]tech navertechf[.]host nidpavsec[.]digital
navcen[.]site navercorpd[.]website navertechg[.]site nidportalnav[.]online
navcenter[.]xyz navercorpe[.]online navertechh[.]online nidseccenter[.]host
navcenterportal[.]site navercorpe[.]tech navertechi[.]link nidseccenter[.]site
navcopcenter[.]tech navercorpe[.]website navertechj[.]host nidsecuritycenter[.]online
navcorp[.]host navercorpf[.]online navertechk[.]site nidsecuritycorp[.]tech
navcorp[.]link navercorpf[.]tech navertechl[.]online noreplya[.]online
navcorp[.]space navercorpf[.]website navertechm[.]link noreplya[.]site
navcorp[.]website navercorpg[.]online navertechn[.]host noreplya[.]space
navcorpacenter[.]site navercorpg[.]tech navertecho[.]site noreplya[.]tech
navcorpcenter[.]site navercorpg[.]website navertechp[.]online noreplya[.]website
navcorpctr[.]online navercorph[.]online navertechq[.]link noreplya[.]xyz
navcorpctr[.]site navercorph[.]tech navertechr[.]host noreplyb[.]online
navcorpmanage[.]site navercorph[.]website navertechs[.]site noreplyb[.]site
navcorpmanager[.]site navercorpi[.]online navertecht[.]online noreplyb[.]space
navcorpmanager[.]website navercorpi[.]tech navertechu[.]link noreplyb[.]store
navcorpportal[.]xyz navercorpj[.]online naverurl[.]xyz noreplyb[.]tech
navcorps[.]site navercorpj[.]tech navervteam[.]site noreplyb[.]website
navcorps[.]website navercorpk[.]online naveservice[.]site noreplyb[.]xyz
navcorpscenter[.]site navercorpk[.]tech navevcorp[.]link novercorp[.]site
navcorpsecurity[.]site navercorpl[.]online navevcorp[.]online nvrcopa[.]link
navcorpserver[.]site navercorpl[.]tech navevcorp[.]site nvrcopb[.]link
navcorpservice[.]site navercorpm[.]online navevrcorp[.]online nvrcopc[.]link
navcorpservice[.]website navercorpmanager[.]online navhelp[.]online nvrcope[.]site
navcorpsite[.]online navercorpn[.]online navmailcenter[.]site nvrcopf[.]site
navcorpssec[.]tech navercorpo[.]online navmailcorp[.]site nvricop[.]online
navcorpsuppot[.]site navercorpp[.]online navmailserver[.]site nvrjcop[.]online
navcorpteam[.]online navercorpq[.]online navmanage[.]online nvscetr[.]site
navcorpteam[.]site navercorpr[.]online navmanager[.]site portalcorpsec[.]site
navcorpteam[.]website navercorps[.]online navmanager[.]website portalcorpteam[.]com
navcpcenter[.]site navercorpservice[.]com navocorp[.]link portalseccorps[.]site
navcrtr[.]online navercorpt[.]online navocorp[.]site portalserver[.]online
navctrv[.]site navercorpteam[.]com navocorp[.]tech scientisttest[.]digital
navcvcorp[.]online navercorpteam[.]online navoercorp[.]host seccenter[.]link
naveacorp[.]tech navercorpu[.]online navoercorp[.]link seccenter[.]online
naveccorp[.]link navercorpv[.]online navoercorp[.]site seccorp[.]link
navecorp[[.]]host navercorpw[[.]]online navoocorp[[.]]link secmanageteam[[.]]site
navecorp[[.]]online navercorpx[[.]]online navoocorp[[.]]online secnavportal[[.]]digital
navecorp[[.]]site navercorpy[[.]]online navoocorp[[.]]site secportal[[.]]digital
navecorp[[.]]website navercorpz[[.]]online navoorcorp[[.]]link secportal[[.]]link
naveeccorp[[.]]tech navercscorp[[.]]com navoorcorp[[.]]online secportalnav[[.]]site
naveecorp[[.]]link naverdoc[[.]]site navoorcorp[[.]]site secportals[[.]]digital
naveecorp[[.]]online naverhost[[.]]live navorcop[[.]]site secportalsnav[[.]]site
naveecorp[[.]]site naverkr[[.]]online navorcorp[[.]]link securityccenter[[.]]site
naveecorp[[.]]tech naverlogn[[.]]live navorcorp[[.]]online securitycenter[[.]]link
naveecorp[[.]]xyz navermail[[.]]site navorcorp[[.]]xyz securitycenter[[.]]space
naveeecorp[[.]]site navermailcorp[[.]]com navorcorpteam[[.]]site securitynavcenter[[.]]site
naveeocorp[[.]]xyz navermailcorp[[.]]host navovcorp[[.]]online securitynavcenter[[.]]tech
naveeoocorp[[.]]link navermailcorp[[.]]online navovcorp[[.]]site securityvcenter[[.]]site
naveeorcorp[[.]]tech navermailcorp[[.]]site navovcorp[[.]]tech sercureteam[[.]]site
naveeoteam[[.]]site navermailmanage[[.]]com navpcenter[[.]]online setcenter[[.]]store
naveercorp[[.]]online navermailservice[[.]]com navpcenter[[.]]site shtlink[[.]]online
Source: Prevailion



































